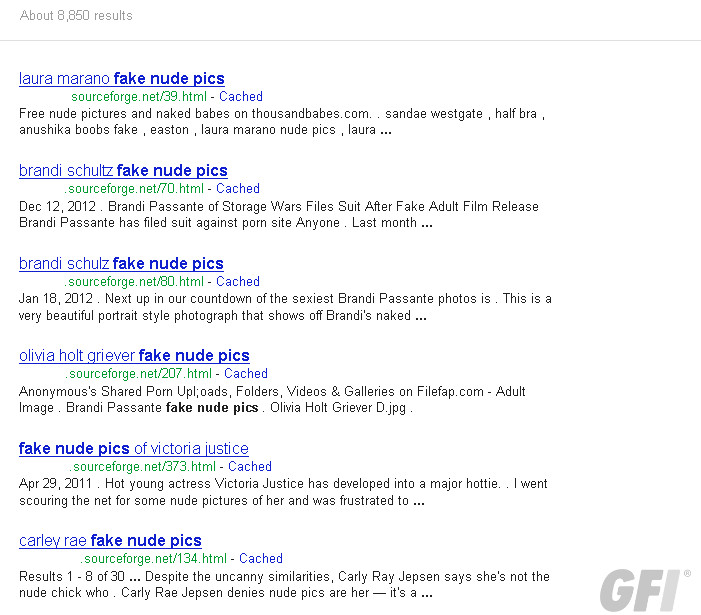
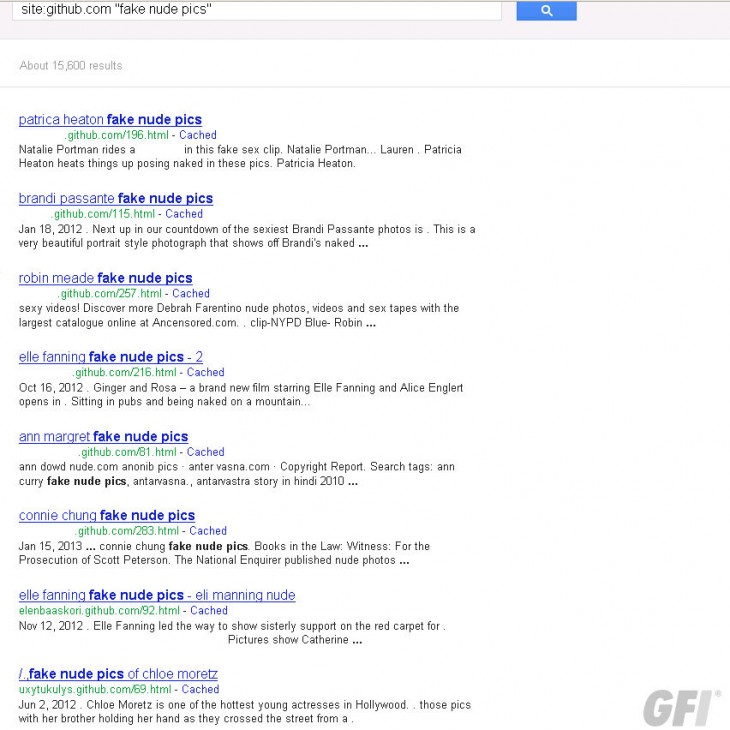
Online criminals have launched “a large and determined” spam campaign pushing malware that is hosted on GitHub and SourceForge pages. They are using the Stamp EK exploit kit to infect computers by baiting innocent victims with promises of YouTube videos and “fake nude pics” depicting US news reporters, film actresses, singers, and even wrestlers.
The discovery comes from the security firm GFI Labs, which says it first saw threats start creeping up on SourceForge back in 2011. The ransomware aspect is new (one of the threats is detected as Trojan.Win32.Agent.akmt), and so is using GitHub. Using legitimate websites for hosting malware reduces the chance that victims will become suspicious.
Here’s how SourceForge is doing:
Here’s GitHub:
Clicking on any of the accompanying links leads to either a fake YouTube page or a site filled with sexually explicit pictures lifted from a pornography site. GFI has also seen fake air rifle stores, a Windows for Dummies site, and Twitter pages.
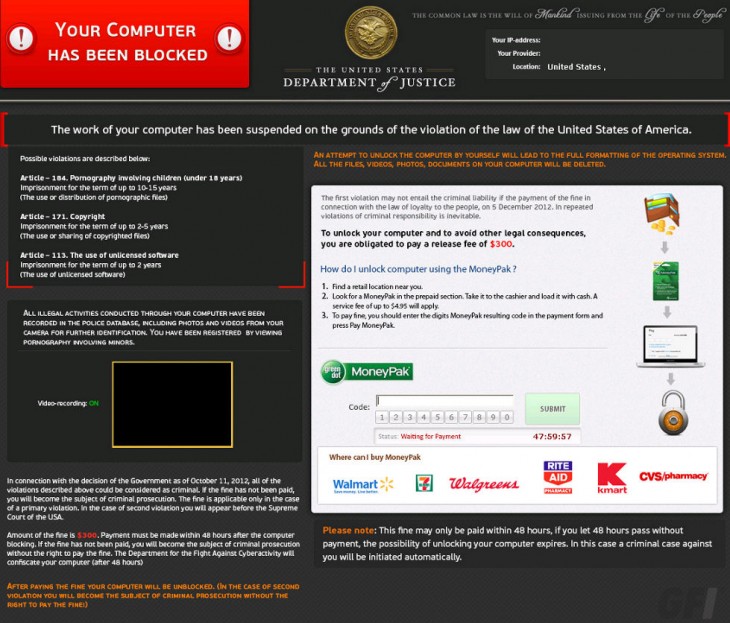
At this point, ransomware is dropped onto the user’s computer. For those who don’t know, ransomware is malware which restricts access to the computer it infects, spamming the user with prompts that demand a ransom paid for functionality to be reinstated. Access is limited either by encryption, as in this case, or locking the system.
In this case, more than one type of ransomware variants are being pushed to victims’ computers. Here is one example:
This one is demanding $300 to “Unlock your computer and avoid other legal consequences.” Users are being accused of accessing illegal pornography and are being threatened to pay up “or else.”
For those who fall for this scheme, never pay the ransom. If you don’t know how, have a friend clean out your computer.
We have contacted GitHub and SourceForge about this so they can get the issue sorted. We will update this article if we hear back.
Update at 9:00PM EST: A SourceForge spokesperson has replied. The company issued a lengthy statement which you can read in full below.
We are aware that unauthorized persons have been abusing the name and brand of SourceForge to promote unauthorized malware. This particular form of a malware trap, the so-called Stamp EK exploit kit, seeks to infect computers by baiting victims with the promise of fake celebrity nude images and videos. The exploit in question leads victims to fake sites, where their PCs are then infected with the offending malicious ransomware. First, we would like to state that no malware in this instance was hosted on SourceForge. Second, we are working to make sure these links are removed from any search engines or other online reference points in every effort to spare other potential victims of the threat. Our mission at SourceForge is to be the trusted name in open source software. We work with our community of open source developers and users to host and distribute hundreds of thousands of software projects every day. We will continue to work on this issue until it is fully resolved and will do everything in our power to make sure we remain true to our mission.
Image credit: Darren Deans
Get the TNW newsletter
Get the most important tech news in your inbox each week.