
Researchers from cybersecurity vendor Check Point have discovered a new kind of mobile malware targeting Android devices.
Dubbed Agent Smith, the malware has been found to exploit known weaknesses in the Android operating system to replace legitimate installed apps on the device with malicious versions without requiring users’ intervention.
Based on their research, Agent Smith has been found to leverage its broad access privileges to display fraudulent ads and profit off them.
Primarily targeting devices in India, and other Asian countries like Pakistan and Bangladesh, the malware has surrepitiously affected around 25 million unique devices, with each victim suffering “roughly 112 swaps of innocent applications.”
The infections were mainly reported on devices running Android 5 and 6, with most infections lasting for a period of at least two months.
In its present form, Agent Smith is being exploited for financial gain by serving malicious advertisements. But given its capabilities to impersonate popular Android apps, the researchers caution that “there are endless possibilities for this sort of malware to harm a user’s device.”
How does Agent Smith work?
Check Point researchers said they encountered the malware in early 2019 after observing a surge of Android malware attack attempts against users in India. Complicating the matter is its stealthy infection methodology, which makes it hard to detect until a device has been compromised.
The attack leverages a three-stage infection chain in order to build a botnet of devices that are controlled from a command-and-control (C&C) server to issue malicious commands.
- The entry point is a dropper app, which the victim installs on an Android device voluntarily. These are usually repackaged versions of legitimate apps like Temple Run with additional code.
- The dropper app automatically installs a malware app — essentially an Android package (.APK) file — whose icon remains hidden from the home screen launcher. They also escape detection by disguising themselves as Google-related updaters.
- The core malware APK extracts the list of installed apps on the device, and scans it against a “prey list” of apps — either hard-coded or issued from the C&C server. If it finds a match, it extracts the base APK file of the target app, injects the APK with malicious ad modules, and installs the new ‘copycat’ version of the app as if it were a regular app update.
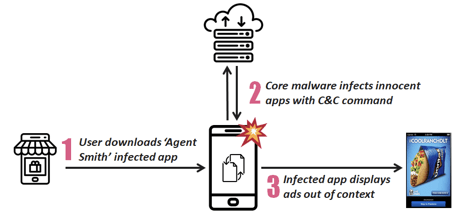
The additional code in the dropper app — called a loader — is mainly meant to extract and load a “core” module, which communicates with the C&C server to fetch the list of Android apps to scan the device for.
It includes some of the most popular apps used in India like WhatsApp, SHAREit, MX Player, JioTV, Flipkart, Truecaller, Dailyhunt, Hotstar (a video streaming service operated by Star India, a subsidiary of Walt Disney), and more.
Upon finding the target app on the Android device, the “core” module then takes advantage of the known Janus vulnerability — previously reported by Belgium-based security firm GuardSquare in 2017 — to replace the legitimate application with an infected version, but without altering the app’s signature.
Once the infected app has been installed on the device, a “boot” module in the app extracts and executes the malicious payload. But to prevent a real update from the developer overwriting all the changes done to the app, a “patch” module cleverly disables automatic updates for the copycat application.
With everything in place, the malicious payload now requests the C&C server to serve malware-ridden ads. The C&C servers, in turn, helped Check Point researchers narrow down the domains used by the threat actor for delivering prey list and rogue ads to the infected devices.
Who is the threat actor?
According to the researchers, Agent Smith has been around since January 2016. Hackers began to use 9Apps as a distribution channel for adware by building an array of dropper apps.
9Apps is a third-party Android app store backed by UCWeb, which Alibaba Group acquired in 2014. One of its most popular products is UC Browser — a web browser app with a strong presence in markets like China, India, and Indonesia.
The malware campaign, which began as a series of garden-variety adware blasts, intensified during the later half of 2018, before dropping significantly earlier this year.
In the recent months, the researchers also uncovered 11 infected apps on the Google Play Store that contained malicious yet dormant components used in Agent Smith, suggesting the threat actor is beginning to use Google’s own app distribution platform to spread adware. Google has since taken down the apps after Check Point reported their findings.
Armed with this information, the researchers connected the Agent Smith campaign to a Chinese internet company located in Guangzhou. The tech firm, they discovered, operated an actual front-end business to help Chinese Android developers publish and promote their apps on overseas platforms.
But Check Point said it found ads for job roles that related to the Agent Smith malware infrastructure and had no connection to the company’s real business.
They also revealed that the “Agent Smith prey list does not only have popular yet Janus vulnerable apps to ensure high proliferation, but also contain competitor apps of actor’s legitimate business arm to suppress competition.”
The Impact
“Agent Smith droppers show a very greedy infection tactic,” Check Point noted. “It’s not enough for this malware family to swap just one innocent application with an infected double. It does so for each and every app on the device as long as the package names are on its prey list.”
The proliferation of the malware also hinged on the operators inundating 9Apps with hundreds of dropper apps — mostly variants of photo utility, games, or adult entertainment related apps.
Agent Smith specifically targeted users from India, but researchers also found successful penetration in Saudi Arabia, the UK, and the US. India alone accounts for over 15 million infected Android devices.
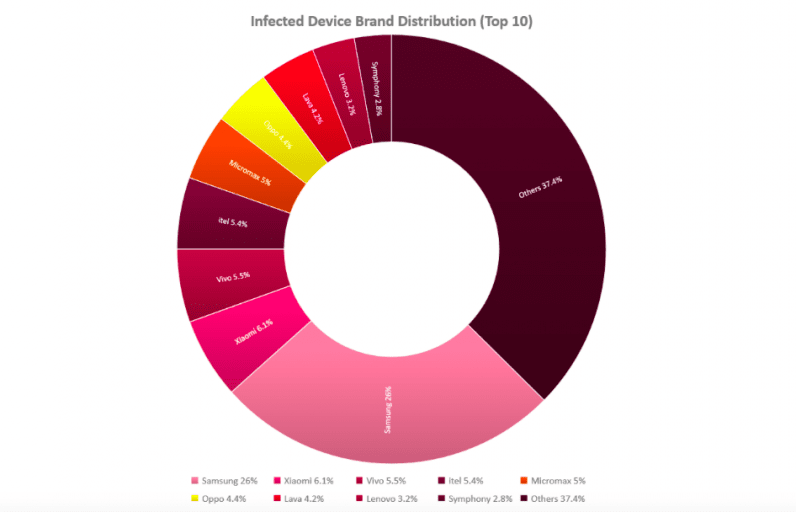
In addition, the research found that the top 5 most infectious droppers alone have been downloaded more than 7.8 million times, with Samsung and Xiaomi devices accounting for the most infections in India.
What’s the takeaway?
This is not the first time an attacker has leveraged third-party app distribution mechanisms to infect devices with malware. Besides the fact that a patched vulnerability is being exploited, it’s concerning that the malware operators are laying the groundwork for a distribution campaign through the official Android app store.
“AOSP patched the Janus vulnerability since [Android] version 7 by introducing APK Signature Scheme V2. However, in order to block Janus abuse, app developers need to sign their apps with the new scheme so that Android framework security component could conduct integrity checks with enhanced features,” the researchers said.
It underscores how devices running older versions of Android can be susceptible to a variety of attacks. But it also highlights the need for collaborative action from system developers, device manufacturers, app developers, and users, so that vulnerability fixes are patched, distributed, adopted and installed in time.
“Although the actor behind ‘Agent Smith’ decided to make their illegally acquired profit by exploiting the use of ads, another actor could easily take a more intrusive and harmful route. Today this malware shows unwanted ads, tomorrow it could steal sensitive information; from private messages to banking credentials and much more,” the researchers concluded.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




