If you’re using Google Drive, you probably received an email earlier this week about a new security update to the file storage and sharing platform. According to the email, “Drive will apply a security update to make file sharing more secure.”
True to the promise, the change is a security upgrade for some of the Google Drive files you might have shared in the past. It will make it harder for malicious actors to find shared files that you didn’t want to expose to the public.
But it doesn’t change anything about the fundamental security flaws of Google Drive’s link sharing feature.
Link sharing on Google Drive
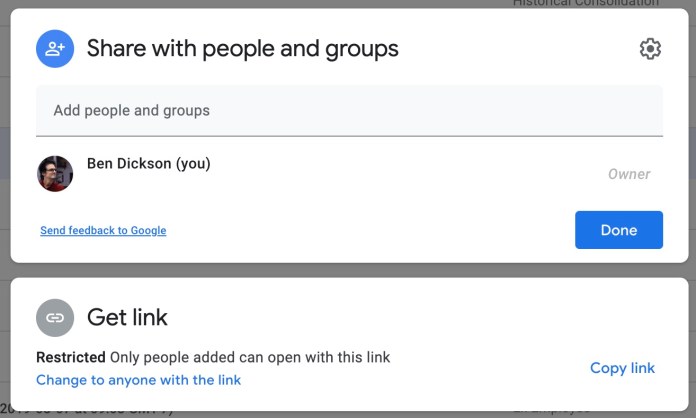
There are basically two ways to share files on Google Drive. The first is “restricted sharing.” In this mode, you must provide the email of colleagues and coworkers who should have access to the file. If they have logged into their Google Account, they will be able to access the file by browsing to its URL. Thankfully, in recent years, this feature is being displayed more prominently on the Google Drive sharing dialog.
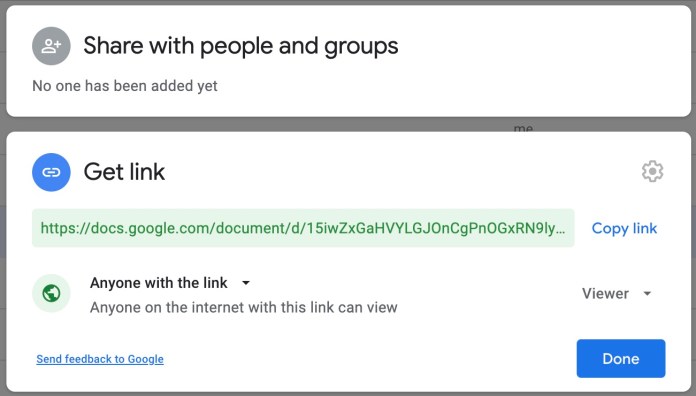
The second sharing mode, known as “link sharing,” provides access to anyone who has a link to the file. The advantage of link sharing, which makes it the go-to sharing mode for many people, is that it spares you from the pain of manually entering the email address of every single one of your colleagues. Just enable the link-sharing feature, copy-paste the link in your Slack channel, Trello, or other collaboration tools you’re using at your organization, and all your colleagues will be able to access it instantly.
But so can anyone else who has the link.
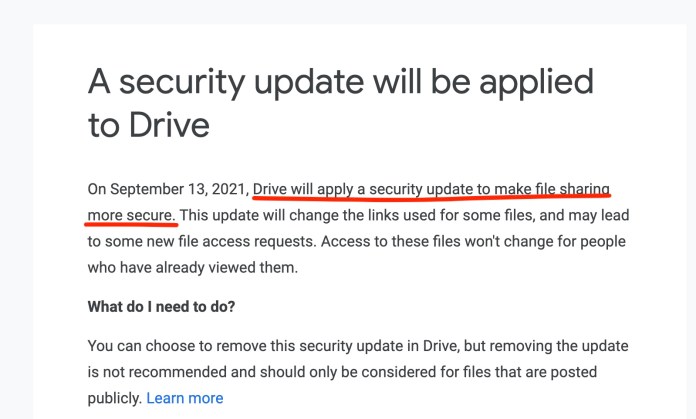
The new Google Drive security update
Google and other cloud storage services (Microsoft, Dropbox, etc.) generate unique URLs for each document you create. These URLs should be hard to guess. So, a malicious actor should not be able to stumble on a document by randomly generating a Google Docs address. But several experiments have shown that, in fact, many popular cloud storage services were previously vulnerable to URL-guessing attacks.
In such cases, if an attacker discovers the URL of a Google Drive file that happens to be made public through link-sharing, they will be able to access its contents. Note that if the same file is shared through the “restricted sharing” feature, then the attacker will only know of its existence but won’t be able to access its contents.
A few years ago, Google updated its address-generation scheme to make it more difficult to guess document URLs. However, if you have shared files from around early 2017, their URLs are still in the old format.
Google Drive’s new security update applies to these files. It will add an extra parameter to the shared document URL called “resourcekey.” People who had previously accessed the file will still be able to access it with the old link (without the resourcekey parameter). People who are accessing it for the first time will need to make an access request, which requires the approval of the file owner.
Basically, this means that if you had applied link-sharing to some old files in your Google Drive and forgot about them, the security update will prevent malicious actors from guessing their URLs and accessing them without you noticing it.
Google Drive link sharing is still a privacy disaster
Google Drive’s new security update makes brute-force link discovery has become harder. But there are still many other ways link-sharing can turn into a security and privacy disaster.
Google Drive link sharing is a prime example of “security by obscurity,” which means your data is safe only because other people don’t know about it, not because they don’t have access to it. Here are a few examples of how a shared file can be exposed to unwanted users:
- Former employees who have the document’s link will still be able to access it after they leave your organization.
- A negligent employee accidentally tweets the link, emails it to unintended recipients, or backlinks to it in another public document.
- The document is discovered through URL referrals.
None of the above (and the many other ways that a shared link can be discovered) require the brute-force discovery of your document’s URL address.
I’m not against Google Drive link sharing. It is not a problem if you’re not handling sensitive data. In fact, many people use the link-sharing feature with Google Docs to make public statements or to publish reports.
The problem is that people often use link sharing to collaborate on confidential documents. In such cases, their data remains safe as long as the link to the shared document is not broadcasted anywhere or leaked to unwanted parties. And there’s no guarantee of it not happening.
More work to be done
In the past few years, the Google Drive interface has gone through some improvements to reduce the possibility of users accidentally sharing their documents with unwanted parties. But the confusion around link sharing remains.
There should be a clear distinction between sharing and publishing. When you share a document, it should be limited to the intended recipients and inaccessible.
When you publish a document, you’re making it available to everyone, even if you don’t publicize its URL or expose it to search engines.
Unfortunately, the link-sharing feature in Google Drive (and other platforms) is a publication feature disguised as sharing. It’s misleading and insecure, and I wish Google changed its name and separated its user interface from that of the restricted sharing feature.
But while Google is fast busy discussing and implementing my recommendations (hopefully), please don’t use link sharing unless you’re fine with the content of your document becoming public knowledge. (If you want to share a single document with a large group of users without entering every single one of their emails, use Google Groups instead.)
This article was originally published by Ben Dickson on TechTalks, a publication that examines trends in technology, how they affect the way we live and do business, and the problems they solve. But we also discuss the evil side of technology, the darker implications of new tech, and what we need to look out for. You can read the original article here.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




