
Ransomware is really nasty. Once it’s infiltrated your system, it’ll place your crucial work files and cherished family photos out of reach, and demand a small fortune in Bitcoin for their return. Fortunately though, new research from Finnish security firm F-Secure suggests that this is a threat that’s hit its peak.
F-Secure’s Changing State of Ransomware report takes a deep dive into this malevolent form of malware, and notes that it evolved massively during 2017. Although ransomware attacks grew 400 percent in 2017, this is attributed to one specific incident: WannaCry.
To refresh your memory, WannaCry was a ransomware worm believed to originate from North Korea’s intelligence agencies. Its purpose was two-fold: to give North Korea’s adversaries a bloody nose, and to generate revenue for the cash-strapped and internationally-isolated repressive regime.
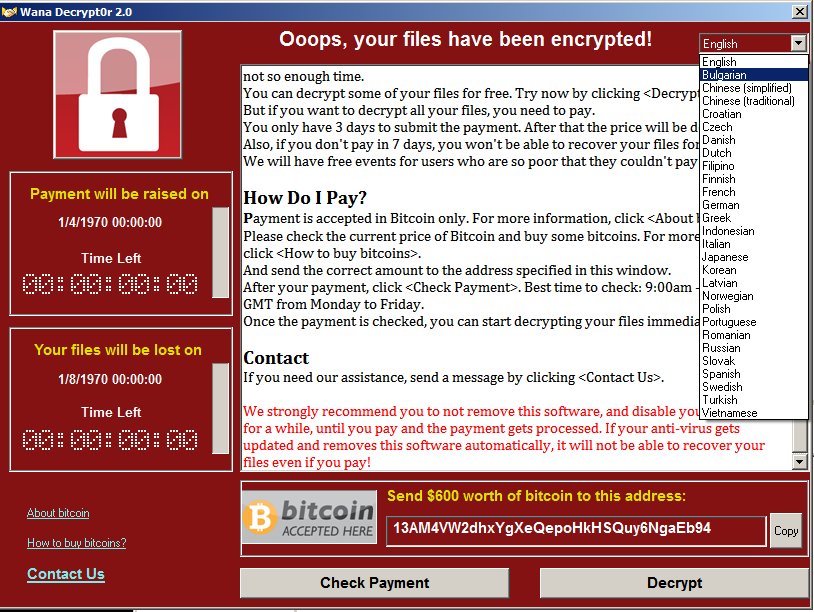
Its big debut happened around this time last year. It didn’t take long for it to utterly devastate nearly 200,000 computers, many of them in corporate, government, and healthcare environments. The UK’s healthcare system, for example, had to temporarily cancel or delay operations, as clinicians were locked out of key information systems. The worm also devastated computers belonging to the Spanish telco giant, Telefonica.
Although it didn’t raise that much cash for the attackers, it caused billions of dollars worth of damage.
The magnitude of WannaCry alone accounts for much of the growth we saw in ransomware attacks last year. But elsewhere, things are quiet, with the use of ransomware by organized criminals having slumped markedly:
“After the summer, there was a noticeable shift away from the kind of ransomware activity that we’ve seen in the last year or two,” Explained F-Secure security advisor Sean Sullivan, in a statement.
Sullivan explained that the current focus in ransomware development is largely targeted at corporate environments, rather than ordinary consumers. This is a major shift, but arguably a more lucrative one. He highlighted the example of the ransomware that devastated the City of Atlanta’s IT infrastructure recently, which was spread via exposed RDP ports.Here, the attackers wanted $50,000 in ransom — which is vastly more than what a home user would be in a position to pay up.
Overall, the incident cost Atlanta taxpayers an astonishing $2.7 million, as government officials fought to recover their systems. It’s not clear if the City of Atlanta paid the ransom, or not.
Sullivan explained:
“The last couple of years saw cyber criminals developing lots of new kinds of ransomware, but that activity tapered off after last summer. It looks like the ransomware gold rush mentality is over, but we already see hard core extortionists continuing to use ransomware, particularly against organizations because WannaCry showed everyone how vulnerable companies are.”
F-Secure’s Changing State of Ransomware report is available to read here.
The Next Web’s 2018 conference is just a few weeks away, and it’ll be ??. Find out all about our tracks here.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





