
Browsing through the depths of Reddit not so long ago, my eyes caught sight of an intriguing project called SpyPi: An (un)ethical hacking station specifically designed to educate people about the importance of data protection by putting them in the shoes of the attacker.
What impressed me even more though was that, despite the complexity and scope of the project, the device was entirely built by a high school student. In fact, the SpyPi was their graduation assignment – a requirement every student needs to fulfil before receiving their diploma.
Curious to find out more about this quirky contraption and the talent behind it, I reached out to the author of the Reddit post and asked them for more details.
“Nowadays technologies meet our needs in so many ways that we often ignore the dangers,” said Sarah, a 19-year-old student from Bern, Switzerland and the creator of the hacking station. “I created SpyPi as part of my graduation work. The motivation behind it was to create a new way of approaching data security.”
Sarah had spotted a disturbing trend in how the general public treats matters of data privacy. “People seem to feel a need for data security and privacy, but act carelessly at the same time. There of course are different reasons for such behaviors, but it is very concerning nonetheless.”
What turned her attention to the topic of data security was a recently introduced law that threatened to compromise the privacy of Swiss netizens in an unprecedented magnitude.
“In 2015, Switzerland voted on the new Nachrichtendienstgesetz law which allows security and intelligence agencies to collect even more data mainly on the pretext of terrorism,” she told TNW.
“During the voting, the nothing-to-hide-argument was omnipresent. I was shocked how easily people gave up parts of their privacy without questioning the whole thing. The law was adopted. I’ve had the impression many people voted on it without having enough information to actually deal with the topic.”

