Stalkerware apps — software used to spy on users’ messages, call information, and GPS locations — have increased a staggering 373 percent during the first eight months of 2019 when compared to the same period the year before.
The findings, disclosed by cybersecurity firm Kaspersky, found 37,532 users who encountered such apps at least once, a 35 percent jump year over year.
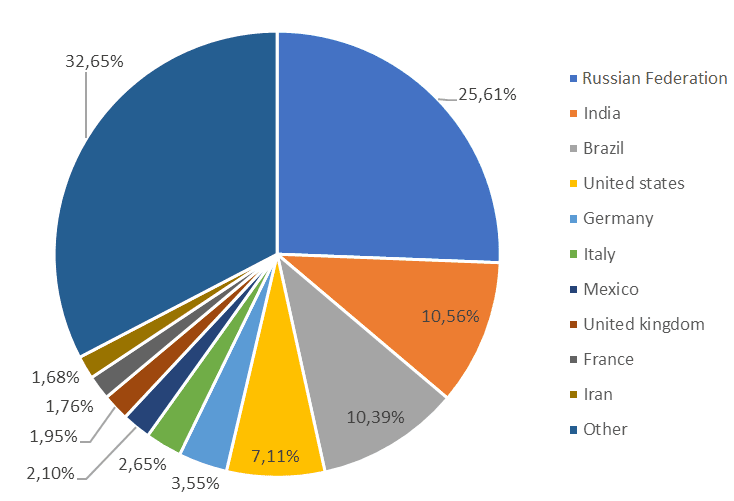
Russia, India, Brazil, and the US emerged as the prominent regions for Android stalkerware globally, while Germany, Italy, and the UK took the top three spots in Europe.
Spyware and stalkerware are both “nuisanceware” in that they are different types of malicious software that can result in the theft of personal data by covertly recording emails, SMS messages, and eavesdropping on phone calls. Stalkerware, however, is generally used by individuals to spy on those close to them.
“These openly-sold consumer surveillance programs are often used for spying on colleagues, family members or partners, and are in great demand,” the researchers said. “For a relatively modest fee, sometimes as little as $7 per month, these apps stay hidden while keeping their operators informed about the device activity, such as its owner’s location, browser history, text messages, social media chats, and more. Some of them can even make video and voice recordings.”
In all, Kaspersky found 518,223 cases where the presence of stalkerware on users’ devices was registered or an attempt was made to install spyware without the consent of the victims involved.
Stalkerware needs a vector to infiltrate a target’s mobile device defenses. Most often, this is done by manually installing the app on the smartphone or tablet. Other times, it’s remotely administered via spear phishing emails containing malicious attachments or links, which when clicked, download the payload surreptitiously without user’s knowledge.
Once installed, they were found to masquerade as parental control apps designed to monitor childrens’ whereabouts, or as anti-theft apps that operate stealthily to evade detection and deletion.
TheTruthSpy, for example, markets itself as “the best Catch Cheating Spouse App available today,” with features to track location, manage calls, monitor internet browsing activities, and spy on instant messaging apps such as WhatsApp, Facebook Messenger, Kik, Viber, and Snapchat. What’s more, it’s completely undetectable.
It’s worth noting that although WhatsApp is end-to-end encrypted (E2EE), the security feature is of no use when the endpoint itself is compromised with surveillance software.
“It may take time to discover the role of stalkers on the cyberthreat landscape, but more incidents are now accounted for,” Kaspersky said. “Those with bad intentions may use it to monitor employee emails, track children’s movements and even spy on what a partner is up to. Such uses may lead to harassment, surveillance without consent, stalking and even domestic violence.”
This is not the first time stalker apps have been found on Android. Earlier this July, researchers from cybersecurity firm Avast detected eight such apps on the Google Play Store that allowed people to keep tabs on employees, romantic partners, or kids, prompting Google to take them down.
But unlike the apps discovered by Avast, the majority of stalkerware apps encountered by Kaspersky are not available on official app stores, suggesting that the “installation requires access to a dedicated website and access to the victim’s device.”
Spyware and stalkerware are intentionally designed to make them hard to find and hard to remove. To protect yourself against such threats, it’s essential that you run a malware scan, and physically secure your device with a strong password. If all else fails, a drastic step would be to reset your phone back to factory settings.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





