Using the Web to support the social process has significantly increased in the last decade with the explosion of social network services like Facebook, LinkedIn, Twitter and online dating sites.
While having an online identity has certain strengths in providing easy communication by minimizing the need for a physical presence, the nature of online identities also has its flaws. It makes it easy for one to fake elements of one’s online identity, create a false identity or steal another person’s identity altogether.
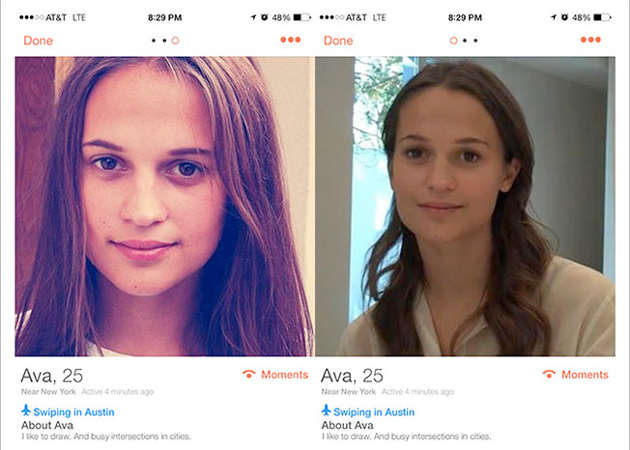
Creating a completely fake online identity
The existence of a temporary virtual wall before one meets face-to- face also makes it easy to engage in fraud and spam online. People can be duped into wiring large sums of money online to a “friend” or “lover” with whom they’ve only virtually communicated with.
Most recently, a woman claimed to have wired $1.4 million to her online lover, whom she’d never met before.
Email is a popular and relatively traditional form of online identity, but they are very easy to fake since there are no identity verification processes required before creating a free email account with popular services like Gmail, Yahoo or Outlook. It is also fairly easy to create email accounts in bulk for spamming purposes.
A single user is able to create hundreds of free email accounts in a short span of time. These can then be used to verify multiple accounts in social applications which are used for spam or fraud.
Dodgy marketing campaigns using fake user accounts can also disrupt the user experience on an app or social network. During SXSW 2015, Ex Machina created a fake profile on Tinder with a bot, using a picture of the film’s Swedish star to promote the movie to other Tinder users that messaged the fake profile.
While this can be a great marketing campaign for the brand, this could potentially turn off people who are genuinely looking to find a human match on the app.
The Ex Machina experiment also proves that Tinder is relatively easy to fill with spam bots. Other social networking sites such as Twitter and Facebook have also had their fair share of spam bot problems, as these services make it easy to create new accounts without any identity verification required. While you can link Facebook to a phone number, it is not a requirement in order to gain permission to create a new profile.
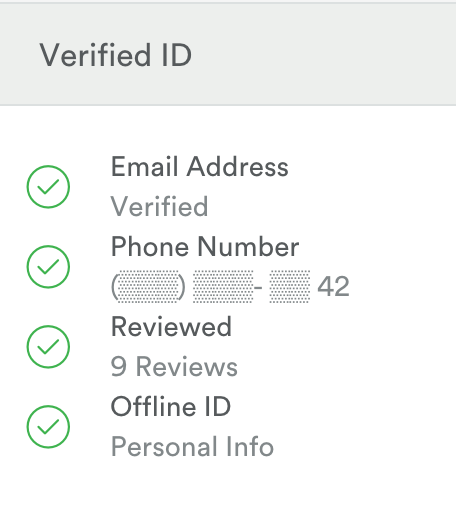 Other services, such as Airbnb, award users with a Verified ID badge if they are able to provide government-issued ID, email address, phone number and a link to an active social network profile.
Other services, such as Airbnb, award users with a Verified ID badge if they are able to provide government-issued ID, email address, phone number and a link to an active social network profile.
While this is extensive and important, not all users may be comfortable sharing their passport or state ID with Internet services.
In favoring ease of onboarding, social apps and services risk identity security as they do not heavily promote verifying profiles with tangible information.
Stealing an online identity
Stealing another person’s identity is relatively simple. Phishing attempts, where one is sent a fraudulent email to harness personal information, is no longer needed because password attacks are becoming automated.
Attackers find out one’s username/password combination by using an ‘account checker’ tool. This tool tests different username and password combinations on e-commerce sites and steal the account holder’s names, addresses and payment card information if the combination works.
In effect, by having the right username and password combination, fraudsters can steal the person’s online identity. This method was recently brought to light when a man with the Twitter handle @n profiled his virtual identify theft early last year.
One can also manually steal another’s identity by answering account recovery questions during the password reset process. In 2008, Sarah Palin’s Yahoo email was hacked with a reset password request since all the answers to her account recovery questions were easily searchable online or available through her social media accounts.
With the many cases cited above, it’s clear that email or social media accounts are not a valid source of user identity. Unfortunately, many apps, e.g. dating or networking, require some form of genuine identity verification that ideally doesn’t involve a lengthy or expensive process. This is where phone numbers can come in.
Phones as unique user identifier
Phone numbers are ubiquitous and people generally retain the same number for a long period of time, e.g. a decade or more. This means most applications will still be able to use this method for the majority if not all of their users.
With mobile phone adoption rate on the rise worldwide, companies can easily communicate with their users via low-cost methods like SMS, which does not require an internet connection to process.
Unlike social networks, phone numbers are not easy to fake since one has to obtain a physical SIM card or a real phone number issued by a carrier. Virtual numbers, numbers without a directly associated telephone line, can be determined by an application and these can be blocked to reduce spam or fraud.
In contrast to email, getting a new phone number is not as easy as signing up. Carriers often require personal information – such as identification and credit score – to open an account, while others may provide a physical SIM card alongside. This analog nature complicates the process of stealing one’s phone number identity as thieves would have to steal a person’s SIM card at the very least.
Furthermore, in the event that one successfully steals a person’s phone, the carrier can stop the account’s service upon report of a stolen number or phone. Therefore, the stolen number identity will be short lived.
There are already several communication applications such as WhatsApp and Viber which use the phone number as the user identity. Although WhatsApp recently rolled out a Web version, it still has to be installed on a phone, then linked to a phone number.
The reach and security of a phone number provides a genuine advantage over email or social media, making it the ultimate user identity.
Read next: How to Increase App Security Through Mobile Phone Authentication
Get the TNW newsletter
Get the most important tech news in your inbox each week.