Google Play Store has a malware problem. And it doesn’t seem to go away despite the company’s best efforts to rein in sketchy apps.
In a yet another instance of Android adware, New Zealand-based independent security researcher Andy Michael found four Android VPN apps with cumulative downloads of over 500 million that not only serve ads while running the background, but are also placed outside the apps, including the home screen.
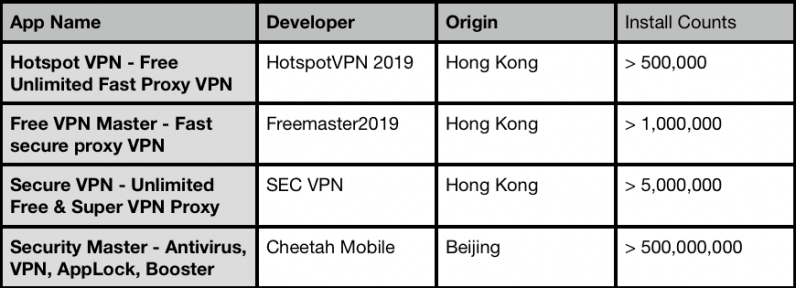
The apps in question are Hotspot VPN, Free VPN Master, Secure VPN, and Security Master by Cheetah Mobile. It’s notable that all these apps originate from Hong Kong and China, where citizens have typically relied on VPNs to get around the Great Firewall.
The apps are live on the Play Store to this date. But in an interesting twist, the apps containing the adware were all VPN or antivirus apps, suggesting that developers are increasingly banking on users’ trust in security-related apps to commit ‘outside ad fraud.’
Disruptive ad behavior
Apart from containing advertisement APIs from both Google and Facebook, Hotspot VPN, developed by HotspotVPN 2019, contained obfuscated code to show full-screen ads at any given point of time — irrespective of whether the app was running in the foreground or otherwise — resulting in significant battery and CPU usage.
Free VPN Master developed by Freemaster2019, likewise, shared the same code for serving Google ads, with both APK files having the same code structure and files.
Michael concluded that the two apps are most likely the same with slight modifications in code that were found to be obfuscated using the same tool.
“If the apps were force stopped from Android settings, they stop serving ads,” he told TNW. “Opening the app once after downloading will usually trigger the behavior.”
The third app, Secure VPN by SEC VPN, is the worst of the four in that it served ads even when people were using other apps, and at times overlaid on top of the home screen, thereby hiding app icons.
The app was also found to have references to code that recorded activities, including ads that were displayed, clicked and dismissed by the user, implying they were used to monitor and display ads based on their activities.
Security Master, on the other hand, leverages a more sophisticated behavior to show ads, such as when a user tries to get back to the home screen or when certain buttons are clicked.
Ad-supported apps are nothing new. They’ve proven to be a viable alternative to subscriptions and one-time purchases. But serving ads while apps are running in the background can result in significant use of the device’s resources like battery and CPU.
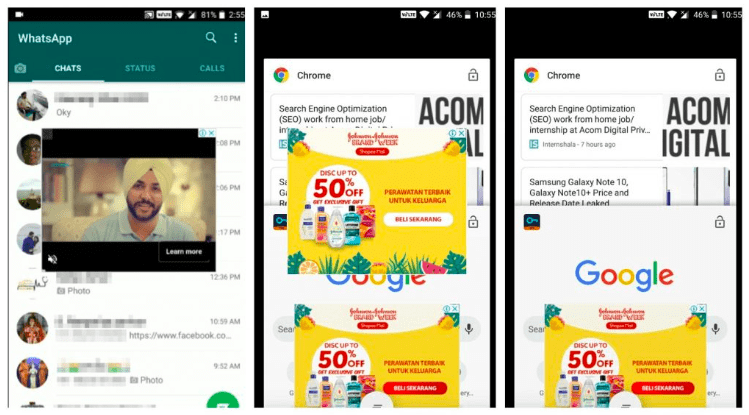
Cheetah Mobile, for its part, has been previously accused of turning smartphones into stealthy click farms to engage in ad fraud, leading Google to ban a bunch of its apps from the Play Store.
“Developers use this [method] because every impression/click gives them revenue,” Michael said. “Due to high popularity of VPN apps, if making a quick buck is the goal, serving outside ads in VPN apps would be a logical choice.”
Google has a strict policy with regards to adware and disruptive ads in general. “We don’t allow apps that contain deceptive or disruptive ads. Ads must only be displayed within the app serving them. We consider ads served in your app as part of your app. The ads shown in your app must be compliant with all our policies.”
The company, when reached for a response, said it would take action on the apps if they’re indeed found in violation of its policies. If we find out more, we’ll update the story accordingly.
The Play Store trouble
This is not the first time the Google has struggled to curb the spread of harmful apps on its official mobile software distribution platform.
In August, Lukas Stefanko, an ESET security researcher, compiled a list of 204 apps on Google Play that had over 438 million installs and were found to engage in ad fraud, adware, and serve other kinds of malware. And this was just for last month.
Although the Mountain View behemoth’s antivirus efforts have resulted in the removal of hundreds of thousands of harmful apps, the security layer has not been entirely bulletproof to offer protection from all sorts of malware.
Review of harmful apps found on Google Play in August 2019
Summary: 204 apps with over 438,400,00 installs.https://t.co/o9DIk38Cir pic.twitter.com/qnk1Cx6EoX
— Lukas Stefanko (@LukasStefanko) September 2, 2019
Complicating the matter is the open nature of Android, which makes it relatively easy for copycat and malicious apps to escape detection, thus leaving users at risk.
“Keeping the Android ecosystem secure is no easy task, but we firmly believe that Google Play Protect is an important security layer that’s used to protect users devices and their data while maintaining the freedom, diversity and openness that makes Android, well, Android,” Google acknowledged earlier this year.
The fact that a legitimate app store like Google Play repeatedly harbors malicious apps is a cause of concern. Android users are often advised not to download apps from third-party sources to avoid malware. Unfortunately, it seems sticking to the Play store isn’t always safe either.
“While the key security imperative ‘Stick with official sources of apps’ still holds, it alone can’t guarantee security,” Stefanko cautioned last month. “It is highly recommended that users scrutinize every app they intend to install on their devices.”
Get the TNW newsletter
Get the most important tech news in your inbox each week.