We reported earlier today on Lenovo bundling adware with some of its newer computers, but over the last few hours it’s emerged that the situation is worse than originally thought.
The software, named Superfish, was pre-installed by Lenovo on some consumer computers. The software injects unwanted advertising into users’ browsers in search results and on third-party websites.
This on its own is a big problem, but it’s emerged over the last few hours that the very same software self-installs a highly privileged security certificate that could allow the software — or other malicious attackers — to snoop on secure connections.
There is simply no reason for Superfish — or anyone else — to install a root certificate in this manner. These types of certificates are usually pre-installed by authorities such as Microsoft, Thawte or Verisign.
Either Superfish’s intent in installing one was malicious or due to sloppy development. Lenovo representatives previously reassured irate users on its forums that the software doesn’t gather any data, despite this huge security flaw.
#superfish pic.twitter.com/UVzMdbe9fe
— Chris Palmer (@fugueish) February 19, 2015
As pictured above, Superfish installs itself as a root certificate authority on the machine. A root certificate authority can impersonate any server’s security certificate as it is one of the highest trust levels on your machine; the computer assumes that the hijacking activity is fine, because it’s being done by a certificate with the right level of access.
Pictured below is the Superfish root certificate impersonating Bank of America’s security certificate on a user’s Lenovo computer. A number of similar images have been circulated showing similar behavior on other websites.
This is a problem. #superfish pic.twitter.com/jKDfSo99ZR
— Kenn White (@kennwhite) February 19, 2015
With these powers, Superfish could conceivably eavesdrop on any secure connection. We noted in our previous piece that Lenovo was “temporarily” suspending the Superfish partnership while it made some changes and would push updates to existing users. The update referred to in the post does not at time of writing remove the security certificate.
Usually, your browser will flag an insecure connection that’s not authentic with a warning, but because Superfish installs a root certificate authority, you won’t see such a warning.
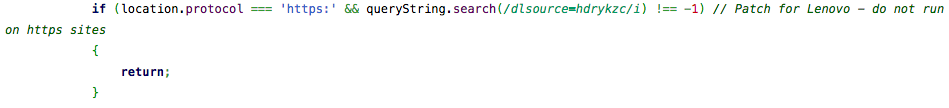
A piece of publicly available Javascript on the Superfish website includes the following line: “patch for Lenovo – do not run on https sites” which indicates the company is well aware of just how bad this problem is.
Unfortunately, it doesn’t end here. Because the root certificate authority appears to be signed with the same private key on every machine, anyone with the certificate is now able to extract the key and use it against these users.
One scenario already suggested online would be using that key to run a server that collects data from Lenovo computers connecting to a cafe hotspot.
Because affected machines trust the certificate and the private key is disabled, if a malicious user was able to get on the same network and run an attack like this, they could decrypt secure communications to whatever services the user accesses.
Removing the Superfish application is trivial, but removing the certificate is somehow not included in the uninstall process. The best course of action would be to perform a fresh install of Windows. This isn’t feasible for many, so you could attempt to manually remove the Superfish certificate as a next resort, following these steps:
- Search for “Certificate Manager” on your machine and open it.
- Navigate to Current User\Trusted Root Certificate Authority.
- Look for the Superfish certificate, right click and delete.
It’s unclear exactly which Lenovo systems have been affected; but it appears to be limited to consumer computers that were released in 2014.
We’ve contacted Lenovo for comment about Superfish, but we’re yet to hear back.
Update: Lenovo said to the BBC that it had “deactivated” the software on existing PCs and stopped installing it on new ones temporarily, but hasn’t addressed the certificate issue detailed here.
Update 2: Lenovo contacted us with the below statement and says that it has disabled the Superfish software and will not bundle it in the future. The company did not, however, respond to the root security certificate flaw and does not appear to have fixed it.
“Superfish was previously included on some consumer notebook products shipped in a short window between September and December to help customers potentially discover interesting products while shopping. However, user feedback was not positive, and we responded quickly and decisively:
1) Superfish has completely disabled server side interactions (since January) on all Lenovo products so that the product is no longer active. This disables Superfish for all products in market.
2) Lenovo stopped preloading the software in January.
3) We will not preload this software in the future.
We have thoroughly investigated this technology and do not find any evidence to substantiate security concerns. But we know that users reacted to this issue with concern, and so we have taken direct action to stop shipping any products with this software. We will continue to review what we do and how we do it in order to ensure we put our user needs, experience and priorities first.
To be clear, Superfish technology is purely based on contextual/image and not behavioral. It does not profile nor monitor user behavior. It does not record user information. It does not know who the user is. Users are not tracked nor re-targeted. Every session is independent. Users are given a choice whether or not to use the product. The relationship with Superfish is not financially significant; our goal was to enhance the experience for users. We recognize that the software did not meet that goal and have acted quickly and decisively.
We are providing support on our forums for any user with concerns. Our goal is to find technologies that best serve users. In this case, we have responded quickly to negative feedback, and taken decisive actions to ensure that we address these concerns. If users still wish to take further action, detail information is available at http://forums.lenovo.com.”
Top image credit: Gil C / Shutterstock.com
Get the TNW newsletter
Get the most important tech news in your inbox each week.