
Researchers at Zscaler ThreatLabZ have identified a new remote-access trojan (RAT) called Saefko, which retrieves Chrome browser history in a search for cryptocurrency-related activity
The RAT, written in .NET and available for sale on the dark web, also looks for information relating to other activities involving credit cards, business, social media, gaming, and online shopping.
For context, a RAT is a type of malware that features a backdoor, enabling perpetrators to remotely control a device.
By remotely controlling a device, the intruder is able to surreptitiously monitor user behavior, access confidential information, activate a webcam, take screenshots, and format drives, among other things.
Once the RAT infects the device it stays in the background, activating and executing every time the person logs in.
The list of different cryptocurrency categories Saefko searches for include:
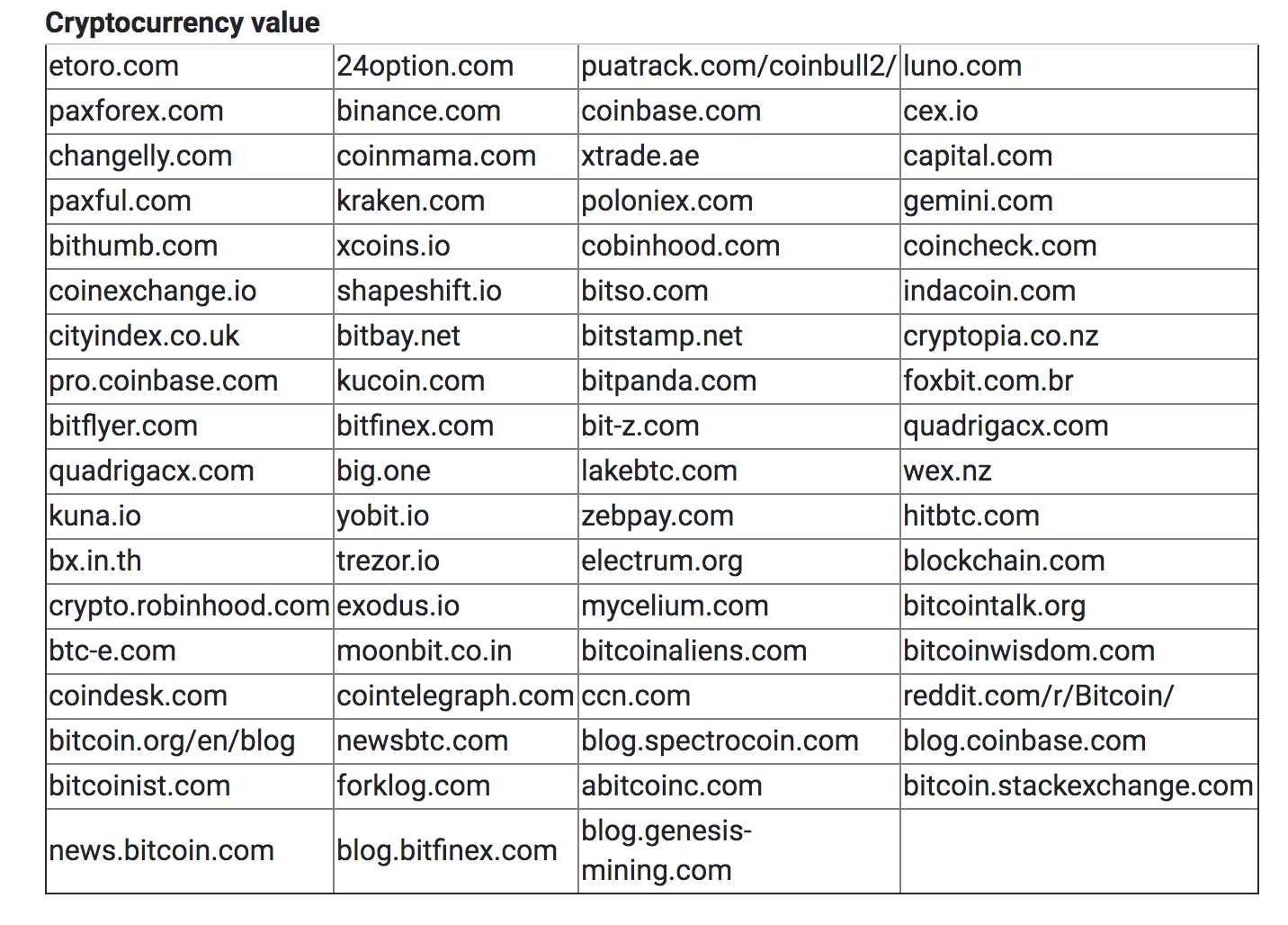
When it comes to protecting yourself against Saefko, the usual advice applies.
Don’t download any programs or open any attachments from an untrusted source. Block unused ports, switch off unused services, and monitor all outgoing traffic.
And remember that attackers are often cautious, preventing the malware from doing too much at once, which would inevitably slow down a device and possibly attract the your attention.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





