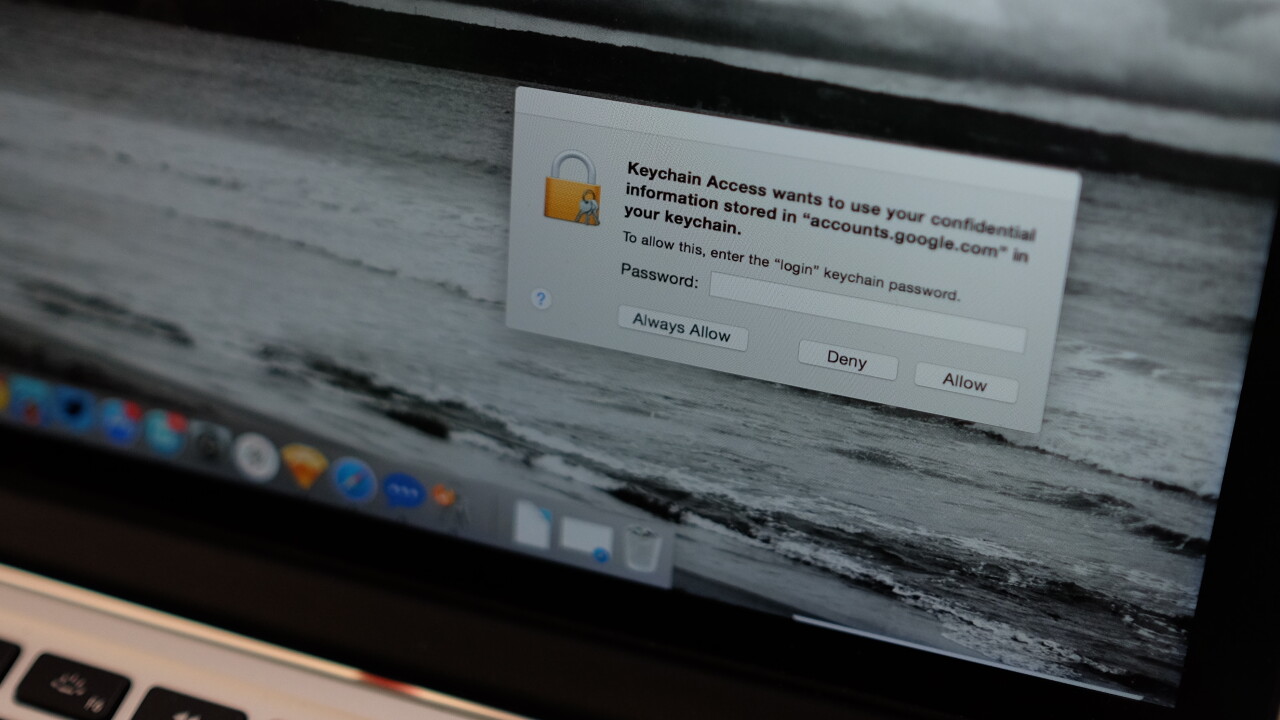
A new exploit discovered by researchers from Indiana, Georgia and Peking universities shows that the OS X Keychain, which stores all your passwords, is vulnerable to an attack that allows malicious apps to gather passwords.
The exploit, which is titled “Xara” utilizes cross-app resource access and works even within the OS X “sandboxed” app mode, which is designed to prevent such attacks.
Xara uses a method that hijacks the access-control mechanism used for Keychain access, to take control of passwords and other credentials added by legitimate apps and websites.
In the group’s research, it found that it was able to create a malicious app, successfully publish it on the App Store without detection and once installed attack many popular apps, including Google Chrome, Evernote and WeChat in order to access passwords in Keychain.
Using the vulnerability, the researchers were able to hijack Facebook and iCloud passwords, along with a slew of other apps/services stored in Keychain. It noted that “the attack can only succeed when the attributes of the victim’s keychain item are predictable” however many services share the same name across Keychain stores.
The problem boils down to there being no way to verify which app owns a credential in Keychain and the operating system does not check if saving a credential to another app’s keychain is suspicious.
There is some good news: the Keychain items you already have stored don’t appear to be susceptible to the exploit, only new ones that are created after a malicious app is installed.
Another attack as part of the exploit hijacks URL schemes that apps use to communicate with each other. Wunderlist, for example, uses the URL scheme “wunderlist://” to manage Google single-sign on, but a second app can register the same URL scheme and successfully steal Google’s private token.
The same exploit was also successfully used on other apps, like Facebook, to steal private app tokens. OS X does not check if apps are entitled to uses specific URL schemes.
The Register reports that Google’s Chromium team plans to pull support for Keychain from Chrome, citing an inability to solve the issue on its own. It’s unclear if support will return in the future.
When the group informed Apple of the vulnerability on October 15, 2014, Apple asked for six months to fix the problem, though both OS X 10.10.3 and 10.10.4 are still vulnerable to the attack.
The paper provides a number of recommendations, however Apple doesn’t appear to have implemented them yet.
We’ve reached out to Apple for comment and will update when we hear back.
➤Unauthorized Cross-App Resource Access on MAC OS X and iOS
Get the TNW newsletter
Get the most important tech news in your inbox each week.





