![Gawker Media is compromised. The responsible parties reach out to TNW [Updated]](https://img-cdn.tnwcdn.com/image?fit=1280%2C720&url=https%3A%2F%2Fcdn0.tnwcdn.com%2Fwp-content%2Fblogs.dir%2F1%2Ffiles%2F2010%2F01%2F1332-300x300.jpg&signature=9668c47369db276d9c6f334f76d3c0b3)
 Updates at the foot of the post.
Updates at the foot of the post.
As we reported earlier, it appeared that the Gawker Media organization’s social media accounts (namely Twitter) had been compromised. While Twitter specifically appears to have been fixed, there’s more to the story. We have been in touch, personally, with the a member of the party responsible for the attack and it appears that the compromised information goes far beyond just a simple Twitter account.
From the information we have been provided, it appears that some of the base infrastructure of the Gawker Media organization has landed in the hands of people completely unrelated to the site or business itself. Though we were initially under the impression that it was the 4chan-founded group of Anonymous we have since been told, via email, that the responsible party has no affiliation with Anonymous or others. In fact, here’s what we’ve seen, in whole:
It has come to our attention that you are reporting about gawker.com being hacked by Anonymous and Operation payback in the war against the wikileaks drama that is currently taking place. While we feel for Wikileaks plight, and encourage everyone