Researchers at cybersecurity firm ESET have unearthed a targeted cyber-espionage campaign that sets out to steal sensitive documents from Venezuela’s military forces
“The attackers exfiltrate specialized file types used by geographic information systems (GIS) software,” said ESET researcher Matias Porolli. “The group is specifically interested in files that describe navigation routes and positioning using military grids.”
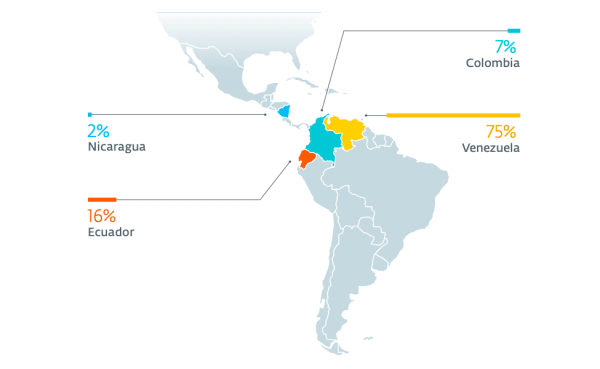
About 75 percent of the malware infections —all operated by Machete — were located in Venezuela, with other victims spread out across Ecuador, Colombia, and Nicaragua.
First documented by Kaspersky in 2014, the Machete group has been active at least since 2010, focusing on a variety of targets across Latin America. But starting this year, ESET said it has primarily been focusing its hacking efforts on Venezuela.
The researchers observed more than 50 infected computers communicating with command-and-control (C&C) servers between the period March and May 2019. This is to deploy routine malware changes in its infrastructure to thwart detection and modify spear phishing campaigns, they noted.
The modus-operandi
The espionage group resort to the time-tested approach of sending phishing emails to intended targets, containing malicious files as attachments.
To lure them into opening the emails, the group cleverly uses previously stolen classified military documents, including radiograms — the widely used format by military organizations to transmit messages. In addition, the attackers leverage their knowledge of military jargon and etiquette to craft convincing phishing emails.
Once opened, the decoy document infects the target’s device with backdoor malware. ESET said the malware — coded in Python — is a new version that was first seen a year ago.
The malware includes a persistent spy component that runs indefinitely in the background, copying and encrypting documents, taking screenshots, and acting as a keylogger. It also communicates with the C&C server every 10 minutes to send the stolen data, and mask their true intent by naming their files as “Google” (GoogleCrash.exe and GoogleUpdate.exe).
ESET said the phishing campaign is still active to this day, and that the hackers have successfully exfiltrated gigabytes of confidential documents every single week.
Who are they?
The researchers have found various instances of Spanish words in the malware code, with the logs generated by capturing keystrokes and clipboard data written out in the same language. This suggests they have been developed by a Spanish-speaking group.
Previous public disclosures by Kaspersky and Cylance (which was acquired by BlackBerry early this year) have echoed similar findings, but details about their exact identity remain unknown.
“The group behind Machete has managed to continue operating even after researchers have published technical descriptions and indicators of compromise for this malware,” ESET researchers concluded. “It is the targeted organizations, though, who have failed in raising awareness and applying security policies so that employees don’t fall for these attacks in the first place.”
Get the TNW newsletter
Get the most important tech news in your inbox each week.