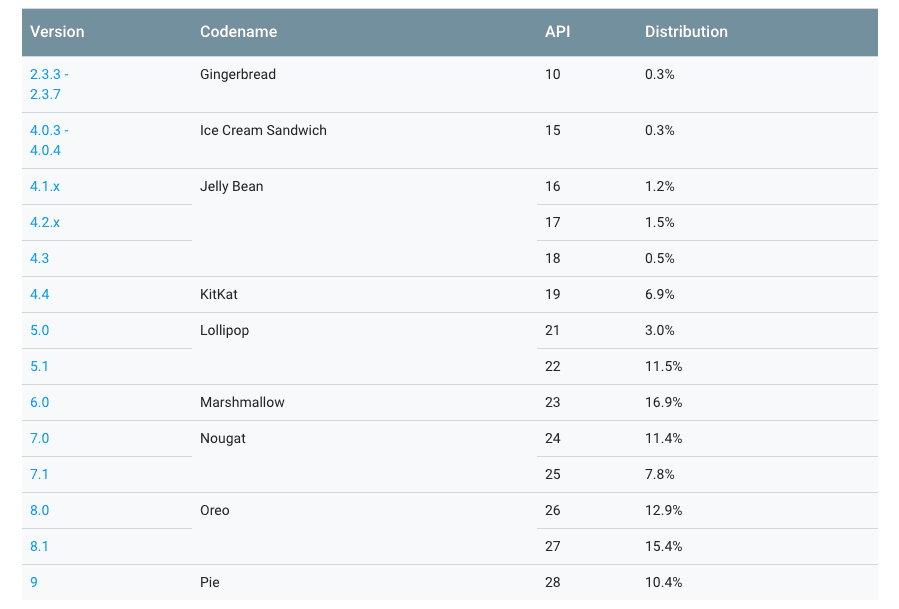
If you use a phone running any version of Android between 7.0 and 9.0 (Nougat, Oreo, or Pie), you ought to immediately install the latest security update – or risk getting your handset hijacked by devious video malware.
The culprit is a vulnerability in the aforementioned Android versions (CVE-2019-2107), which enables hackers to remotely execute arbitrary code by sneaking in “specially crafted files,” like videos laced with a malicious payload. Once a victim has opened the file, attackers can gain access to their device.
Developer Marcin Kozlowski has already uploaded a proof of concept for the attack vector on GitHub. “You can own the mobile [device] by viewing a video with [the malicious] payload,” Kozlowski wrote in the documentation.
“A possible attack vector is opening an unmodified malicious video file,” Kozlowski told TNW. “Such files can be sent for example via email (the Gmail app loads video with Android’s stock video player, unless you changed it to another player).”
Fortunately, there are some caveats that make the exploit difficult (but not impossible) to pull off.
For one, the attack will only work if victims load the infectious video in its unmodified state.
In fact, people in the Twitterverse have already speculated that sending the malware via services that re-encode the video – like YouTube, WhatsApp, or Messenger – will stifle attacks.
Kozlowski seconds this assumption. “If the video would be touched or re-encoded, which I think messengers do, it would stop the attack,” he told TNW. “Re-uploading should break the exploit,” ESET malware researcher Lukas Stefanko further told TNW.
Google has already dropped a fix
While the vulnerability is pretty severe, the good thing is that Google has already rolled out a security update that fixes the issue.
Indeed, the kink in question was one of the three Media Framework vulnerabilities Google addressed in its July Security Bulletin. “The most severe vulnerability in this section could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,” the company wrote.
It’s difficult to estimate how many devices are at risk, but Google bragged there are over 2.5 billion active Android handsets back in May 2019. Out of those, nearly 58 percent (about 1.5 billion) are running versions of Android susceptible to this vulnerability, according to Google’s distribution dashboard.
Of course, there’s no telling how many of those phones have been patched with the latest security update. Google didn’t specify the exact number, but a spokesperson told TNW its security team hasn’t seen any evidence of this vulnerability being exploited in the wild.
Earlier in July, Symantec uncovered an attack vector that made it possible to manipulate media files – like videos and images – on WhatsApp and Telegram. Unlike this Android vulnerability though, the malware Symantec detailed didn’t allow for remote code execution or device takeover.
If you’re running an affected Android version, your best bet would be to update your operating system as soon as possible. Google has already released a security update (2019-07-05) that patches this issue. Follow these steps to protect yourself.
Get the TNW newsletter
Get the most important tech news in your inbox each week.