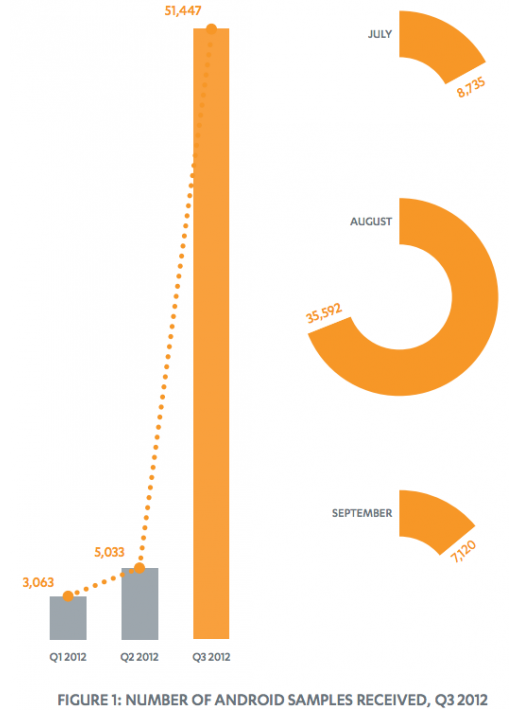
Last week, F-Secure released its 40-page “Q3 2012 Mobile Threat Report” (PDF) and of course the talk of the town was Android malware. The report included this scary-looking chart:
Unsurprisingly, the data was picked up all over the place. We decided to skip the story since it wasn’t clear how much of these threats were in the official Google Play Store; in fact “Google Play” was only mentioned once in the whole PDF.
In response to queries about a breakdown, however, F-Secure today revealed more numbers. Here’s what you have to know: out of the 51,447 samples discovered by the security firm last quarter, 28,398 were malicious samples, 146 of which came from Google Play, and 23,049 were potentially unwanted software (PUA), 13,639 of which came from Google Play.
This means that 55.20 percent of the samples were malware and the remaining 44.80 percent were risky. The difference is important: malicious apps intentionally cause harm to you or your phone, while risky apps do things like steal data, damage privacy, make payments, track web browsing, send your location, and so on.
More importantly, if only 146 of the 28,398 malware samples were found on Google Play, that means 0.51 percent were on the company’s store. This means most users, at least in countries where Google Play is available, won’t ever see these malicious apps.
That’s not all. F-Secure also underlined another important point today:
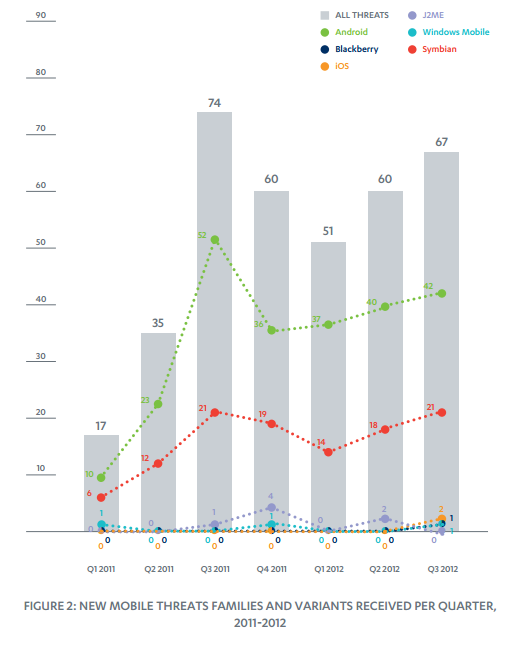
Note: please remember that sample does not necessarily equal threat. Based on our detections, the number of “families” in the wild is actually down when compared to Q3 2011
This chart puts things into perspective a bit better:
In summary, if you’re an Android user, stick to the Google Play Store when looking for apps to download and install. Even then, always read the permissions an app is requesting from you and make sure they make sense for the app you’re trying to install.
In one year, Android malware up 580%, 23 of the top 500 apps on Google Play deemed ‘High Risk’ and FUD alert: 72% of all Android apps on Google Play access permissions they shouldn’t
Image credit: Iva Villi
Get the TNW newsletter
Get the most important tech news in your inbox each week.