
Researchers from cybersecurity firm ESET have uncovered a malicious version of the Tor browser – the program used to access the dark web – and it’s been stealing user’s Bitcoin.
According to ESET, the bad actors were able to steal more than $40,000 worth of Bitcoin. But how?
The scammers have been using a trojanized version of an official Tor browser package. The bad browser redirects users to two websites which claim the user’s version of Tor is out of date. Researchers say this happens even if the browser is the most up-to-date version.
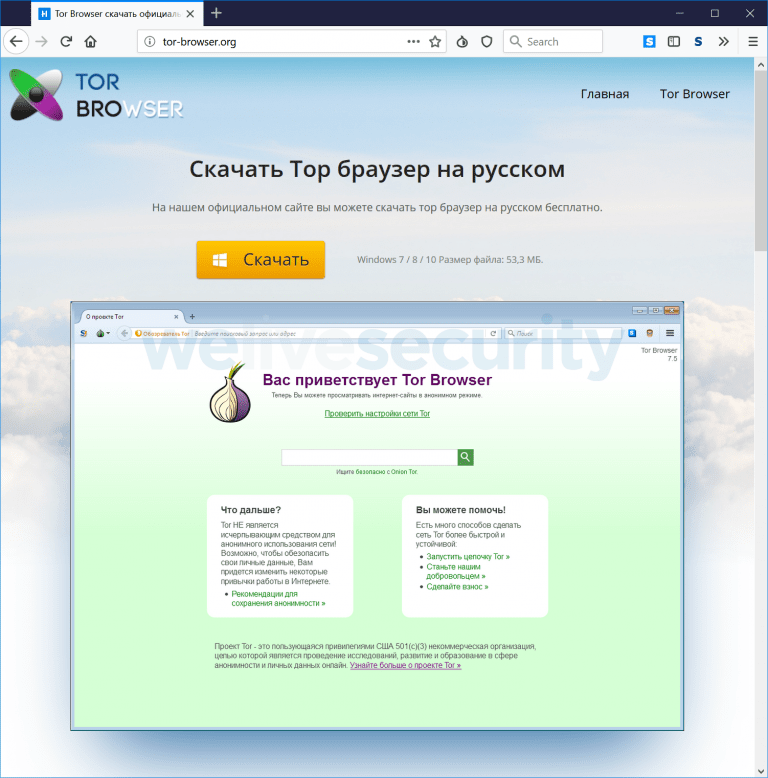
When a user clicks on the “update” link on the nefarious page, they are redirected to another website where they are told they can download an update.
ESET says these websites and the malicious Tor browser was promoted in 2017 and early 2018 – during the infamous cryptocurrency bull run – on various Russian forums. The fake browser claimed to be the official Russian language version of Tor.
The scammers also used Pastebin accounts to promote their fake Tor websites, and encourage users to download the software to evade government surveillance. The associated Pastebin accounts have been viewed more than 500,000 times.
When users of the infected browser went to add funds to their Bitcoin wallet or pay for items on dark web marketplaces, the browser would change the target wallet address to one controlled by the scammers.
ESET researchers identified three Bitcoin wallets used in this campaign. At the time of writing the wallets had received 4.8 BTC, about $40,000.
For all intent and purpose, the infected browser is exactly the same as the legitimate Tor browser, so there is little to suggest to the user that something might go awry.
While using malware to switch out Bitcoin wallet addresses is nothing new, embedding that functionality in a browser is less common.
It’s quite a savvy strategy, too. To access dark web marketplaces you must used Tor (The Onion Router). The cyberbaddies knew there’s a high probability that Tor users will probably use Bitcoin aswell.
If there’s something to be learned from this it’s to always download software from legitimate sources and keep it up to date.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




