
Etherscan, the most widely used Ethereum blockchain explorer, has quickly patched security vulnerabilities overnight as hackers exploited certain parts of its service.
Hackers successfully manipulated the Disqus API – a third-party service used by Etherscan that allows for comments to be left on Ethereum wallet addresses. They were able to execute a Cross Site Scripting (XSS) attack to inject JavaScript code into its interface that forced a spooky message to pop-up for its users.
It simply read: ‘1337’ – which is ‘leetspeak’ for ‘elite,’ a pseudo-language popular at the dawn of the internet which replaced English letters with ASCII symbols. Users were quick to share the relevant code:
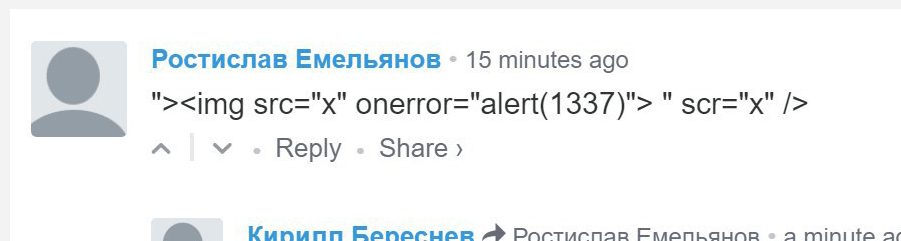
While it would have appeared as though the messages were coming from the Etherscan service itself, devs report that no harmful code was sent to users. The team were also prompt to disable related functionality while the security holes were plugged.
Michael Hahn, programmer for popular Ethereum interface MyCrypto.com and Etherscam.db, added this in a reddit post:
An XSS attack, in this case javascript injection, was taking advantage of API that Etherscan uses to grab the latest comments about addresses from the Disqus CMS. It doesn’t appear that Etherscan had been serving malicious code when it was noticed. Disqus comments on Etherscan.io were disabled until a security patch is pushed which will encode the API data to remove the vulnerability to XSS. No user funds were lost.
Being able to show unauthorized comments to users under the guise of an official message is precisely what can lead to widespread phishing. Unsuspecting users could be tricked into handing over private keys or sensitive information, unaware that they were not interacting with Etherscan officially. Luckily, in this instance, they were just shown an annoying pop-up.
Although this particular attack does seem to be innocuous – JavaScript injections like these are often part of a wider plan to penetration test (pentest) a service in preparation for further exploitation.
An quick update on the random "1337" script pop up on https://t.co/VAEURQyNAG https://t.co/3N222GMucu
— Etherscan.io (Not giving away Ether) (@etherscan) July 23, 2018
Analysis shared by Etherscan also seems to back this up – there were four attempts in total – the last of which was an attempt to ‘inject’ a web3.js transaction into the Etherscan service.
There were 3 attempts to inject the JS alert message “1337”. The first appeared non malicious with the second 2 coming from someone we know (most likely experimental). The 4th attempt tried to inject a web3.js tx but this was blocked (truncated) by our backend.
Web3.js is the Ethereum JavaScript library. It is precisely this library that allows for browser extensions like MetaMask to process cryptocurrency transactions over the Ethereum blockchain.
We have reached out to Etherscan for clarification as to the ramifications of an unauthorized web3.js injection, and will update this story accordingly should we hear back.
This is just the latest in a series of recent attacks suffered by the Ethereum blockchain. Earlier this month, MyEtherWallet (MEW) users who were running the Hola VPN extension were urged to move all of their cryptocurrency out of their MEW wallets following a sustained, five-hour long hack.
Two months earlier, Amazon’s DNS service was hijacked, leading to the redirection of MEW users to an exact replica of its official website – one created purely to steal the private keys of users and eventually lead to the loss of over 200 ETH in just a few hours.
So, while there has seemingly been no damage done in this instance – just an annoying pop-up – there may be more attacks on the way. In any case, it’s certainly a good time for a refresher on strategies to avoid being phished – and a reminder to never hand over your private keys to anybody, ever.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





