
Now this is an ironic flub-up. Popular utility tool CCleaner (short for ‘Crap Cleaner’), which promises to clean up your system for enhanced performance, was hacked to distribute malware directly to its users, Cisco Talos reports.
The app, which touts more than two billion downloads and over two million active users according to parent company Avast, was infected with a malicious payload that made it possible to download and execute other suspicious software, including ransomware and keyloggers.
While developer Piriform and Avast have already confirmed the attack, the good thing is that there is currently no evidence to suggest the exploit was used to install additional malware.
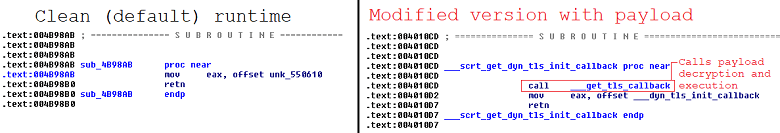
The malware was also programmed to collect a bunch of user data, including:
- Name of the computer
- List of installed software, including Windows updates
- List of running processes
- MAC addresses of first three network adapters
- Additional information whether the process is running with administrator privileges, whether it is a 64-bit system, etc.
Though it in no way alleviates the blunder, the appmaker says all stolen data was encrypted and unlikely to be accessed.
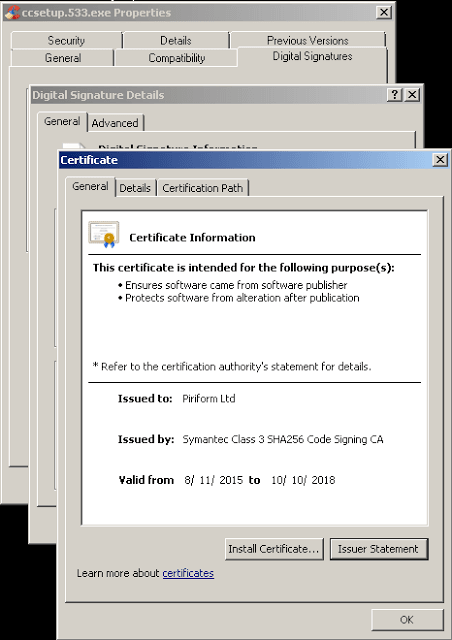
Talos’ report warns that the malware was found in CCleaner version 5.33, which was actively distributed between August 15 and September 12. What is particularly jarring is that it appears the infected app was signed with a valid certificate Symantec issued to Piriform (recently acquired by Avast).
According to reports, the malware-infested version of CCleaner was downloaded by 2.27 million users. Speaking to Forbes, Avast chief technical officer Ondrej Vlcek said that, “2.27 million is certainly a large number, so we’re not downplaying in any way. It’s a serious incident. But based on all the knowledge, we don’t think there’s any reason for users to panic.
“To the best of our knowledge, the second-stage payload never activated… It was prep for something bigger, but it was stopped before the attacker got the chance.”
Should you happen to be one of the millions of users that downloaded the infected version 5.33, your best bet is to head to Piriform’s website here and update to the latest iteration of CCleaner.
Those interested in more technical details can peruse Talos’ full vulnerability report here.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