This is when the crafty high-school student saw an opportunity to change things for the better.
Instead of pursuing futile attempts to educate people by “spreading the word” or flooding them with jargon-heavy leaflets nobody reads, Sarah opted for an approach that put potential victims in the place of the hacker – so they could single-handedly see how vulnerable to data breaches everyone on the web is.
“Since talking to people didn’t work out in the past, my approach was to create a platform, which allows people to interactively get in touch with the topic,” she told me.
“To get people enthusiastic about IT is a challenging task. But there is one thing a lot of people have in common: The childhood fantasy of becoming a hacker.”
“That’s why I created a hacking station. SpyPi should allow people to find out why keeping data and their privacy save is important for themselves,” she continued. “To reach people on an emotional level, I’ve created different programs/attacks, that affect spheres of everybody’s daily life, such as payment, social networks and wireless networks.”
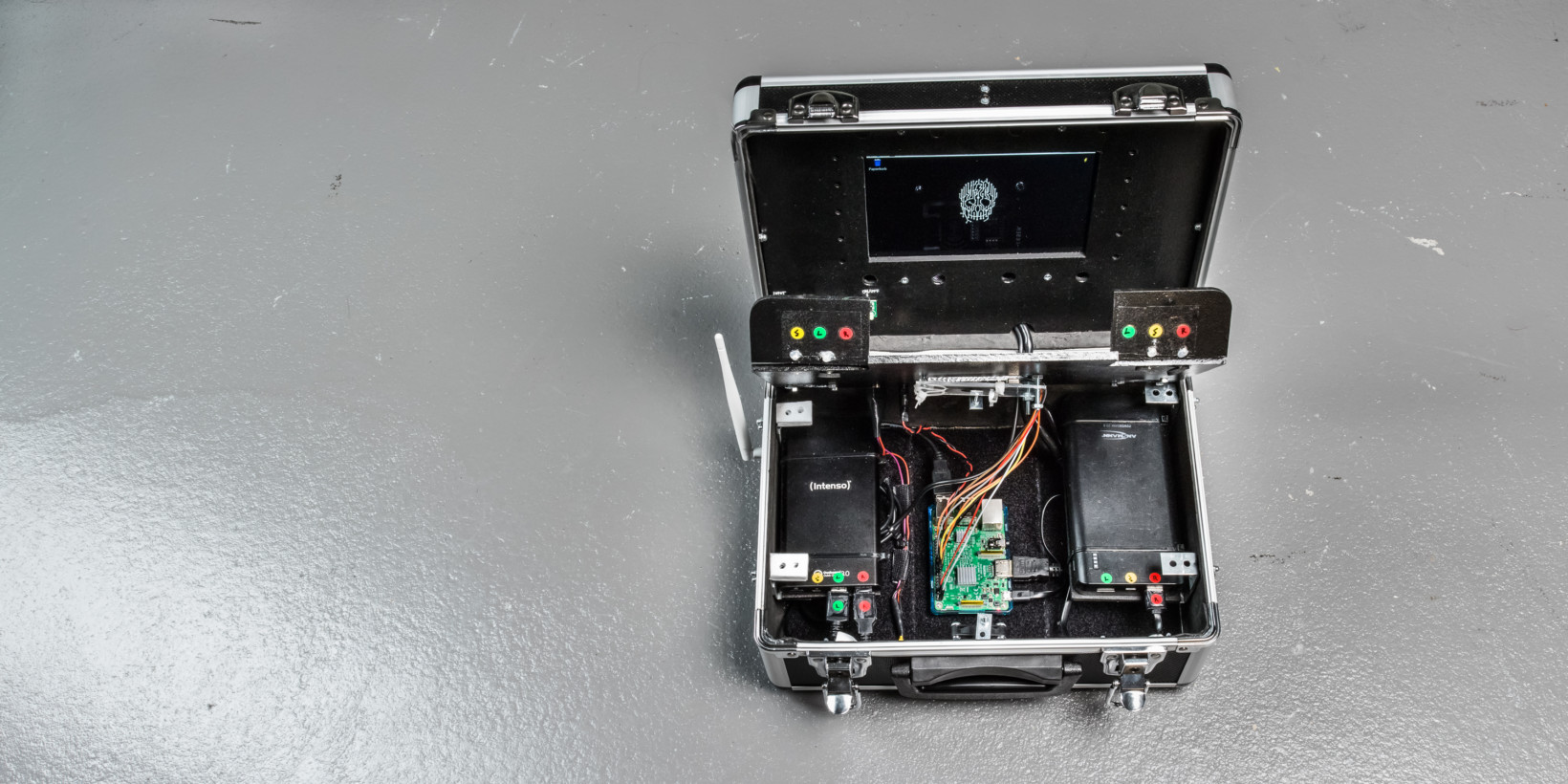
With this in mind, Sarah built five core features into the SpyPi in order to demonstrate the various ways in which data makes users vulnerable: A network scanner, a brute-force dictionary, an mitproxy data-catcher, an RFID spoofer, and a Twitter data-miner.
The network scanner, for instance, was programmed to display readily available information about your network and turn your attention towards certain easily-detectable weak points in your network setup, so you can patch them up before an attacker exploits them.
The brute-force dictionary was included to demonstrate how easy it is to crack unsafe passwords; the Twitter data-miner, on the other hand, showed how malicious agents can collect your publicly available information and turn it into data that reveals your (online) habits.
