
Researchers have revealed a previously undocumented threat actor of Chinese origin that has run at least six different cyber espionage campaigns in the Southeast Asian region since 2013.
The findings — disclosed by Palo Alto Networks’ threat intelligence team Unit 42 — linked the attacks to a group (or groups) it calls PKPLUG, named after its tactic of delivering PlugX malware inside ZIP files, which are identified with the signature “PK.”
The ambiguity in its attribution is because “our current visibility doesn’t allow us to determine with high confidence if this is the work of one group, or more than one group which uses the same tools and has the same tasking,” Unit 42 said.
PKPLUG has been found to install backdoor Trojan implants on victim systems, including mobile devices, for tracking and gathering information, although their ultimate motives are as yet unclear.
Their main targets include Myanmar, Taiwan, Vietnam, and Indonesia, along with Mongolia, Tibet, and Xinjiang, all three of which are known for their contentious relations with China. Xinjiang province, in particular, is home to the country’s Uyghur Muslim minority, a populace that has been the subject of persecution and heightened surveillance in recent years.
“This group (or groups) has a long history and series of creating custom tools which implies they are persistent, and well-resourced,” Unit 42’s Alex Hinchliffe told TNW. “For example, the creation and use of a custom Android malware […] may indicate their targets require unique attention based on prevalent operating systems used or that they need that capability generally. This group(s) is patient in what they work toward.”
PKPLUG modus operandi
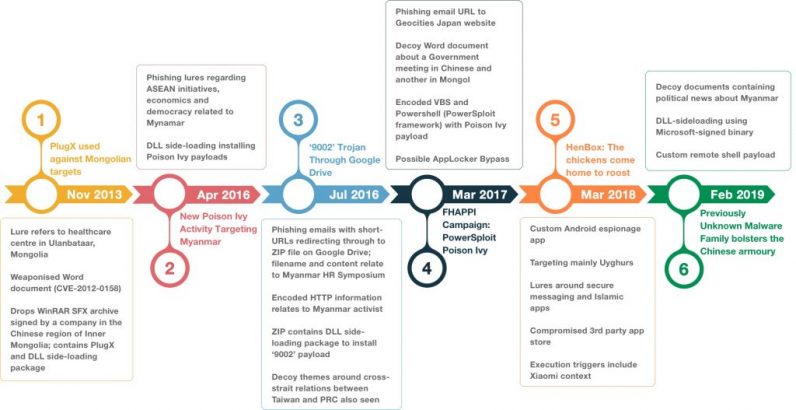
Unit 42’s report combines its own research with those published by other cybersecurity firms such as Blue Coat Labs and Arbor Networks to piece together a timeline of PKPLUG’s malware-based tactics, techniques, and procedures (TTPs).
The earliest confirmed PKPLUG attack is said to have occurred in November 2013, when they were found to target Mongolian individuals with PlugX malware. Three years later, they were caught using Poison Ivy malware against Myanmar and other Asian countries.
That same year, Unit 42 reported attacks via spear phishing emails used to download a ZIP file hosted on Google Drive that loaded a Trojan to compromise victim devices.
In early 2018, the firm discovered a new malware family — called HenBox — that masqueraded as a legitimate Android app to primarily target the Uyghurs and compromise Xiaomi devices with a goal to harvest outgoing phone calls to China and access the phone’s microphone and camera.
Interestingly, the investigation gave away one of PKPLUG’s other tricks to lure unsuspecting users: make the espionage app available on a third-party Android app store, and even pose as a VPN app named DroidVPN to get them to download it.
VPN apps are how citizens in China get around the Great Firewall, and the fact that they were employed as an attack vector is indicative of cybercriminals’ tendency of increasingly banking on users’ trust in security-related apps to install malware.
Fast forward to February 2019, Unit 42 uncovered the group’s use of a Windows backdoor known as Farseer, which leveraged sideloaded libraries to install malicious payloads — a common technique that connects their disparate campaigns.
PKPLUG’s reuse of domain names and IP addresses also helped strengthen the overlaps between the different cyber offensives, the research noted.
The need for endpoint security
Details of PKPLUG’s elaborate cyber espionage attacks come merely days after Check Point Research disclosed a similar data-stealing campaign directed at Southeast Asia undertaken by a Chinese hacking group called Rancor.
Asked if these state-sponsored actors could be working in tandem to enable targeted operations on a large-scale, Hinchliffe told TNW: “We’ve seen nation-states, like Russia, hire various groups to lead out attacks, and while it’s possible in this scenario, we don’t have enough data at this time to make that assumption.”
In addition to avoiding downloading apps from third-party Android stores, Hinchliffe recommends businesses secure their network endpoints, and evaluate their BYOD (short for “bring your own device”) policies by limiting device access to the network.
Although this latest research offers a peek into PKPLUG’s activities, it’s far from a conclusive picture.
“Presumably, there are more victims that were targeted, more tools used, and more infrastructure. The more organizations that shine a light on threats like PKPLUG moving forward, the more complete our picture can become,” Hinchliffe said.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




