Security firm Check Point has unearthed a new case study detailing how more than €36 million ($47 million) was stolen from more than 30,000 corporate and private banking customers across Europe. The cybercriminals behind the schemed conducted a highly sophisticated attack featuring malware infecting both PCs and mobile devices. Check out the full 18-page whitepaper (PDF) or read on to get the shorter version.
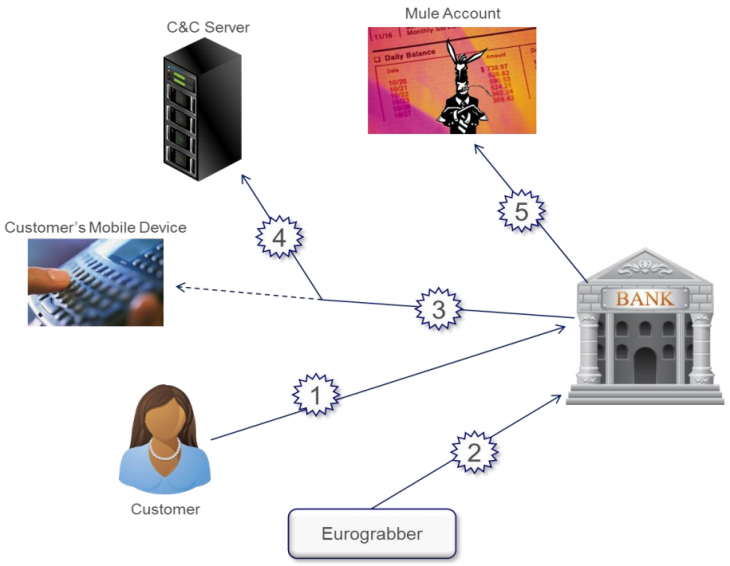
Called Eurograbber, the attack targeted banking customers using a sophisticated combination of malware directed at computers and mobile devices and a Command and Control (C&C) server. The attack used the Zeus Trojan, a very popular threat designed to log your keystrokes.
First it infected victims’ computers, and then it infected their mobile devices (Android and Blackberry smartphones) in order to intercept SMS messages to bypass the banks’ two-factor authentication process. Using the stolen information and the transaction authentication number (TAN), the attackers then performed automatic transfers of funds from the victims’ accounts to mule accounts across Europe.
The transfers ranged anywhere between €500 and €250,000, and quickly added up to the tens of millions. The attacks originated in Italy, but Check Point says they quickly spread to Germany, Holland, and Spain.
“Cyberattacks have become more sophisticated, more creative, and more targeted than ever before,” said Eran Kalige, Head of Security Operation Center, Versafe. “As seen with Eurograbber, attackers are focusing on the weakest link, the people behind the devices, and using very sophisticated techniques to launch and automate their attacks and avoid traceability.”
As online and mobile banking become more and more popular, targeted attacks like this one will become more and more common. There is no easy way to prevent them, but security needs to be kept at the forefront for everyone involved: the customers and their banks, as well as the vendors of all the software involved.
Image credit: Alberto Villén
Get the TNW newsletter
Get the most important tech news in your inbox each week.