
The malware campaign targeting the Uyghur Muslim minority in China’s autonomous region of Xinjiang may have been more extensive than previously thought.
According to a new report published by Washington, DC-based digital forensics firm Volexity, the community has been been at the receiving end of a large-scale surveillance operation via “strategically compromised websites” affecting mobile devices running not just iOS, but also Android.
This indicates that the campaign targeting Uyghurs was far broader in scope than Google initially disclosed.
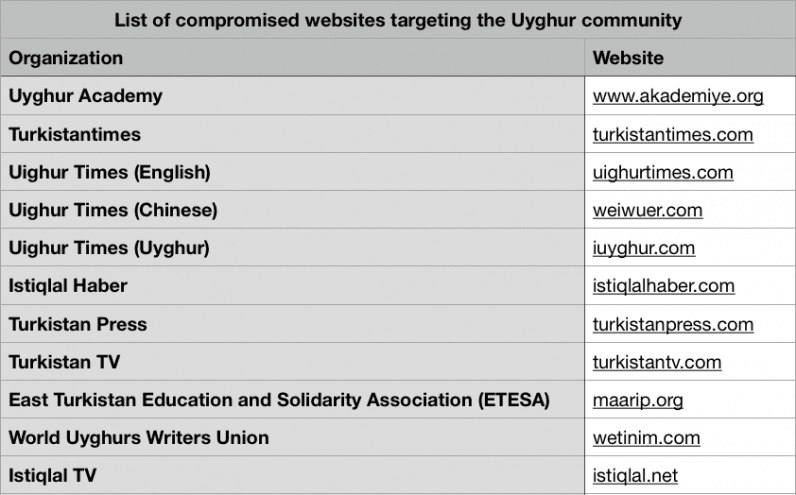
“The systematic targeting and compromise websites that are run by and cater to Uyghurs make it clear they are the primary targets,” the report said. “However, each of the compromised websites are banned by the Great Firewall in China, leaving largely only those outside of the country as targets and potential victims.”
The ongoing cyber-attacks against Uyghurs have been traced back to at least two separate Chinese threat groups — Evil Eye and an unidentified actor — per Volexity, based on the modus operandi of delivering malicious code using compromised websites.
Android as an attack surface
Over the weekend, multiple reports from TechCrunch and Forbes found that Chinese advanced persistent threat (APT) groups were using a number of previously undisclosed flaws in iOS (since patched by Apple) to lure Uyghur Muslims to malicious sites that installed spyware on the devices.
The development followed an earlier analysis by Google’s Project Zero security team last week, which uncovered a group of malware-infested websites that were used as a watering hole to attract and infect iPhone users by penetrating iOS’s digital protections.
But Google’s deep-dive of the exploits also faced some criticism for not revealing the names of the websites that were used in the attacks, and the threat actors behind the operation.
Now it appears there’s to more to the story than meets the eye, as the attacks seem to have leveraged Android phones as an attack surface — a fact that was completely missing from Project Zero’s report.
Volexity noted that it was able to identify 11 different Uyghur and East Turkistan websites (listed above) that were compromised as part of the campaigns, some of which go back at least four years.
In addition, the attackers engaged in a variety of phishing attacks by spoofing popular domains like Google, the Turkistan Times, and the Uyghur Academy, and gained access to users’ email and contact lists by posing as a legitimate third-party app (see image below).
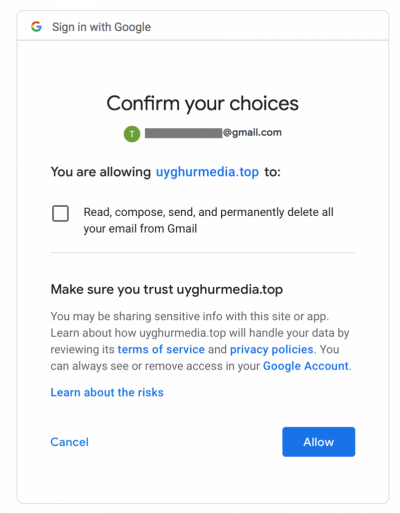
It’s to be noted that Google has been steadily cracking down on third-party developer access to Gmail, Google Drive, and Chrome extensions in recent months as part of its ongoing Project Strobe “root-and-branch review.”
Are the two events related?
Although the report confirms the malware attacks targeting Android users through Uyghur/East Turkistan websites, Volexity notes “it is reasonable to suspect that these same attack campaigns could have easily been leveraged to target Apple and Microsoft users.”
Interestingly, the firm observed a number of suspicious behaviors that have led the researchers to think the exploits uncovered by Google and those detailed above are possibly related.
It said the three domain names leveraged by Evil Eye (akademyle.org, turkistantlmes.com, and google-analysis.info) stopped resolving shortly after Google’s post went live on Project Zero blog.
Around the same time frame, a number of the websites listed above started showing Google Safe Browsing warnings in Google search results, and that most of the malicious scripts referenced on the compromised websites were removed.
Given the lack of conclusive evidence, it’s not immediately clear if the search giant was aware of these attacks, and if so, whether they were all part of a coordinated malware campaign across different operating systems.
We’ve reached out to Google to confirm the findings, and we’ll update the story if we hear back.
While the Uyghurs have long been subject to physical and electronic surveillance, the aforementioned barrage of digital snooping techniques unleashed upon the community sheds light on the extensive surveillance apparatus put in place by the country.
“China has continued to increase the level of effort and sophistication they have put into targeting Uyghurs,” Volexity concluded. “As a result, it is critically important that Uyghurs take into consideration when using their computers and mobile devices that they may have been targeted and compromised, especially if the websites listed above are frequented.”
Get the TNW newsletter
Get the most important tech news in your inbox each week.





