A serious zero-day vulnerability has been disclosed in Zoom video conferencing app on the Mac.
Security researcher Jonathan Leitschuh, in a Medium post, detailed the flaw that could let websites hijack your Mac’s camera and “forcibly” join you to a Zoom call without your permission.
Zoom is one of the most popular cloud-based enterprise communication platforms that offers chat, video and audio conferencing, and options to host webinars and virtual meetings online. About four million of its users are on Mac.
The vulnerability takes advantage of a pretty simple feature that gives Zoom users an easy way to dial into video conference calls with the tap of a link — something like https://zoom.us/j/999999999, where ‘999999999’ is a random nine-digit meeting ID that expires once the meeting ends.
This Zoom vulnerability is bananas. I tried one of the proof of concept links and got connected to three other randos also freaking out about it in real time. https://t.co/w7JKHk8nZy pic.twitter.com/arOE6DbQaf
— Matt Haughey (@mathowie) July 9, 2019
This ensures that as long as the Zoom app is running in the background, if you open the meeting link on your browser, it automatically launches the Zoom client on your Mac.
Leitschuh found this functionality was not securely implemented. Not only can a user be auto-joined to a Zoom video conference call by merely clicking on the meeting link, this works even if you no longer have the Zoom app installed.
It’s because when you install the Zoom app, it also installs a web server locally to accept meeting requests. The troubling part here is that post uninstalling the app, the server still persists and can re-install the app without requiring your intervention.
Let’s not overlook the root of the problem here: Zoom designed their application so the person controlling the meeting decided if your video camera is on, NOT YOU.
This was done on purpose by their product designers.— PlaneOnSecurity (@SwiftOnSecurity) July 9, 2019
This effectively means, in order to exploit this vulnerability, all an attacker needs to do is create an invite link through his account on Zoom, embed it on a website as a malicious ad, and just lure the target into visiting that website.
The camera, however, can be turned off if you have ticked the option “Turn off my video when joining a meeting.”
Leitschuh originally disclosed the flaw on March 26, 2019, but he mentioned the first actual meeting about how the vulnerability would be patched occurred on June 11, 2019, only 18 days before the end of the 90-day public disclosure deadline.
The timeline in the Medium post shows that Zoom fixed the vulnerability on June 21. But a regression earlier this month caused the bug to resurface again, prompting Zoom to fix the issue yesterday.
Heads up @zoom_us:
The fix for the security vulnerability that impacts ~4 million of your users has regressed.
90-day public disclosure deadline was June 24th.
I’m going public tomorrow.
This is unacceptable.— Jonathan Leitschuh (@JLLeitschuh) July 7, 2019
“Zoom did end up patching this vulnerability, but all they did was prevent the attacker from turning on the user’s video camera. They did not disable the ability for an attacker to forcibly join to a call anyone visiting a malicious site,” Leitschuh wrote.
The idea that any website you may visit from Mac has the capability to activate your video camera by default via an unauthorized Zoom call is alarming. Zoom has responded that it doesn’t see “video on by default as a security vulnerability,” and that it allows users to set their own video preferences.
Zoom also said it developed the local web server as a workaround to changes that were added in Apple’s Safari browser that prompted Zoom users to confirm if they want to launch the app each time they clicked on a meeting link.
“The local web server automatically accepts the peripheral access on behalf of the user to avoid this extra click before joining a meeting,” the company said — meaning Zoom essentially sidestepped browser security mechanisms to solve what it calls “poor user experience.”
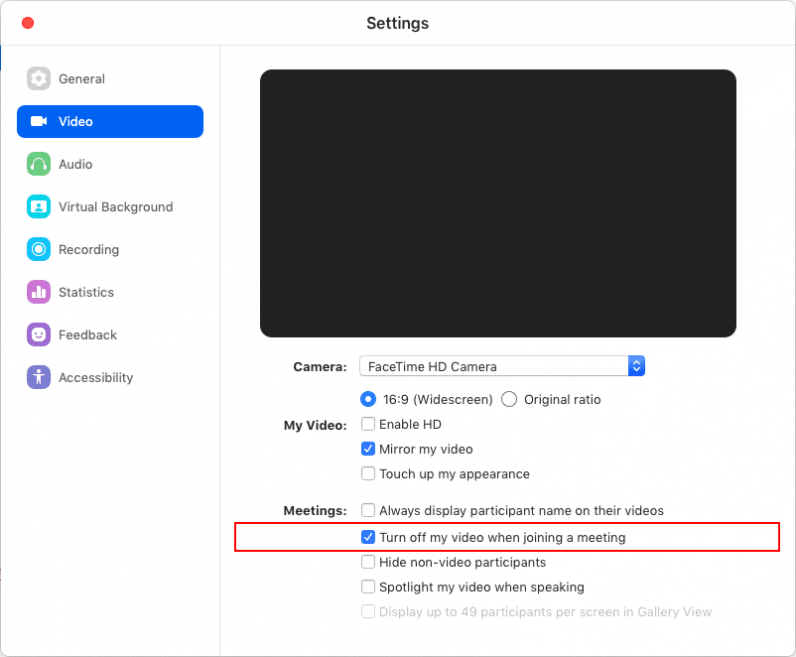
As a solution, the company — which went public earlier this April — plans to roll out an update this month that will save users’ and administrators’ preferences to turn on/off video when they first join a call.
But users who choose to keep the video option on will continue to be susceptible to malicious third parties as the company isn’t looking to fundamentally change the app’s behavior on Macs.
Instead the onus will be on you to turn your camera off by default.
It’s evident that Zoom has a tough problem on its hands as far as its Mac users are concerned — but it clearly isn’t doing a good job of keeping them safe from unsolicited calls, as bad actors could trick them into clicking links and enabling their video streams.
The company would do well to think of a better way to address this than leaving it up to users to prevent this from happening.
Update on July 10, 9:30 AM IST: In a surprise reversal, Zoom has decided to kill its controversial practice of using a local web server on Macs devices. It has also pushed an emergency patch to remove the server completely, but it acknowledged it didn’t currently have an easy way to uninstall both the client and the server.
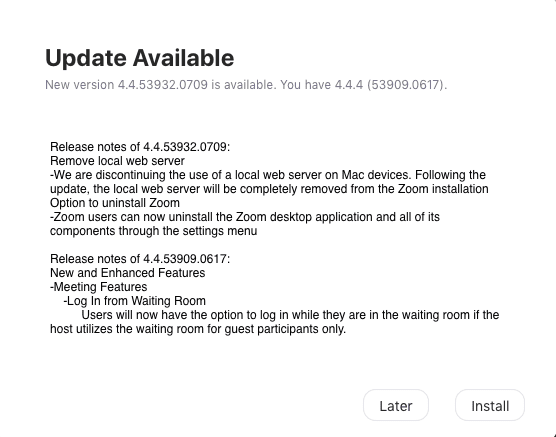
“We do not currently have an easy way to help a user delete both the Zoom client and also the Zoom local web server app on Mac that launches our client,” Richard Farley, Zoom’s chief information officer, said.
“The user needs to manually locate and delete those two apps for now. This was an honest oversight. As such, by this weekend we will introduce a new Uninstaller App for Mac to help the user easily delete both apps,” he added.
On Tuesday, the company had defended its use of a local web server, stating it enables users to join the meeting without having to do an extra click to get into a meeting. It also said it was a “legitimate solution to a poor user experience” due to changes Apple introduced in Safari 12.
Get the TNW newsletter
Get the most important tech news in your inbox each week.






