
Google appears to have a problem with stopping malicious apps from sneaking into the Play Store.
In what appears to yet another case of malware disguised as a legitimate app, security researchers from Symantec have found a new app that advertised itself as an unofficial version of Telegram messaging app — only to push malicious websites in the background.
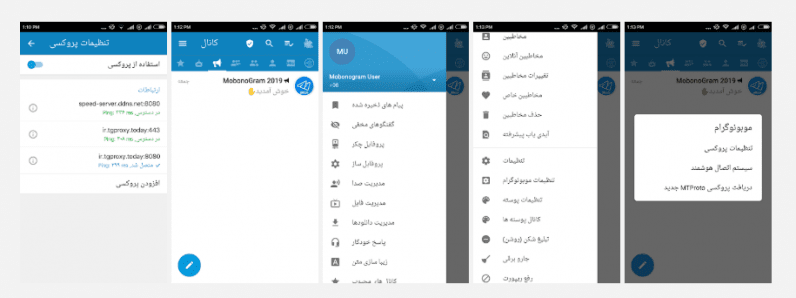
Named MobonoGram 2019, the app used open-source code of the legitimate Telegram app, but was injected with malware before it was published on the Google Play Store.
The malicious code on the infected device was used to spread “Android.Fakeyouwon” malware, and loaded malicious URLs received from a command-and-control (C&C) server.
Google Play as a hotbed for malware
This is not the first time malicious apps have been found on Google’s Play Store. Just in the span of last few months, the search giant has battled an ever-increasing number of malware apps on the app store.
Partly because of the open nature of the platform, it’s an issue that keeps occurring.
From counterfeit apps and games to copycat apps that silently serve adware on infected devices, from spyware to apps pushing ads to generate fraudulent revenue, the gamut of threats on Android devices has vastly expanded in scope.
Google, for its part, has been leveraging Google Play Protect as a means to secure devices from potentially harmful applications.
While the company’s efforts resulted in the removal of over 700,000 apps just last year alone, the cracks in its review process have repeatedly made it possible for bad apps to slip through time and again.
The issues have also been compounded by what appears to a larger problem plaguing the Play Store: bad actors can mask their true intention by obfuscating malicious code behind encryption barriers that make it harder to detect malware.
Despite this steady stream of reports about new adware and other malware found in the Google Play Store, Google has continued to emphasize that the rates are actually very low and that users are much safer only installing apps from Google Play.
But these incidents serve to highlight the limits of Google’s own app filters, raising security concerns about its supposedly vetted store.
How the MobonoGram malware works
Available in English and Farsi, MobonoGram targeted users in countries like Iran and Russia — where the app is officially banned — and the US.
The researchers found that although the app did provide basic messaging functionality, it was also revealed to be secretly running a few services on the device without the user’s consent, as well as loading and browsing an endless stream of malicious websites in the background.
“Mobonogram is an unofficial version of the mainstream Telegram that works without any filter breaker, and has much more features than Telegram and other unofficial versions,” reads the Persian translation of the app’s description.
The malicious app featured a ‘persistence mechanism’ that allowed the app to launch itself every time a device was booted, or immediately after an app was installed or updated.
According to the researchers, this Autostart feature — set to run as a foreground service or restarted automatically after two hours in the event the service is killed — was used to initiate a number of additional services without user’s knowledge.
Once the app was up and running, it accessed a set of designated C&C servers to receive malicious URLs, a browser user agent to mask the source of the request, and three JavaScript codes.
The researchers observed that the JavaScript codes were designed to commit click fraud and generate counterfeit ad revenues.
“The clicking events were not seen in action, even though all JavaScript codes were indeed loaded. Nonetheless, we cannot entirely dismiss the possibility of the malware being used for click fraud or some other malicious end,” the researchers noted.
Apart from this, Symantec researchers also found that there were some URLs which caused an infinite loop of requests to a malicious website. Such activity can exhaust the device’s battery while also potentially causing it to crash.
Based on telemetry data gathered between January and May 2019, the cybersecurity firm said it detected and blocked 1,235 infections related to the Android.Fakeyouwon malware family, with the highest number of infections located in the US, Iran, India, and the UAE.
It is not immediately clear how long MobonoGram 2019 was available. But the app racked up more than 100,000 downloads, and the developer — RamKal Developers — pushed at least five updates before Google removed it from the Play store. The same developer also published a second app called Whatsgram that exhibited similar malicious behavior.
However, a simple search shows that the apps continue to be available on unofficial third-party app repositories.
For now, the same rule of caution applies. It’s always best to keep your phone’s software up to date, refrain from downloading apps from unknown sources, and be cautious of the permissions requested by apps.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