to donate and mirror the site, we are not related to Operation Payback or engaged in their activities. We have compromised all their email accounts and databases, and a significant portion of the passwords have been unhashed into plaintext.
To prove the validity of our claims, here is a sample of the database: [redacted]
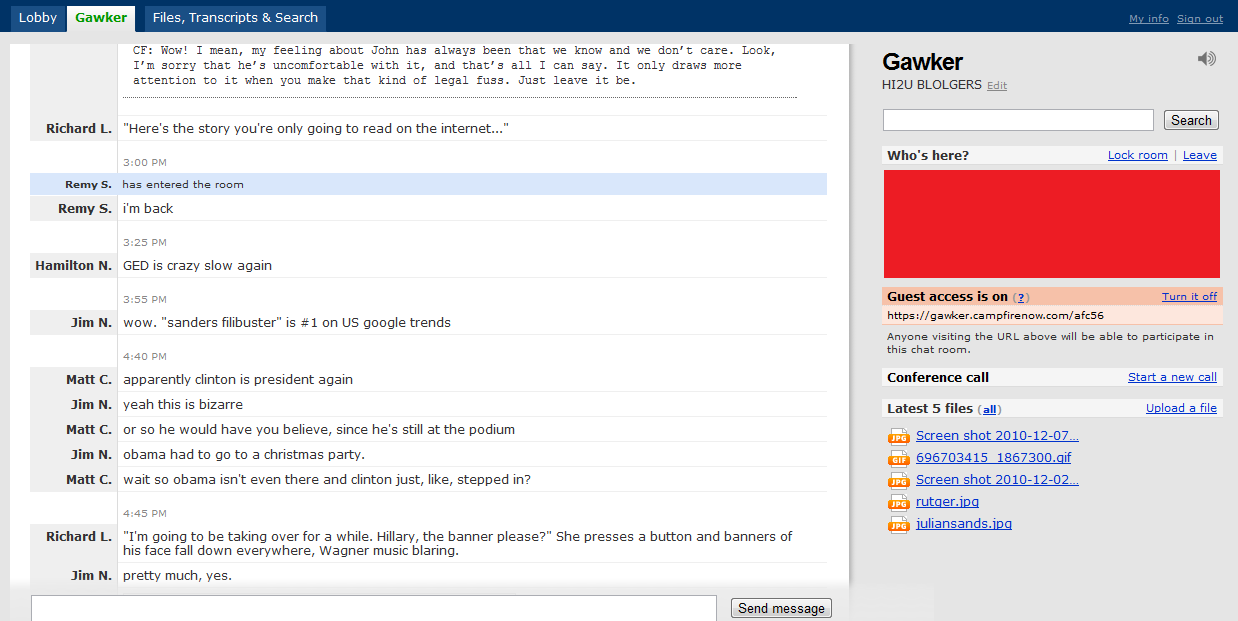
While we were, of course, skeptical of the information the claims were potentially huge. That said, we did ask for proof and proof was provided via screenshots of information that would typically only be available to a site administrator or owner. For example, here is a screenshot from the Campfire chat program that Gawker uses to communicate in real-time:
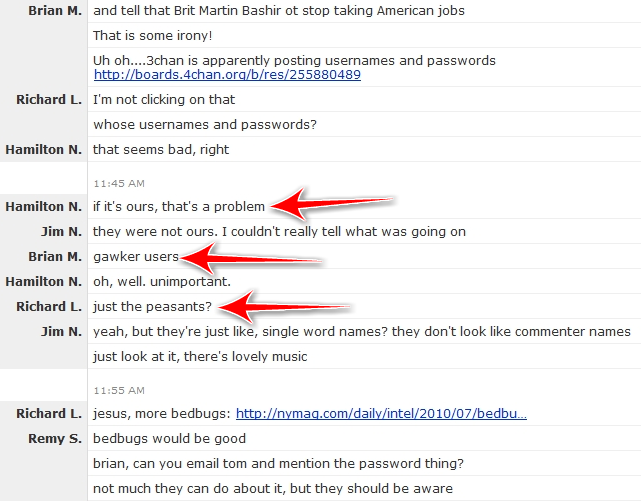
Interestingly, it appears that while 4chan wasn’t responsible for the breach of security, the data did end up on the site as evidenced by a later Campfire screenshot below:
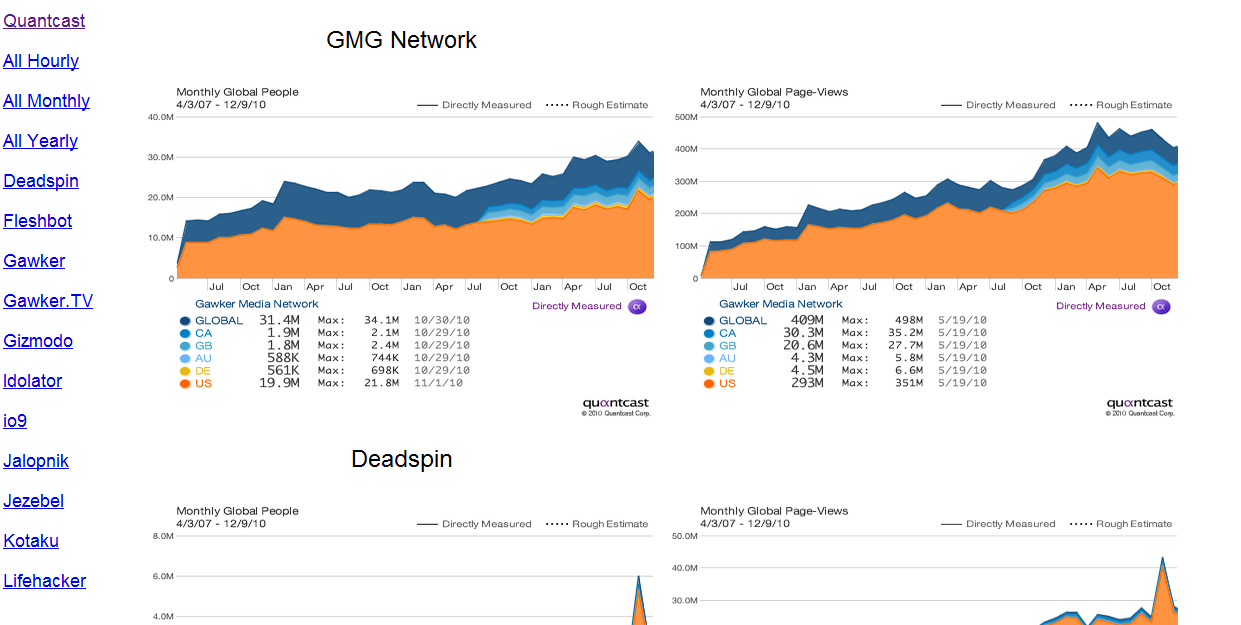
While Gawker is aware of the problem, attempts to contact the site have remained fruitless. As a final does of proof, however, the group does offer the QuantCast information for Gawker and its sister sites, again in screenshot form:
For those of you who might happen to have an account on a Gawker media site, it is advisable that you change your password. Though we are not certain if the security hole has been patched just yet, it’s till safe practice just in case.
