We all live in public, at least as far as the US National Security Agency is concerned. As Internet users and global citizens become more aware of surveillance activities that the US and other countries are doing on the World Wide Web, there are those who seek to ensure that privacy and personal freedoms aren’t trampled upon.
Tor technology aims to help appease privacy advocates and offer a way in which the Internet can be enjoyed without the prying eyes of surveillance programs or other tracking software. This free piece of software has certainly become mainstream in light of recent events, but what is Tor and why does it matter to you, your family, neighbors, co-workers, and the rest of the Internet?
Peeling back the onion layers
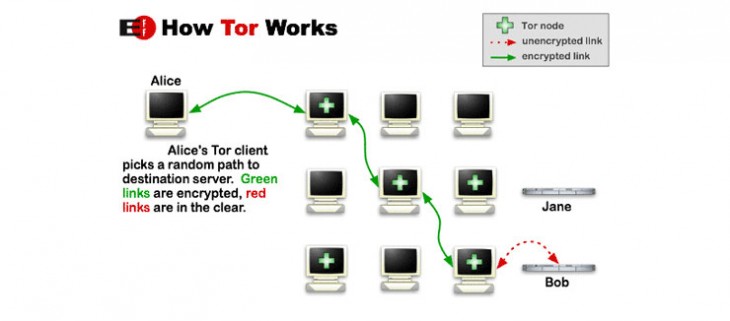
It might surprise you that the Tor Project, originally an acronym for The Onion Router Project, was initially funded by the US Naval Research Laboratory and helped launch the development of onion routing (anonymous communication over a computer network) on behalf of DARPA. It had also received the backing from the Electronic Frontier Foundation.
When users installed Tor software onto their computers, it would conceal their identity and network activity from anyone spying on their behavior. This was accomplished by separating the identification and routing information. The data is transmitted through multiple computers via a network of relays run by like-minded volunteers — almost like how users installed SETI software to look for extraterrestrial beings.
Tor isn’t the only service that helps you hide in the shadows away from the prying eyes of the federal government, or any other person who would do it for malicious purposes. However, some say that it’s better because it works at the Transmission Control Protocol stream level.
Diverse usage
With anonymized Internet usage, this opens up new opportunities for a variety of people, whether it’s for consumers who just want privacy, or for criminals, military personnel, activists and whistleblowers, businesses, journalists and more. Each of these groups has a specific mission to accomplish, but the end goal is the same — to do so with as little surveillance as possible.
So how does this affect what you, the average consumer, do online? It’s all about peace of mind, quite frankly.
Consumers will use Tor because it protects their privacy from marketers and potential identity thieves. If you’re wary about services like Google and Facebook tracking your online activity and don’t want unwanted ads because you know that cookies are involved, then Tor may be your solution. The Tor Project says that Internet Service Providers (ISPs) claim that they “anonymize the data by not providing identifiable information”, but a 2006 study highlights this as a myth.
Another said benefit is that you hide your location, which most services now prompt you for in order to provide personalized information and content. By hiding a user’s real IP address, this can, for example, help protect children from having predators find where they are, along with any bullies or stalkers.
Of course, if you’re researching sensitive information, being hidden might be wise. Say for example if you’re in China, searching the Internet or having discussions about Tibetan culture or Tiananmen Square, it would be prudent to avoid having spy organizations find you. This can apply to various countries of course, not just China.
Interesting fact: Silk Road, the online marketplace recently shut down by the FBI, utilized Tor’s services to protect destination IP addresses — we’ll discuss this a little later.
Not a panacea for security
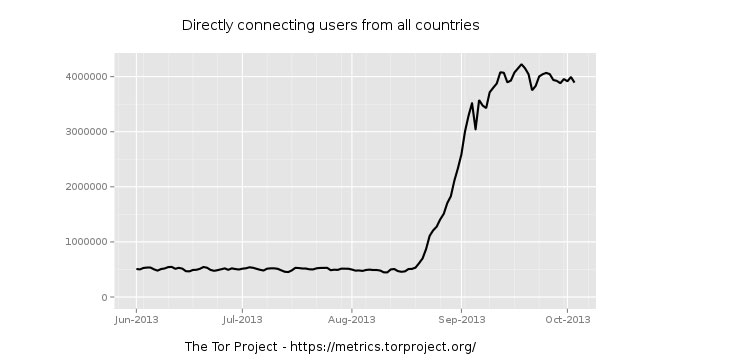
The NSA has surely helped raise the prominence of Tor over the past few months, thanks to former contractor Edward Snowden’s leak of classified data. Network security firm Sophos says that there’s been a huge surge in Tor usage since August — an increase from 550,000 to 1,200,000 users — surpassing its previous high of 975,000 in January 2012.
One would think that as the world begins to digest the effects the US’s Prism scandal has on its various governments, and maybe its citizens, this led to the increase in Tor usage. However, the project’s director Roger Dingledine doesn’t think it’s necessarily attributable to that, saying:
Anybody know details? It’s easy to speculate (Pirate Browser publicity gone overboard? People finally reading about the NSA thing? Botnet?), but some good solid facts would sure be useful.
