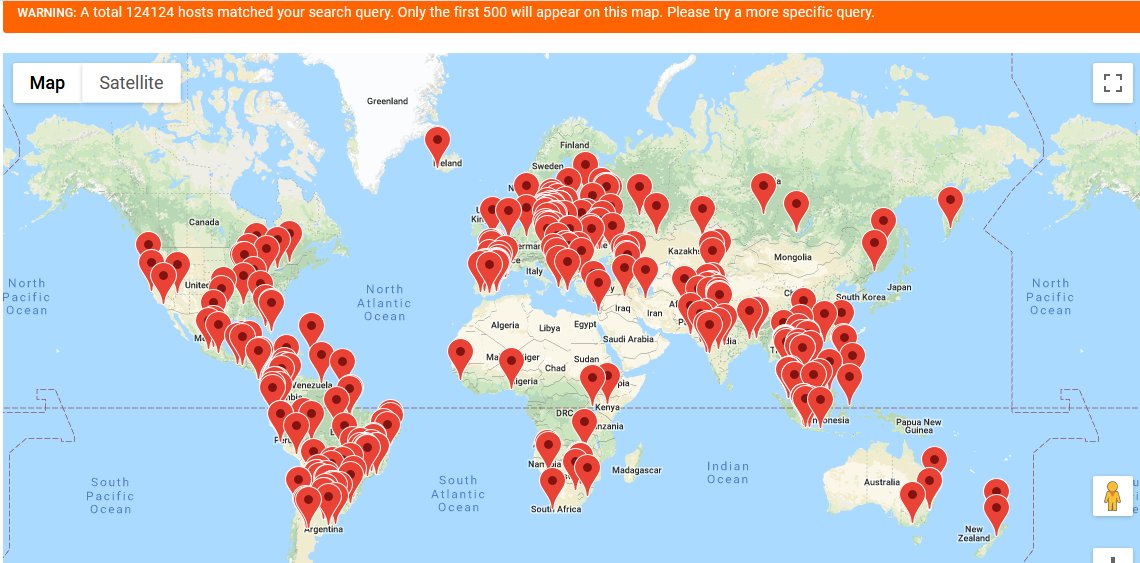
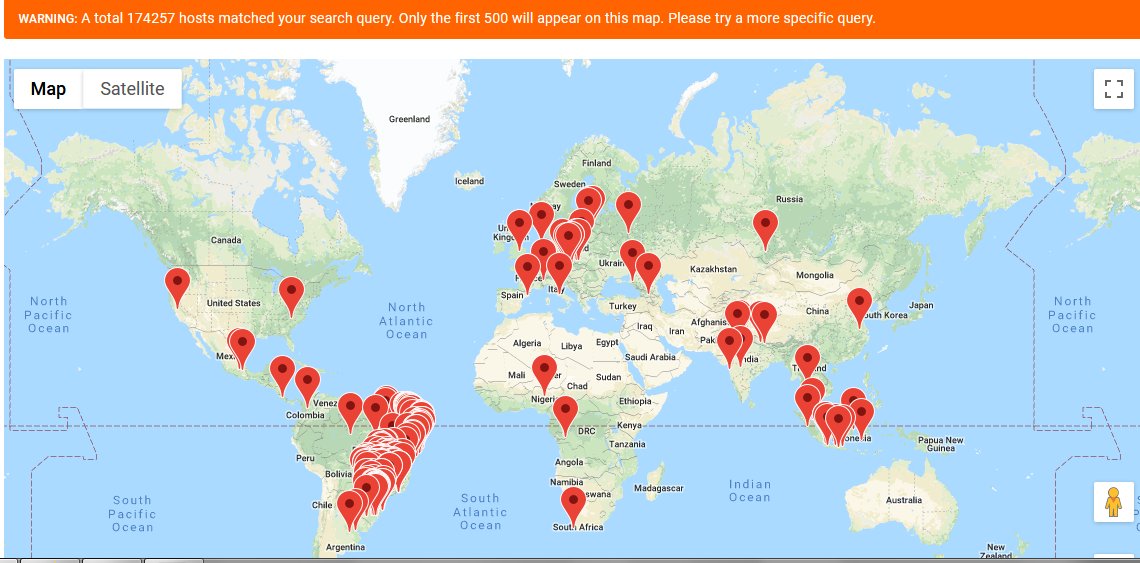
Researchers have discovered over 415,000 routers across the globe have been infected with malware designed to steal their computing power and secretly mine cryptocurrency.
The attack, which is still ongoing, affects MikroTik routers in particular. For the record, the string of crypto-jacking attacks on the brand first began in August, when security experts discovered over 200,000 devices had been infected. The number has more than doubled since then.
While the majority of affected devices was initially concentrated in Brazil, data suggests there are tons of affected devices worldwide.
It is worth pointing out that the number of breached devices might be slightly off, since the data reflects IP addresses known to have been infected with crypto-jacking scripts. Still, the total amount of compromised routers is still pretty high.
“It wouldn’t surprise me if the actual number of actual infected routers in total would be somewhere around 350,000 to 400,000,” security researcher VriesHD told Hard Fork.
Interestingly, while attackers used to favor CoinHive – a mining software for privacy-oriented cryptocurrency Monero (XMR) – the researcher notes there has been a significant shift to other mining software.
“CoinHive, Omine, and CoinImp are the biggest services used,” VriesHD told Hard Fork. “It used to be like 80-90 percent CoinHive, but a big actor has shifted to using Omine in recent months.”
Cryptocurrency mining malware epidemic
The swath of compromised routers was first discovered in August, after researchers reported over 200,000 devices in Brazil had been hijacked to secretly mine cryptocurrency.
By September, the total number of vulnerable devices had increased to a staggering 280,000.
The good thing is that there is something victims can do to protect themselves. Security expert Troy Mursch from Bad Packets Report advises owners of the affected MikroTik devices to immediately download the latest firmware version available for their device.
VriesHD additionally points out that internet service providers (ISPs) can also help battle the spread of malware by forcing over-the-air updates to the routers.
“Users should indeed update their routers, yet the biggest bunch of them are distributed by ISPs to their customers, who often have no idea what to do or how to update the router,” the researcher told Hard Fork. “Often these distributed routers are limited in their rights as well, not allowing users to update the routers themselves.”
“The patch for this specific problem has been out for months and I’ve seen ISPs with thousands of infections disappear from the list,” he added. Unfortunately, it appears tons of ISPs simply won’t take action to mitigate the attacks.
You can find the latest version of RouterOS on MikroTik’s website here.
Get the TNW newsletter
Get the most important tech news in your inbox each week.