 The chances are you already know about the Gawker Media security breach, a network-wide attack that compromised over a million registered accounts across Gawker’s web properties. Internal memos were accessed, sensitive usernames and passwords uncovered and site modifications made.
The chances are you already know about the Gawker Media security breach, a network-wide attack that compromised over a million registered accounts across Gawker’s web properties. Internal memos were accessed, sensitive usernames and passwords uncovered and site modifications made.
As part of our ongoing coverage, we now bring you an exclusive interview with the group behind the attacks, Gnosis.
We had questions and Gnosis had answers that we are sure you’ll want to see.
We spoke to three members of Gnosis, they will be identified as N, I and T.
Who/what is Gnosis?
I: We are a small group, who have varying talents in computer technology, each member of the team is hand picked based on their skills and personality. We generally just chat and code together as a tight knit group and work on projects in our free time.
So it’s an invite only group?
I: It is yes.
That currently has three members?
N: No, there are currently 13 members, with three “others”.
Do you have a leader?
I: Ha, we were expecting that one. We dont believe in having a leader of the group, everyone is as equal as the next.
Certain members of the media have mentioned you were associated with 4chan/Anonymous, despite you strictly implying you were not. Can you explain your connection to 4chan?
I: We formed as a small group interested in learning about technology. Ever since, we have become a collective who work together on projects.
N: As for 4chan, we are not directly connected, no. But 4chan’s influence on the net is large and several of our members visit the site. We don’t directly agree with some of 4chans tactics, or rather “anon’s” tactics.
We believe that ddosing sites won’t help their cause and will only generate negative press and I personally see in the media a lot of acts being simply put under the umbrella of “4chan” or “anonymous”. We would have not wanted this to be lumped with such acts as DDOS’ing Amazon or Mastercard.
Negative press?
N: Well the saying goes that any press is good press.
Did you believe compromising Gawker and publishing innocent users accounts would bring positive press?
N: Nope
I: No, we did not.
N: Which is why we did not lump it together with Wikileaks, or any other “aim”. We simply released it as it was.
Would you say the timing of your release could have been better as to not be “lumped” in with Anonymous?
I: The timing for the release was quite a rush to be honest, while we will not disclose why this was. We will say that, however rushed it was, we are happy with the release. It is always going to be lumped with anonymous, no matter what it is.
Well, at least by some people.
Why did you choose to deface Gizmodo’s Twitter account above all others and why post #wikileaks supporting messages? Did you believe Giz was the most visible [Gawker] property?
N: I was the one who defaced the Twitter [account]. Gizmodo was very visible and while the tweets were up for only 5 mins at max they caused quite a big stir.
[In answer to the first question] I believe in Wikileaks and their cause, so I thought the first post would be “WIKILEAKS”. I then started to post about the upcoming release and I was actually just writing a tweet about the source code release date when they got control back.
So they [Gawker] acted almost instantly?
N: Nearly instantly, within 5 mins. They removed the tweets and changed the password.
What motivated you to hack Gawker? Did you have something against Denton, Gawker or the its writers? Or all of them?
T: We were motivated by the sheer arrogance of the Gawker group of bloggers. We are a technologically minded group of people, and we enjoy a challenge.
When we got in, we were shocked by the apparent lack of any layers of security, setting off a chain, leading to compromise.
N: As for the question about if this is a thing against its writers, I personally have nothing against them, they have built what they call an “empire” and I respect that. So no, it is nothing personal.
So this had nothing to do with the 4chan/Gawker spat many months ago? Are you saying it’s unrelated?
N: Completely.
I [wrongly] assumed the two incidents were connected?
N: We read about these as they happened and thought nothing of them but a member brought it up and we decided to see if we could get inside Gawker but the large gap was because we didn’t really care at the time.
But after a quick pentest we discovered how truly arrogant they were, which makes more sense if you know the levels of security within Gawker.
How long did it take to compromise Gawker? Can you comment on how you gained access?
I: Sorry but we do not wish to provide a timeframe but, if it helps, it didnt take us long. The site is a set of components, and we tested and evaluated each ones integrity.
N: We had frontpage access quite quickly though, and like dominos the other systems fell into place.
Did you employ XSS vulnerabilities or kernel vulnerabilities?
N: We cannot comment, I am sorry. Though vulnerabilities were involved at several stages, in several components, we cannot specify which and what type.
Can you comment on the stages in which you gained access to Gawkers web properties?
N: We can’t comment on the stages but we did access the Email, the issue tracker, several web servers, Campfire, SVN as well as some other old internal things that were not used anymore. There are others, who’s names do not spring to mind. They should all be in the README.txt [a file released in the torrent data].
What do you say to the people who had their details compromised? Aren’t they just unwitting pawns in the crossfire?
I: We apologize that you were caught in the crossfire of this attack, if you have a sufficiently good password over 8 characters then you are most likely not at risk, anyone could have did what we did, it was wide open for everyone to exploit, we just got there first.
Why did you release user data?
