A new trojan for Android has been discovered that can help carry out Distributed Denial of Service (DDoS) attacks. The malware is also capable of receiving commands from criminals as well as sending text messages for spamming purposes.
The threat, detected as “Android.DDoS.1.origin” by Russian security firm Doctor Web, likely spreads via social engineering tricks. The malware disguises itself as a legitimate app from Google, according to the firm.
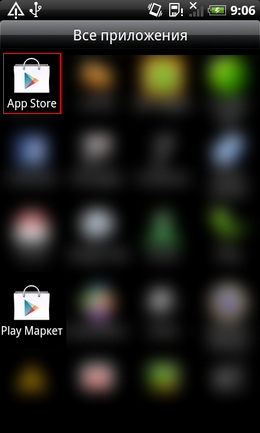
Once the app is installed, it creates an icon that resembles the one for Google Play. Tapping this icon will still launch Google Play, reducing suspicion that something isn’t right.
After it is launched, the trojan immediately tries to connect to its Command and Control (C&C) server. If successful, it sends the victim’s phone number to the criminals and then awaits instructions sent by SMS. The malware has two main functions: attack a specified server (criminals send over its address and the port), and send a text message (criminals send over the message text and the number to which it should be sent).
When it receives a DDoS attack command, the malware starts to send data packets to the specified address. One user won’t be able to hurt a site single-handedly, but if criminals have got the malware onto enough Android devices, they could potentially take down a site if if a critical mass of infected phones and tablets target it at the same time.
When it receives a command to send an SMS, it immediately spams the recipient. The infected device can hurt its victims not just by significantly reduced performance, but by unexpected charges for accessing the Internet and sending text messages.
Doctor Web notes Android.DDoS.1.origin’s the code of is heavily obfuscated, meaning its creators want to hide its true function. This shouldn’t be too surprising given that the threat can clearly be used for attacking websites (for competitive reasons, political motives, and so on), spamming products, or simply generating revenues by sending large amounts of text messages to premium numbers.
It’s important to note that we haven’t seen any indication that this threat is spreading quickly or that it is being widely distributed. That being said, it is still interesting to see Android malware used as a DDoS attack tool.
See also – Android malware surged in Q3? Sure, but only 0.5% came from Google Play and Over 60% of Android malware steals your money via premium SMS, hides in fake forms of popular apps
Image credit: Ali A
Get the TNW newsletter
Get the most important tech news in your inbox each week.