Two weeks ago, Mac security software company Intego discovered malware which it classified as “a new Java backdoor trojan called Java/Jacksbot.A.” New threats are discovered all the time, but Intego later concluded that even though Jacksbot is a variant of the Java remote access tool (RAT) created by the jailbreaking group Redpois0n, it can target multiple platforms.
Intego first reported that the malware version it found is fully functional on Windows, and “partially functional” on OS X and Linux. Since at the time it was not known to have infected users and did not run without root permissions, the security firm classified it as “low risk.”
Yet new information this week from Trend Micro says that this threat has now been spotted in the wild: the company’s software has successfully cleaned two infection counts (one in Australia and one in Malaysia).
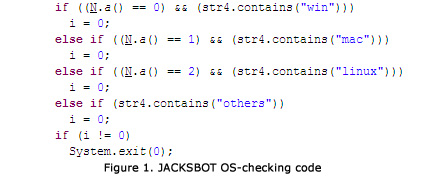
As you can see in the screenshot above, the malware checks the OS before continuing its rampage. Both companies agree, however, that Windows is the targeted platform, despite the fact the malware also works on OS X and Linux. Trend Micro has a theory as to why this is:
The malware writers behind JACKSBOT may just be testing the waters for a successful multiplatform malware; however for now they appear to be unwilling to invest the time and resources to develop the code more completely. It’s likely that the authors will continue to improve the code to fully support infection for OS X and Linux.
Intego first revealed that Jacksbot has the following capabilities:
- Gathering system information.
- Taking screenshots.
- Performing denial of service attacks.
- Deleting files.
- Stealing passwords (including specifically Minecraft passwords).
- Visiting remote URLs, likely to perform Clickfraud.
The malware is capable of visiting URLs, creating files and/or folders, running shell commands, as well as executing and ending programs. It can also steal information by logging keystrokes and mouse events.
Given the Minecraft password part, Trend Micro believes it is possible the malware presents itself as a Minecraft modification tool to unsuspecting users. The RAT can take control of the compromised system with some of the following backdoor commands: Chat, Corrupt, DeleteFile, GetFile, GetScreen, KillProcess, ListFiles, ListProcess, Restart, Shutdown, TakeFile, and VisitURL.
While Trend Micro has only detected two infections so far, the fact that malware authors have chosen the multiplatform route shows that they are in it for the long haul. Malware writers love exploiting Java because it’s simply more efficient: it allows them to target more than one operating system, more than one browser, and thus more than one type of user.
See also – Security companies are recommending you disable Java, or just uninstall it
Image credit: Musuvathi J Ubendran
Get the TNW newsletter
Get the most important tech news in your inbox each week.