I: TBH, they would rather it was us, than some Russian spammer who would sell their databases, or use them for more malicious uses.
T: Release is the safest path, as it allows lessons to be learned.
Can’t you argue that a spammer would be able to use this data anyway?
N: A spammer could easily use this, but the true value lies with the passwords. Someone clever could have extracted this information and then bruteforced the hashes to get the passwords, and slowly and maliciously exploited them. Now they are out in the open the people effected will be able to change.
In the short term yes, they could be used maliciously, but long term we would hope that the majority would change their passwords.
We don’t want to condone what we did as right, because it will cause damage to the people caught in the “crossfire” but it should be a reminder to everyone that security does matter and that big sites take unacceptable liberties with users’ data.
T: Additionally, we let users know their data was compromised, as we didnt look for other tracks, but it doesn’t mean to say they were not there.
As we have repeated, _anyone_ could have gotten their hands on this info.
N: (Anyone with some skill that is)
T: Indeed.
Then what is your core ideology?
N: Our ideology is to learn. As knowledge is power. We like to explore and work on interesting projects, some of which we believe have not been attempted in the past.
Now you have compromised Gawker, will you seek to attack anyone else?
N: Well, we have a few pokers in the fire, but nothing we can discuss. We will however re-visit Gawker sometime in the future and see if they have improved their security and fixed the numerous holes. I hope they will, they mentioned they were hiring IT experts, whatever that means.
So is that to say you will be looking to announce more attacks soon?
I: No, we will not be conducting attacks like we have this time, we are not a malicious group intentionally. We will just revisit Gawker at some point to assess their security, and see if this drop has helped them improve security.
Are you worried whether Gawker might have contacted the authorities following this attack?
I: We are not worried about this, as we beleive being broken wide open will help them to secure their site. We have not been informed in any way of Gawkers intentions to call the authorities or not.
Would you conduct strict security testing of other sites if they were found to be operating similar to Gawker? Put simply, who would be fair game?
N: The group is fairly decentralized, there are no orders per say, if a member wants to investigate (or a group of members such as with Gawker) then he or she can do, its at their discretion. We try to keep our ears open, we sometimes hear that a big site is vulnerable and we take a look and everyone is fair game on the internet, in my opinion.
What would you say you have gained from all this?
N: We have gained an insight into how a large website works and is run and what technologies they use, it was very interesting. However I hope Gawker is the exception rather than the rule.
Is there anything else you wish to point out for me, our readers, members of the press and/or public?
N: Uhh, well from my point of view it has been a fun ride, and good luck with the story.
I: I agree, Good luck with the story.
T: I’d just like to point out that the disclosure of source should be taking a lot more of the stage. Other than that, it’s been fun.
T, can you elaborate?
T: I feel that the fact that _full_ source has been released, Gawker may as well go opensource, which would be _very_ interesting, and would love to see how that plays out for Gawker and the open source community.
N: I actually agree on one point, I am reading a post by Fox News now and the source is not mentioned once, which is a shame.
Anyway, thanks for taking the time to talk to us.
T: Thanks
Thank you for your time.
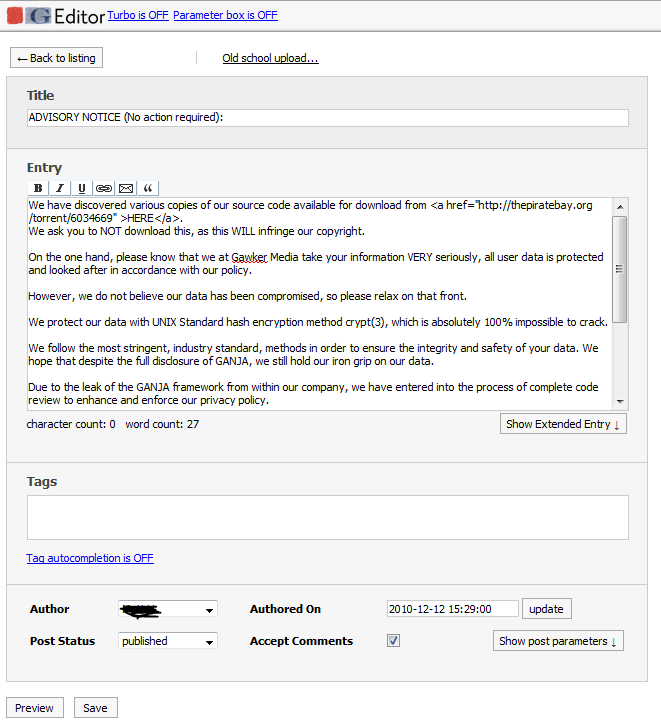
Gnosis also sent us a screenshot of the group writing and publishing the article that went live across the Gawker network. This was the post published by Adrian Chen, who went on to deny the posting and admit the site was hacked. Below is proof that Gnosis did indeed compromise the Gawker backend and publish the article:
Get the TNW newsletter
Get the most important tech news in your inbox each week.