A threat group responsible for a series of malware-based espionage attacks in Singapore and Cambodia has been increasingly targeting the Southeast Asian government sector to steal confidential data, new research indicates.
The findings — disclosed by cybersecurity firm Check Point Research — show the operations were carried out over a period of seven months between December 2018 and June 2019, and leveraged spear phishing tricks to lure victims into opening dubious emails that downloaded malware on to their machines.
The hacking group — dubbed Rancor — engaged in clever social engineering tactics by sending malicious documents from real email addresses belonging to government officials to make them seem more legitimate. The targets were government departments, embassies, and government-related entities in Southeast Asia, Check Point said.
Rancor was first documented by Palo Alto Networks’ threat intelligence team Unit 42 last July, who suspected the group of partaking in cyber espionage attacks against Singapore and Cambodia using spear phishing messages containing malicious attachments, such as Microsoft Excel files with embedded macros and HTML applications.
The threat actor’s modus operandi of singling out Southeast Asia also pits it against similar efforts undertaken by Thrip aka Lotus Blossom, an active state-backed espionage group that’s set its sights on communications, geospatial imaging, and defense industries in the region.
A broad, persistent campaign
Rancor’s methodology of employing decoy documents — official letters, press releases, and surveys — to install malware on victims’ machines hasn’t changed in their latest campaign.
But the group has continuously mutated its tactics, techniques, and procedures (TTPs) by using a range of methods, including macros, JavaScript, known vulnerabilities in Microsoft Equation Editor, and even anti-virus programs with sideloaded with malicious libraries, to distribute malware.
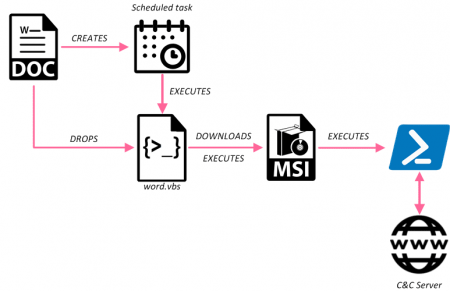
This ‘second stage payload’ then communicated with an attacker-controlled command-and-control (C&C) server to download the ‘final stage payload.’
In all, Check Point observed eight different waves of Rancor activity during the seven months. Tying them all together were overlapping indicators, such as the ones mentioned above and the use of ChangeIP.com for domain resolution.
Who is behind it?
Check Point researchers say the application of Equation Editor exploit (CVE-2018-0798) and the fact their C&C servers were available only between 01:00 and 08:00 UTC time suggest a threat group of Chinese origin.
Earlier this July, California-based cybersecurity firm Anomali Labs reported that multiple Chinese threat actors have “updated their weaponizer to exploit the Microsoft Equation Editor (EE) vulnerability CVE-2018-0798 late 2018.”
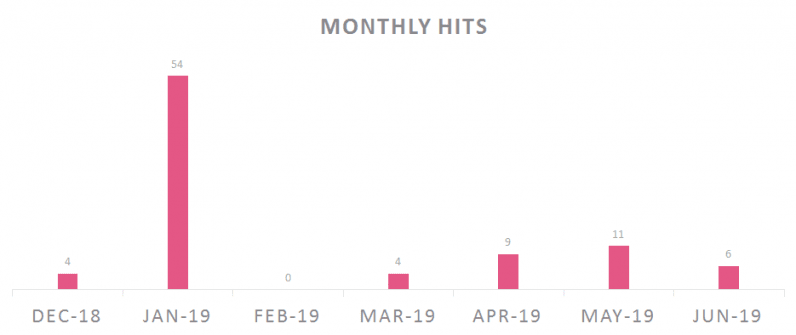
“Chinese roots can also be confirmed by the presence of metadata in Chinese for some of the documents,” Check Point stated, adding “the campaign wasn’t active during February 2019 which is a month of Chinese New Year and Spring Festival, a long holiday in China.”
If anything, the attacks highlight the evolving strategies of the cyberattack machinery assembled by Chinese threat groups to enable large-scale surveillance not only within the country, but also outside it.
Indeed, a report from Crowdstrike released yesterday found state-sponsored hackers working for the Chinese government deployed attacks against the largest number of industry verticals in the first half of 2019, including telecom, gaming, health care, manufacturing, and pharmaceutical sectors.
“We expect the group to continue to evolve, constantly changing their TTPs in the same manner as we observed throughout the campaign, as well as pushing their efforts to bypass security products and avoid attribution,” the researchers concluded.
Get the TNW newsletter
Get the most important tech news in your inbox each week.