A Facebook user by the name of Philippe Harewood on Wednesday spotted a rather interesting scam that leverages Facebook, Tumblr, and Google Chrome to spy on its victims. The privacy-violating campaign was later detailed further by security firm Webroot.
The whole campaign is based on the hopes that Facebook users want to change the theme of the site to another color, such as red. It can be of course adjusted to target other users as well.
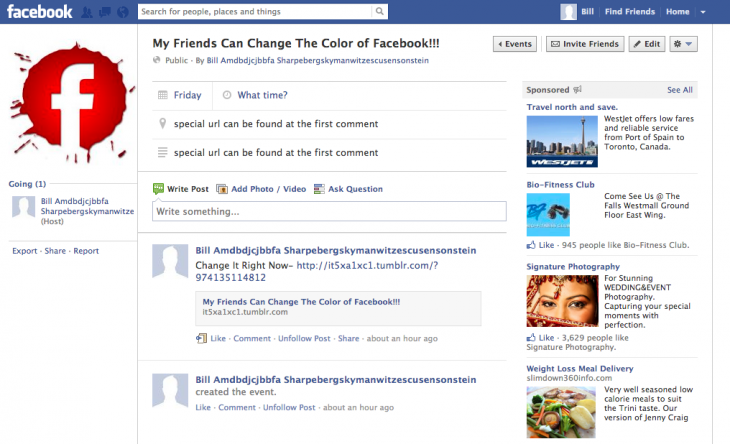
Harewood explains how it works. A Facebook user is invited to a fake event on the social network. He or she then clicks on a Tumblr link, which redirects to another page (typically hosted on Amazon Web Services) that prompts the user to install a Chrome extension.
The extension then executes a JavaScript file (also hosted on Amazon) when it detects an open Facebook page, which creates a new Tumblr page and a new Facebook event. Finally, the script invites all your friends and pushes the Tumblr link, and the scam starts again.
As Webroot notes, the real danger is the malicious Chrome extension, which once installed, has access to all your data on all websites, as well as access to your tabs and browsing history. The Facebook event and Tumblr links are merely used to trick users into thinking the extension will do what they want; all the URLs in question look legitimate since they are hosted on the aforementioned sites.
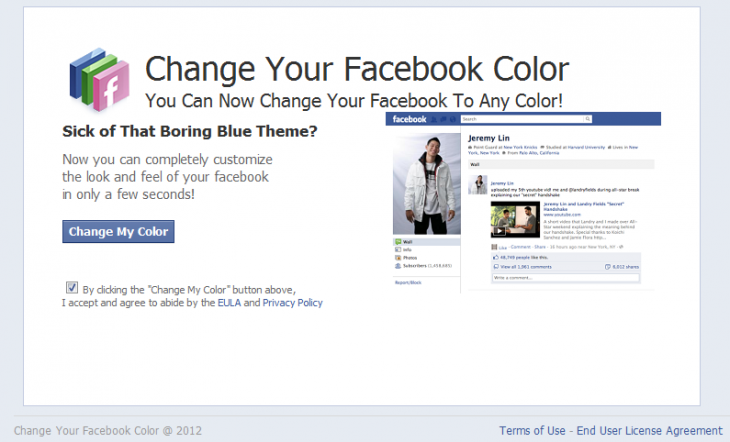
Here’s the page that entices users into changing their Facebook color theme:
As you can see, there’s even an accompanying EULA and privacy policy, in an attempt to further improve the scam’s legitimacy. If the user chooses not to accept the agreements, the cybercriminals behind the campaign try to monetize the hijacked Facebook traffic by asking the victims to participate in surveys full of ads to generate revenue for them anyway.
Protecting yourself is very easy: don’t click on random links on Facebook, even if they are hosted on Tumblr. Being invited to a Facebook even does not suddenly make them safe.
Image credit: Chris Chidsey
Get the TNW newsletter
Get the most important tech news in your inbox each week.