
Remember Tinder Social – the group meeting feature that got the popular dating app in trouble for outing its users to their Facebook friends? It turns out that, in addition to this, Social had another glaring privacy issue that made it possible for Tinder users to track their Facebook friends – and see their exact location.
To demonstrate how intrusive the group meeting feature can be, researchers from cybersecurity firm Detectify developed a creepy Chrome plugin that enabled them to use their Tinder account to triangulate the precise location of their Facebook friends.
As the security experts explain in a blog post, they exploited a well-known privacy vulnerability that allows to export your Facebook friends’ Tinder IDs. The next step was to mark this data onto one big map and automate it to continually update users’ location with data from the app.
Here is how this looked:
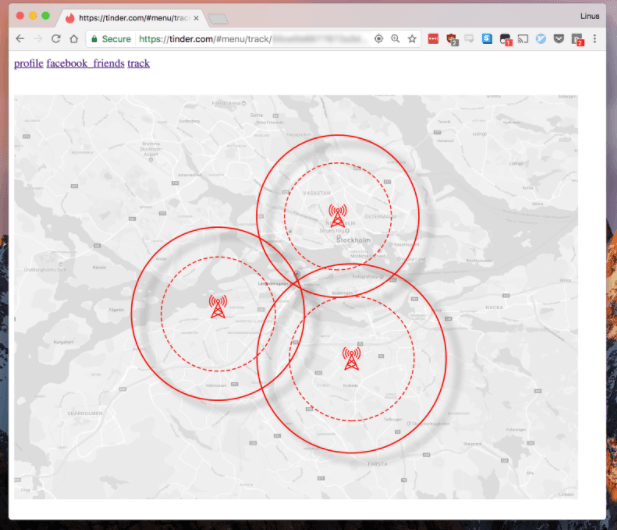
While Tinder has no official API, Detectify resorted to popular sniffing tool Burp Suite in order to detect and hijack the necessary traffic data. This made it possible for the experts to retrieve a list of all of their Facebook friends using Social and also see exactly how far they were from them.
Detectify also worked out how to abuse Tinder to send latitude and longitude coordinates to arbitrarily change their location.
With all this information at hand, the researchers were able to develop an algorithm that automatically triangulated the location of their friends.
In all fairness, Detectify is hardly the first company to exploit this setup.
In fact, Tinder previously addressed this issue and argued it is more of a feature, than a bug. The company later made Social an opt-in feature to further protect the privacy of its users, but it clarified that anybody who activates Social will be vulnerable to this loophole. Since then, it has killed off Social altogether.
Still though, numerous opportunists have already used this workaround to cash in by secretly outing Tinder users.
As Detectify puts it, user location needs to be publicly available for Tinder to work: “They could have made our research harder, but they could not have stopped it.”
So ultimately it is up to you to decide on which side of the trade-off you want to be: Is a date more important to you than your privacy?
Get the TNW newsletter
Get the most important tech news in your inbox each week.





