In case you’ve missed this morning’s debacle on Twitter (and it’s not likely that you have), it appears that there was a breakdown in the system when it comes to Twitter’s t.co link shortening.
If you remember, a couple of months ago, we talked in depth about how the t.co system would work. It was Twitter’s goal, at the time, to provide a “sanitized” system of link shortening on the site. In Twitter’s eyes, the goal was two-fold:
- Provide safe linking on Twitter
- Add to the Promoted Tweets platform
The problem, of course, comes into play when things don’t work out quite as expected. According to an eagle-eyed TNW reader, the first link to display the vulnerability was, in fact, a t.co link:
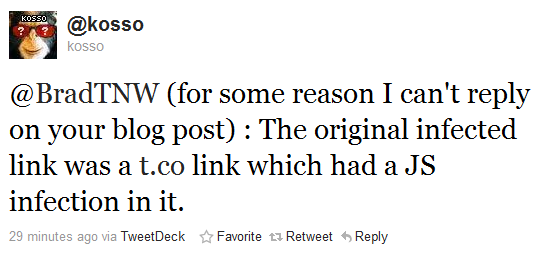
It is typically seen as best practice to search out vulnerabilities in code before releasing it. No doubt, Twitter spent considerable time doing just that. It is the simplicity of execution in today’s threat, however, that really strikes attention.
Within minutes of the first link going live, it was spreading by the thousands per second. As it continued, the linked items mutated to create blank tweets, direct messages and even block out sections of the users’ screens. While we didn’t see any reports of truly malicious code, the problems that did arise were certainly annoying enough to warrant questioning.
So with that, I’ll leave you to the questioning in our comments. Do today’s events change your perception of Twitter’s t.co service, or are they just growing pains of a new service?
Get the TNW newsletter
Get the most important tech news in your inbox each week.