For now, we’ll sit and wait as one of the Internet’s most notorious sites chews on a bit of its own dog food. Oh, and as a note to the folks over at Gawker — It might be time to buff up the security a bit. As we’ve been told, “We can say that it was a very obvious flaw in their security, one that any half brained trainee tech would have found and fixed.”
This article was co-authored by Brad McCarty.
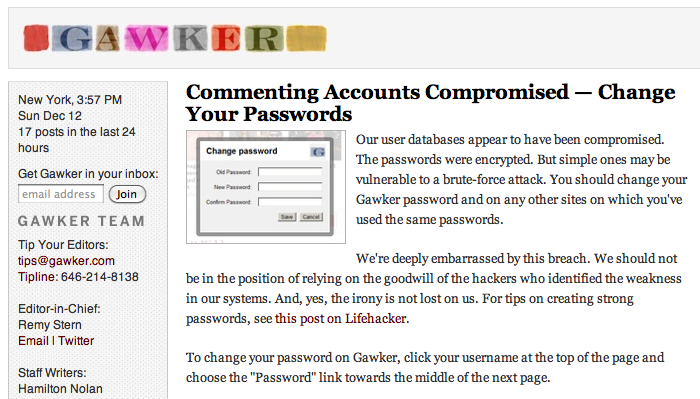
Update: After posting to Twitter that there was no evidence that Gawker accounts were compromised, Scott Kidder , Director of Editorial Operations at Gawker Media has confirmed that database data was indeed accessed by an unauthorised party.
Registered members on any of Gawker Media’s web properties should change their passwords with immediate effect, staff writers have been urged to do the same, noted in an internal email to all Gawker staff:
Our user databases do indeed appear to have been compromised. The passwords were encrypted. But simple ones may be vulnerable to a brute-force attack. You should change the password on Gawker (GED/commenting system) and on any other sites on which you’ve used the same passwords. Out of an abundance of caution, you should also change your company email password and any passwords that may have appeared in your email messages. We’re deeply embarrassed by this breach. We should not be in the position of relying on the goodwill of the hackers who identified the weakness in our systems. And, yes, the irony is not lost on us. Lifehacker has tips on how to create strong passwords: http://lifehac.kr/h7jgzQ
We’ll obviously continue to look into this and I’ll let everyone know when we have more to share.
It is not known what will happen with the data collected by the attackers, we will of course keep you updated should new information come to light.
Update: Gawkers Management Team has just posted its official statement on the Gawker.com website:
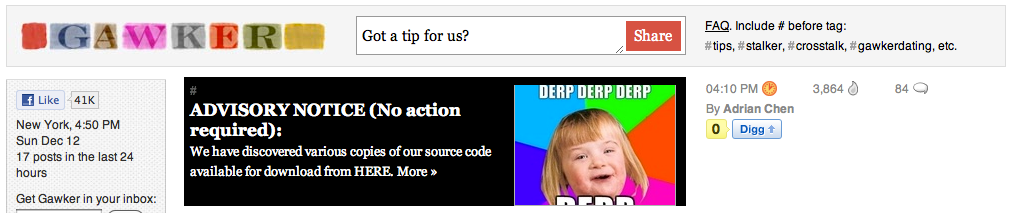
We then noticed that the front page of Gawker had been defaced, with a rather ominous message:
Understanding that this might be a ploy from Gawker to ride a wave of interested viewers, we reached out to the parties responsible for the initial attack for confirmation of their involvement. Moments later, we received the confirmation, quoted here:
Yes, we are behind it all. We have released our findings: http://thepiratebay.org/torrent…[redacted]
The only thing left to do is sit and wait, it would seem, for Gawker to fix its sites and start cleaning up the damage.
Get the TNW newsletter
Get the most important tech news in your inbox each week.