A new trojan specifically for Macs has been discovered that installs an adware plugin. The malware attempts to monetize its attack by injecting ads into Chrome, Firefox, and Safari (the most popular browsers on Apple’s desktop platform) in the hopes that users will generate money for its creators by viewing (and maybe even clicking) them.
The threat, detected as “Trojan.Yontoo.1” by Russian security firm Doctor Web, is part of a wider scheme of adware for OS X that has “been increasing in number since the beginning of 2013,” according to the company. The security firm chose to underline Yontoo because it can download and install an adware browser plugin, making it slightly more modular as attackers could potential swap out the threat for an updated one or a different one entirely.
This particular trojan can get onto your Mac in multiple ways. Criminals have so far used movie trailer pages that prompt users to install a browser plugin, a media player, a video quality enhancement program, or a download accelerator. In other words, the usual schemes we’ve seen on Windows.
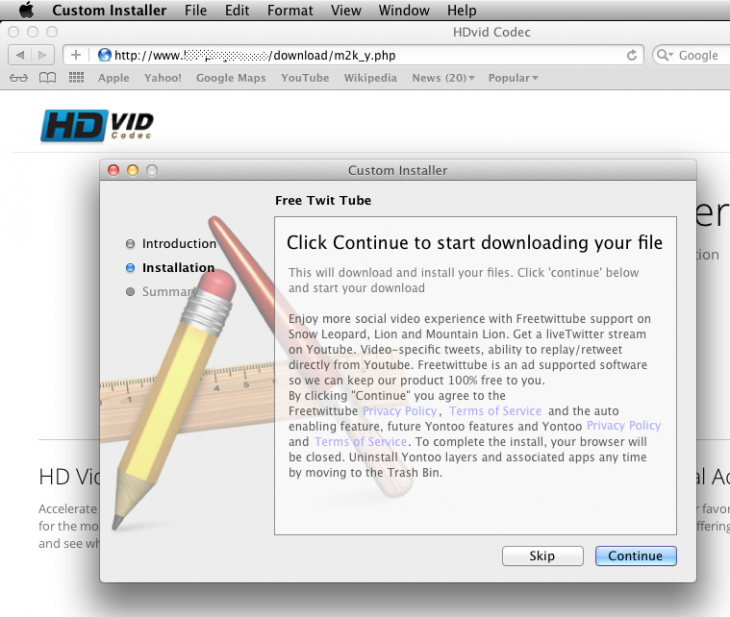
When launched, Trojan.Yontoo.1 prompts the user to install something called “Free Twit Tube” or something similar:
Instead of the claimed program, the Trojan downloads and installs the adware plugin for Chrome, Firefox, and Safari. When users surf the web, the plugin transmits information about the loaded pages to a remote server, and returns with a file that enables the trojan to embed third-party code into pages visited by the user.
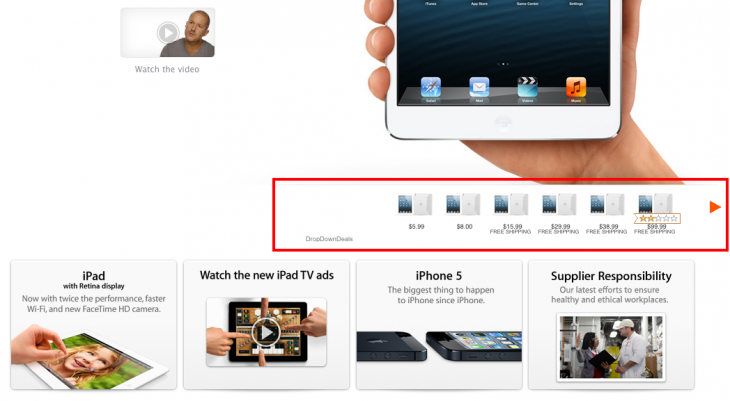
Doctor Web chose to use an Apple.com page displayed on an infected machine as an example. It’s not clear if this ad was generated automatically based on the contents of the page (most likely), or if it was selected specifically for Mac users visiting Apple’s website, but either way it seems to be very well chosen:
Doctor Web notes that adware is of course not limited to just OS X, as criminals naturally profit from affiliate ad network programs regardless of the platform. The company chose to analyse attackers targeting Macs, since “their interest in users of Apple-compatible computers grows day by day.”
Nevertheless, the security firm says “a similar scheme for spreading the Trojan is used to target Windows PCs,” although it wouldn’t detail if this included a trojan that downloads an adware plugin that targets say, Chrome, Firefox, and Internet Explorer.
Update on March 21 – According to Symantec, a Windows version Yontoo does indeed exist, although it reportedly doesn’t affect Windows 8 and is centered around Facebook ads. We’ve seen cross-platform malware before, but it’s interesting this threat seems to be tailored specifically to each platform, and furthermore it doesn’t seem to depend on Java.
Update on March 22 – In under 24 hours, Apple updates malware definitions to detect Yontoo adware for Chrome, Firefox, and Safari
See also – First OS X fake installer malware spotted, as SMS scams are ported from Windows and Android to Mac and Sophos declares 2012 the year of Android and Mac malware, as cybercriminals look beyond Windows
Top Image credit: asabird
Get the TNW newsletter
Get the most important tech news in your inbox each week.