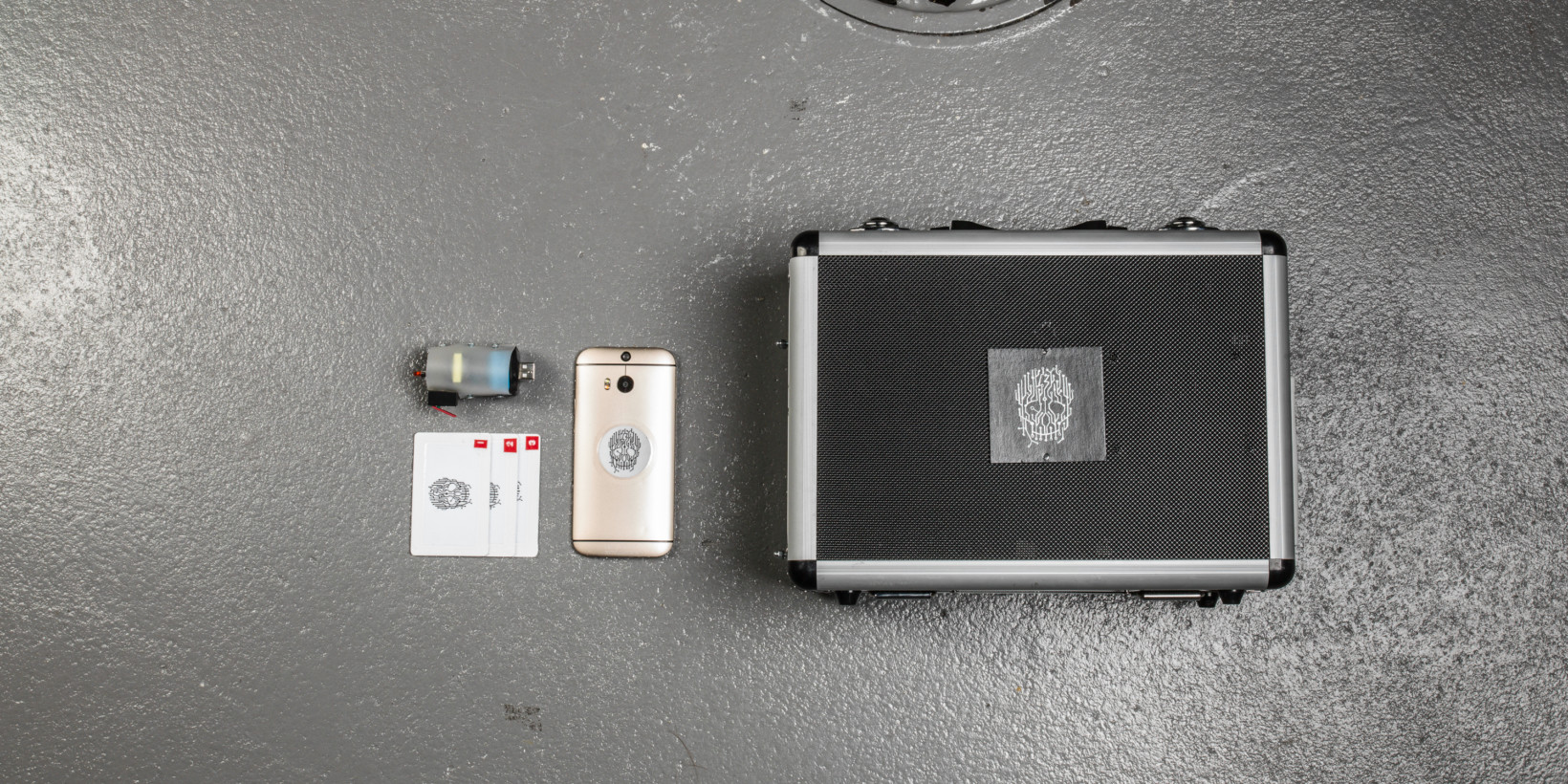
One additional component the student implemented in the hacking station was a self-destruction USB killer that would fry the machine, when plugged into one of its ports.
In case you were wondering, the SpyPi cost about $400 to put together. Among other things, Sarah used a Raspberry Pi 3 B single-board computer, a 7-inch mini-display, a mini mouse/keyboard solution, and an RC-522 RFID reader.
While Sarah designed the SpyPi for white-hat uses, she doesn’t hesitate to admit the tool could just as easily be used for malignant purposes. Indeed, she seems to take the same stance as Snowden on this matter: It is ultimately up to the user to decide how to use it.
All she out to accomplish with the SpyPi was to bring forth the importance of maintaining proper data security and privacy protocols in a more engaging and pro-active way – and on that count, the hacking station seems to do a pretty decent job.
Those seeking to know more about how Sarah built the SpyPi can find more details on the official page she set up for the project here. There is also a 70-page documentation (in German) for anybody interested in digging deeper into the technicalities. Drop an email to Sarah at spypi@gmx.ch for a copy.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





