
This morning on Hacker News, members spotted a gaping security hole in Tumblr, which exposed more than 748 lines of sensitive configuration information out into the open. Members pointed to possible errors at the core of the PHP scripting language that might make the data dump inevitable. The error could have been a coding mishap, such as a missed opening PHP tag. Other coders felt that blaming PHP was unfair as security holes can be design as much as language.
The problem with PHP is that there’s no easy way of sharing state between requests. If you have a separate (ini-style) configuration file, every time you get a new request, the file will have to be read in from disk and parsed.
On heavily-loaded web servers this can be a significant performance issue. Configuration stored in a PHP file will be cached by your opcode cache and so doesn’t incur any per-request parsing/reading overhead.
The problem here is not that Tumblr stored their configuration in PHP. The problem is their lack of testing their changes.
Tumblr responded one hour ago:
A human error caused some sensitive server configuration information to be exposed this morning. Our technicians took immediate measures to protect from any issues that may come as a result.
We’re triple checking everything and bringing in outside auditors to confirm, but we have no reason to believe that anything was compromised. We’re certain that none of your personal information (passwords, etc.) was exposed, and your blog is backed up and safe as always.
This was an embarrassing error, but something we were prepared for. The fact that this occurred at all is still unacceptable, and we’ll be seriously evaluating and adjusting our processes to ensure an error like this can never happen again.
All in all- this morning’s Tumblr bug wasn’t catastrophic and it’s hopeful that users’ passwords weren’t compromised. The event seems likely equivalent to a Saturday morning hangover- the kind where you wake up exposing yourself to a stranger, wishing you’d used better protection.
A similar event occurred 3 years ago at Tumblr, which also made it into the Hacker News forum. In this instance, one user noticed that if you login to a personal Tumblr account then manually type in /admin, it directs you to the systemwide Tumblr admin page.
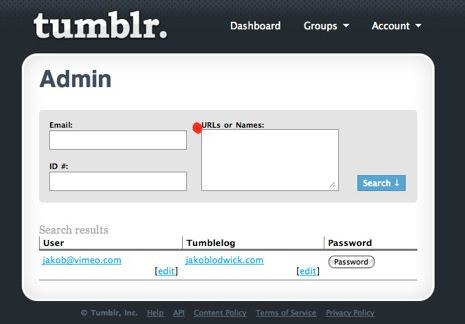
Members argued over whether or not the coding error should’ve been posted into the forum before or after notifying Tumblr. Unfortunately, Tumblr doesn’t provide an easy mail to address on its home page.
Thanks to friend and coder, @J2Labs who tweeted, “Omg… The Tumbeasts are spitting out passwords!” this morning.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





