More than 300,000 users continue to utilize credentials that have been previously compromised, with people visiting entertainment and porn websites most at fault.
That’s according to a new study by Google, which found that approximately 1.5 percent of all sign-ins used across the web involved credentials that have been already hacked.
The findings come from a telemetry analysis of its Password Checkup Chrome browser extension that it launched earlier this year. Google is presenting details of the study this week at the USENIX Security Symposium in Santa Clara, California.
“We scanned 21 million usernames and passwords and flagged over 316,000 as unsafe — 1.5 percent of sign-ins scanned by the extension,” the search giant said. “By alerting users to this breach status, 26 percent of our warnings resulted in users migrating to a new password. Of these new passwords, 94 percent were at least as strong as the original.”
But users also opted to ignore 81,368 — or 25.7 percent — of the breach warnings presented to them, the study found.
The paper — “Protecting accounts from credential stuffing with password breach alerting” — noted data for the study was collected from 670,000 users over a month-long period between February 5 – March 4, 2019.
The need for breach alerting
The alarming frequency and scale of data breaches have left user accounts exposed to credential stuffing attacks, where in stolen login information from cyber thefts are used to gain unauthorized access to other accounts.
Worse, data dumps comprising of billions of stolen credentials — including passwords that have been ‘dehashed’ and converted back to plaintext — are floating around on the Dark Web and underground forums, making it easy for bad actors to exploit.
This effectively means, all an attacker will have to do is login to different websites with every breached credential in order to isolate vulnerable accounts.
While knowing which accounts require your attention still remains a chore, services like Firefox Lockwise, HaveIBeenPwned, and Enzoic (formerly PasswordPing) have stepped in to fill that void.
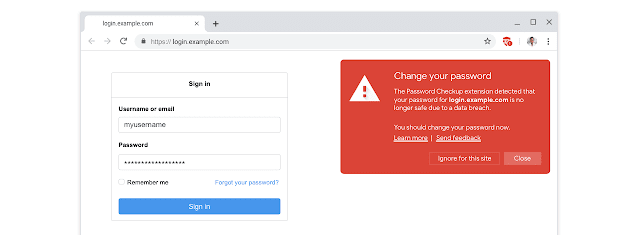
But these breach alerting services come with their own privacy tradeoffs, as Google notes in the paper:
Firefox and LastPass check the breach status of usernames to encourage password resetting, but they lack context for whether the user’s password was actually exposed for a specific site or whether it was previously reset.
Equally problematic, other schemes implicitly trust breach alerting services to properly handle plaintext usernames and passwords provided as part of a lookup. This makes breach alerting services a liability in the event they become compromised (or turn out to be adversarial).
Google, therefore, has made the case for a “new privacy-preserving protocol that allows a client to learn whether their username and password appears in a breach without revealing the information queried.”
Say hello to Private Set Intersection!
The Password Checkup extension works by employing this new cryptographic protocol — which Google calls Private Set Intersection (PSI). It allows for matching hashed login information against an encrypted data set of 4 billion compromised credentials that were leaked in previous data breaches without revealing the details to anyone, including Google.
So, when you login to a site, if Google finds that your username and password is no longer safe due to appearing in a third-party data breach, you’ll receive an alert (see image above) and will be prompted to change your password.
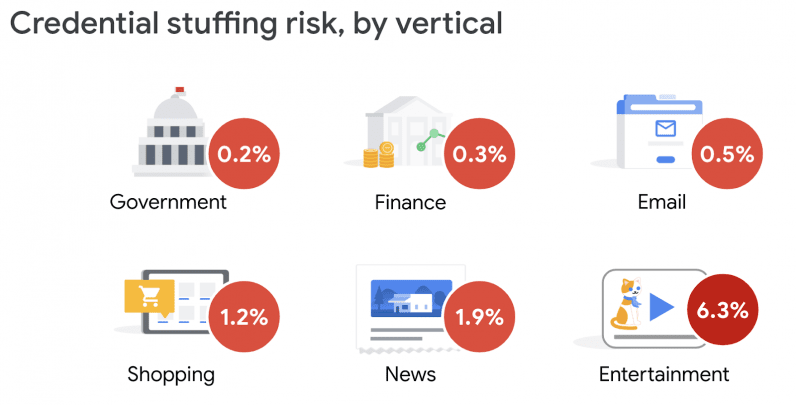
The verticals that generated the most warnings were adult sites and entertainment sites — the former had a warning rate of 3.6 percent, while sites belonging to the latter category had a rate of 6.3 percent.
The limitation of this approach is that the hashing is computationally expensive, with Google observing that the process requires at least 256MB of memory. This could be a challenge for devices — particular smartphones — that may have memory constraints.
Another significant pitfall is the matching process itself. The extension currently works by downloading the compromised credentials data in chunks, but Google’s security team cautions this could be affected as new breach information is added to the database.
Interestingly, the core PSI protocol also underpins Private Join and Compute, an open-sourced cryptographic method that helps organizations work together with confidential data sets in a privacy-preserving manner.
The takeaway
Note that the results are based only on a sample of 21 million logins; as a result, it’s possible there are more people using hijacked credentials to login to their websites.
It’s imperative you use unique passwords for each site and promptly change passwords when they’re exposed, unless you want to leave them deliberately vulnerable to password guessing attacks and, worse, identity theft.
But Google knows too well that not everyone will install the extension, as it’s an opt-in feature. So, it’s doing the obvious — integrating the feature directly into Chrome browser.
In addition, by making the protocol public, Google hopes it’ll incentivize researchers to step in and improve the current model. “Our protocol is a first step in democratizing access to breach alerting in order to mitigate one dimension of account hijacking,” Google said.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





