
The infamous FinFisher cyber espionage tool has gone mobile, malware style. Multiple mobile Trojans for the Android, iOS, BlackBerry, Symbian, and Windows Mobile platforms have been discovered as have many Command and Control (C&C) servers around the world that they communicate with. Security researchers from the University of Toronto Munk School of Global Affairs‘ Citizen Lab (via The Financial Post) have published an extensive report detailing their findings.
The malware is designed to spy on you via your phone. It can monitor your apps, emails, text messages, and voice calls. It can phone home to send data as well as get further instructions. It can track your location.
While FinFisher is described as surveillance software developed by U.K.-based Gamma Group, what we’re talking about here is malware. The researchers say the discovered “tools” are consistent in functionality with documentation for the FinSpy Mobile product, a component of the FinFisher toolkit.
Your phone can get infected if you are tricked into downloading the spyware, which can be disguised as something other than FinSpy. You don’t even have to be using your browser: it can come via a text message that looks like it’s from your cellular provider, asking you to install an app or perform a system update.
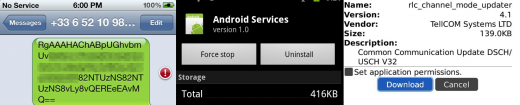
The Android version of this threat comes in the form of an APK that installs itself as “Android Services.” It requests a massive slew of permissions:
- Access_Coarse_Location
- Access_Fine_Location
- Internet
- Read_Phone_State
- Access_Network_State
- Read_Contacts
- Read_Sms
- Send_Sms
- Receive_Sms
- Write_Sms
- Receive_Mms
- Receive_Boot_Completed
- Process_Outgoing_Calls
- Access_Network_State
- Access_Wifi_State
- Wake_Lock
- Change_Wifi_State
- Modify_Phone_State
- Bluetooth
- And_Receive_Wap_Push
One of the samples calls home to C&C servers located in the Czech Republic and the U.K.
The iOS threat was developed for Arm7, and appears to work on iOS 4.0+, meaning the iPhone 4, iPhone 4S, iPad 1, iPad 2, iPad 3, as well as the iPod touch 3 and the iPod touch 4 are all affected. The bundle is typically called “install_manager.app.” Multiple references to “FinSpy” are all over the binary, and it appears that a developer’s certificate belonging to Martin Muench, Managing Director of Gamma International and head of the FinFisher product portfolio, was used. The malware makes a point to keep itself from being wiped upon a reboot of an infected iOS device. The threat can perform arbitrary data exfiltration, SMS interception, and so on.
The BlackBerry threat is a complex .code file. It can manipulate BlackBerry apps, access crypto libraries, and access other phone functionality such as sending SMS messages. The malware can call home to Germany and Indonesia. It asks for a slew of permissions:
- USB
- Phone
- Location Data
- Internet
- Wi-Fi
- Cross Applicaiton Communication
- Device Settings
- Media
- Application Management
- Themes
- Input Simulation
- Browser Filtering
- Recording
- Security Timer Reset
- Organizer Data
- Files
- and Security Data
The malware can log and manipulate phone events, and can even accept a silent call so that the attacker can listen to a conversation in the infected phone’s vicinity. It can also record sent and received email messages, record BBM messages, listen for both incoming and outgoing SMS messages, and even monitor WhatsApp.
The Symbian threat calls itself “System Update” or “Installation File.” The former requests the following capabilities:
- PowerMgmt
- ReadDeviceData
- TrustedUI
- SwEvent
- NetworkServices
- ReadUserData
- WriteUserData
- Location
The Trusted UI one is interesting because it is only specifically used when confidentiality and security are critical. In other words, most apps don’t ever touch it.
The Windows Mobile threat provides interception and monitoring capabilities (Windows Phone appears unaffected). Depending on the status of the device or monitored events, the malware communicates notifications back to the C&C server. It uses the following modules:
- AddressBook
- CallInterception
- PhoneCallLog
- SMS
- Tracking
The malware can thus manipulate phone calls as well as track the device using GPS.
In addition to their app analysis, the security researchers also scanned the Internet for where FinSpy C&C servers could be operating. They found two servers in Brunei, one in Turkmenistan’s Ministry of Communications, two in Singapore, one in the Netherlands, a new server in Indonesia, and a new server in Bahrain. There are new ones in certain countries because Rapid7 previously found C&C servers for FinFisher in 10 countries: Indonesia, Australia, Qatar, Ethiopia, Czech Republic, Estonia, Mongolia, Latvia, the UAE, and the U.S.
Despite all this worrying information, there’s good news. While these Trojans provide substantial surveillance functionality, there is no evidence of them exploiting the aforementioned mobile platforms on their own. As such, cybercriminals will need to figure out how to leverage an existing exploit, or use social engineering to get on your device. Alternatively, they can also physically access your phone.
To protect yourself, here’s what the researchers suggest you do:
We recommend that all users run Anti-Virus software, promptly apply (legitimate) updates when they become available, use screen locks, passwords and device encryption (when available). Do not run untrusted applications and do not allow third parties access to mobile devices.
In other words, stay clear of any apps that ask for far too many permissions to install, and always keep your phone on you and away from those who may want to track you.
Image credit: stock.xchng
Get the TNW newsletter
Get the most important tech news in your inbox each week.



