![Twitter security flaw allows third-party sites to open on mouseover [Update: Fixed]](https://img-cdn.tnwcdn.com/image?fit=1280%2C720&url=https%3A%2F%2Fcdn0.tnwcdn.com%2Fwp-content%2Fblogs.dir%2F1%2Ffiles%2F2010%2F09%2FPicture-2.png&signature=6108cc7f1af0e7772099471dff50f305)
Updates at bottom of post – Twitter’s official response
There is apparently a security flaw in the Twitter code that is allowing users to have third-party websites open in your browser, and all you have to do is mouse over a link for it to happen.
The flaw, as reported by Internet security company Sophos, appears to be somewhat innocuous for now but holds some pretty nasty potential as it could allow Twitter users to be redirected to other sites that contain less-than-honorable code.
While that threat certainly appears, another one has reared its ugly head as well. The newest variation of the code attempts, on mouseover, to have you continue to spread it via your Twitter status update.
The code, which could also be used to display multi-colored “rainbow tweets” or even a blank page, produces an effect like this: 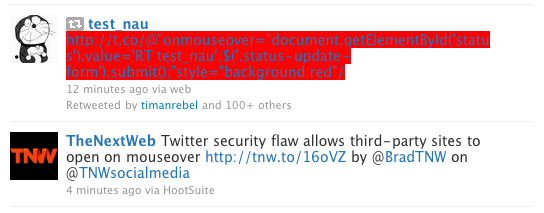
—————————
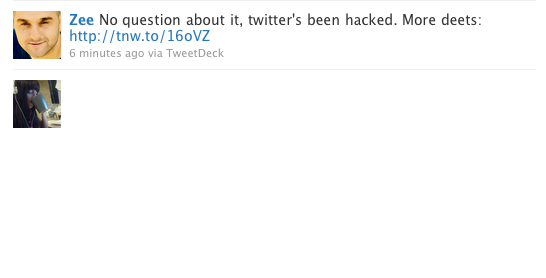
We’ve contacted Twitter, as well as a security expert and we’re waiting for any further information. For now, it is worth noting that you should avoid clicking or mousing over any link that has the “onmouseover” command, or any link that is disguised by colors.
Of course, it is also advisable that you use a third-party Twitter client such as TweetDeck or Seesmic, in the mean time. The clients are not succeptable to the “onmouseover” events, and should prove to be a safe solution. If you happen to be one of the lucky New Twitter users, you should also be safe (thanks @Boris).
Another workaround is to head to the mobile version of the Twitter site at http://mobile.twitter.com as the links do not appear to be functional via that version. You should be able to safely browse Twitter, and also delete any inadvertent tweets from your account via the mobile interface, according to CenterNetworks.
Our thanks to Sam at TwitterCounter for the images and additional information.
Update: According to some users, the latest chunk of code not only attempts to hijack your stream, but also apparently is hijacking the account as a whole, even if you haven’t moused over a link. One users has noted the following:
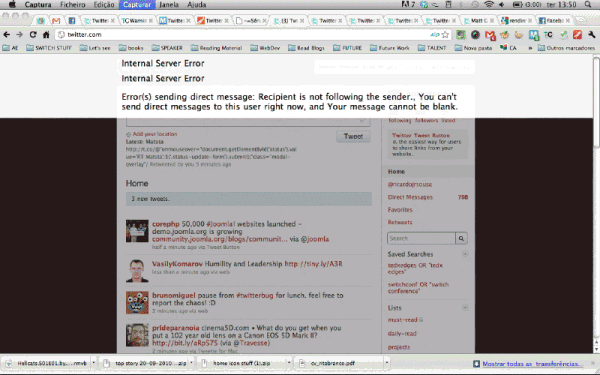
We’ve also gotten a better explanation of how the attack is happening, again via Sam from TwitterCounter:
It seems to stem from the short url http://t.co/@. Whenever a URL is included into the tweet, Twitter renders the HTML for it (eg. https://thenextweb.com would render as <a href=”https://thenextweb.com“>https://thenextweb.com</a>). What this hack does, it abuses this rendering by closing the href attribute early sohttp://t.co/@“onmouseover=”etc”/ would render as <a href=”http://t.co/@” onmouseover=”etc”>http://t.co/@“onmouseover=”etc”/</a>. That first double quote in the malicious URL closes the href attribute and allows for javascript events to be included afterwards.
Georg Wicherski from Kaspersky Labs adds to Sam’s explanation:
Apparently, there is an actively exploiteded XSS vulnerability on Twitter. From my first preliminary analysis, you’ll have to hover over a link to activate it and so far I have just seen some proof of concepts from people I follow. However, this vulnerability looks at least semi-wormable, so better turn JavaScript off on Twitter for now!
Update (14:05 CEST): This vulnerability is confirmed to be exploitable with no user interaction automatically. Turn off JavaScript for Twitter!
Update 2 (14:13 CEST): It is possible to load secondary JavaScript from an external URL with no user interaction, which makes this definitely wormable and dangerous.
Update 3 (14:24 CEST): Worm code for this vulnerability has been posted on IRC, making the rounds.
Update 4 (14:36 CEST): Worm is live already…
Update 5 (14:59 CEST): It appears Twitter now properly escapes links, that specific vulnerability seems closed.
We’ve just heard from @cpen at Twitter, and she points us to the Twitter Status blog which states that the XSS vulnerability is now being patched.
10:30 AM PDT – Twitter has put a statement on the Twitter Blog that describes the incident, as well as its response.
Get the TNW newsletter
Get the most important tech news in your inbox each week.