Whatever the cause, it seems that people are using the software. But, it’s also important to note that Tor is by no means a foolproof solution to surf the Internet rather willy-nilly. We spoke with John Adams, a security researcher who has been following this development for some time, who tells us that there are limitations in what Tor can protect. He says that it will provide data encryption, but only during transit — specifically, when the data gets to the other end of the connection and leaves the exit node, it could pass along the Internet in plaintext, exposing the data to everyone, unless it was using https protocols.
In other words, if a destination website you’re connecting with has cookies, Javascript, or any sort of tracking information on the client, it can be de-anonymized over time. Tor will also not protect privacy if you have tracking plugins installed on your browser.
And let’s not forget about malware that could get installed. As the EFF notes: “Tor won’t defend you against Malware. If your adversary can run programs on your computer, it’s likely that they can see where you are and what you’re doing with Tor.”
Targeted for invasion … by the NSA
In 2007, Dingledine gave a talk at the NSA about Tor and spoke about its identity protection features. By the end of the meeting, he suspected that the agency was looking to find a way to penetrate the network — documents leaked by Snowden have confirmed Dingledine’s suspicions.
Is it surprising that the anonymity that Tor grants its users is something that national security organizations want to tap into? Yes, they’ll make claims saying that it’s not to spy on ordinary citizens, but it’s also crossing a very thin line about legitimacy. Is it right to monitor the entire Internet just to track a small subset who would do the country wrong? That answer is up to each individual to answer for themselves, but advocates like the EFF feel that the government should stay out.
American cryptographer, computer security, and privacy specialist Bruce Schneier penned a post showcasing how the NSA is trying to break into Tor’s network: Before it can use its computer network exploitation (CNE) capabilities, the agency needs to find Tor users. After discovering one, Schneier says that the NSA would use its network of secret Internet servers to redirect the user’s traffic to the government’s servers, codenamed FoxAcid, thereby “infecting” the user’s computer.
FoxAcid is an NSA system designed to act as a matchmaker between potential targets and attacks developed by the NSA, giving the agency opportunity to launch prepared attacks against their systems.
Once the computer is successfully attacked, it secretly calls back to a FoxAcid server, which then performs additional attacks on the target computer to ensure that it remains compromised long-term, and continues to provide eavesdropping information back to the NSA.
In the Snowden-leaked NSA presentation, entitled “Tor Stinks …” the agency acknowledges that it will never be able to de-anonymize all Tor users all the time. However, it does say that through manual analysis, it can reveal a “very small fraction” of Tor users.
Silk Road and denial of a back door
Last week, the Federal Bureau of Investigations (FBI) arrested Ross Ulbricht and shut down his Silk Road online marketplace. Ulbricht went by the username “Dread Pirate Roberts” and he was arrested for allegedly selling drugs, computer hacking conspiracy, and conspiracy to launder money. This Tor-enabled site soon went offline, but how did law enforcement find it?
The Tor Project published a statement soon after Ulbricht’s arrest seeking to reassure users that there were no compromises in its software or network. The FBI said that discovery of Silk Road happened as a result of “mistakes in operational security, and was found through actual detective work.”
Silk Road’s discovery is the most recent event to shine a spotlight on Tor software and expose it to public view. It probably gave pause to some users who felt that Tor had been working with the government, a claim that was leveled against companies like Microsoft, Yahoo, Google, Facebook, and Dropbox in the aftermath of Snowden’s Prism leaks.
Claims that it has a backdoor for the government are unfounded, according to the Tor Project. In its FAQ section, the organization says:
Nobody has asked us to put one in, and we know some smart lawyers who say that it’s unlikely that anybody will try to make us add one in our jurisdiction (U.S.). If they do ask us, we will fight them, and (the lawyers say) probably win.
We think that putting a backdoor in Tor would be tremendously irresponsible to our users, and a bad precedent for security software in general. If we ever put a deliberate backdoor in our security software, it would ruin our professional reputations. Nobody would trust our software ever again — for excellent reason!
But let’s also remember what we said earlier: Tor isn’t foolproof.
How to get started with Tor
Getting Tor set up is relatively easy — the browser bundle is free for anyone to install. Adams tells us that an average person can install the bundle and begin using the software. However, if you’re looking to add it to your server, it will require slightly more work, but that isn’t something that most people will need to do.
While most people aren’t installing Tor onto their servers, it’s somewhat preferred by the Tor Project as the more servers running it, the greater the anonymity and performance of the network.
The software is available for Windows, OS X, and Linux and offers support for a variety of languages, including German, Spanish, Italian, Korean, Dutch, Russian, Chinese, Vietnamese, and English.
➤ Download the Tor Browser Bundle
Photo credits: Alex Wong/Getty Images, How Tor Works infographic via Electronic Frontier Foundation, China Photos/Getty Images, Win McNamee/Getty Images,Patrick Lux/Getty Images, and Tor browser bundle via PC World
Get the TNW newsletter
Get the most important tech news in your inbox each week.