A dangerous new wave of cryptocurrency mining malware has struck the internet, and it has already infected thousands of high-value enterprises across Asia.
Known as “Beapy,” the malware uses leaked NSA exploits and hacked credentials to spread through exposed networks as quickly as possible. It’s even capable of infecting patched machines.
Cybersecurity research firm Symantec, which has been tracking the threat, reports Beapy is a file-based coinminer that uses email as an initial infection vector.
“This campaign demonstrates that while crypto-jacking has declined in popularity with cyber criminals since its peak at the start of 2018, it is still a focus for some of them, with enterprises now their primary target,” it added.
Symantec first recorded Beapy in January 2019. Activity has reportedly increased since the beginning of March.
This is how Beapy infects and spreads its malware
Beapy’s initial attack vector is malicious Excel spreadsheets distributed in emails, at least in some instances.
If a recipient opens the attachment, a secondary NSA-built exploit known as DoublePulsar is downloaded, which was used by the epic WannaCry ransomware attackers that shook the world in 2017.
DoublePulsar is responsible for opening a backdoor on infected machines, allowing for commands to be executed remotely by the attackers.
“Once DoublePulsar is installed, a PowerShell command is executed, and contact is made with the Beapy command and control server, before a coinminer is downloaded onto the target computer,” said Symantec.
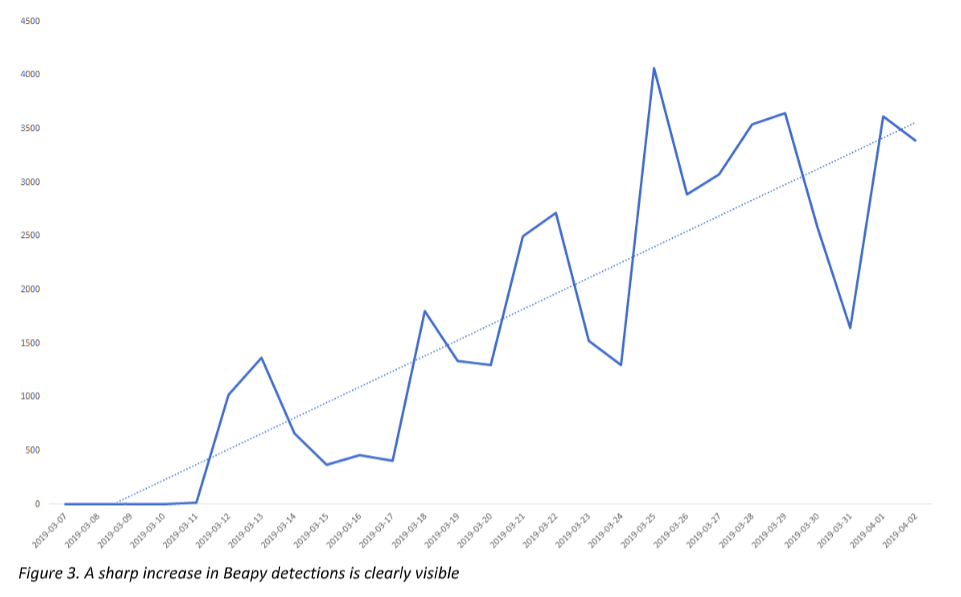
The malware then uses another famous exploit, EternalBlue, to spread throughout networks – but it isn’t Beapy’s only propagation technique.
The researchers observed it using credential-stealing tool Hacktool.Mimikatz on infected computers, which allows Beapy to spread to machines that have been patched against EternalBlue.
“Beapy also uses a hardcoded list of usernames and passwords to attempt to spread across networks. This is similar to how the Bluwimps worm operated,” said Symantec. “Bluwimps infected thousands of enterprise machines with coinminers in 2017 and 2018.”
Symantec detected an earlier version of Beapy hidden on a public-facing web server. The worm was attempting infections by generating a list of IP addresses of connected computers.
“The version of Beapy seen on the web server is an early version of the malware, coded in C rather than Python, like later versions,” Symantec revealed. “However, the activity is similar, with the downloaded malware also containing Mimikatz modules for credential harvesting, as well as EternalBlue exploit capabilities.”
Beapy has wormlike capabilities
Symantec researchers found almost all of Beapy’s victims are enterprises, which they say could indicate continuation of previous malware trends which saw crypto-jacking criminals shift towards hacking enterprise networks.
“While we have no evidence these attacks are targeted, Beapy’s wormlike capabilities indicate that it was probably always intended to spread throughout enterprise networks,” said Symantec.
“This mirrors a trend we saw in ransomware in 2018 too when, despite a drop in overall ransomware infections of 20 percent, ransomware infections in enterprises increased by 12 percent,” Symantec continued. “Enterprises appear to be an increasing focus for cyber criminals.”
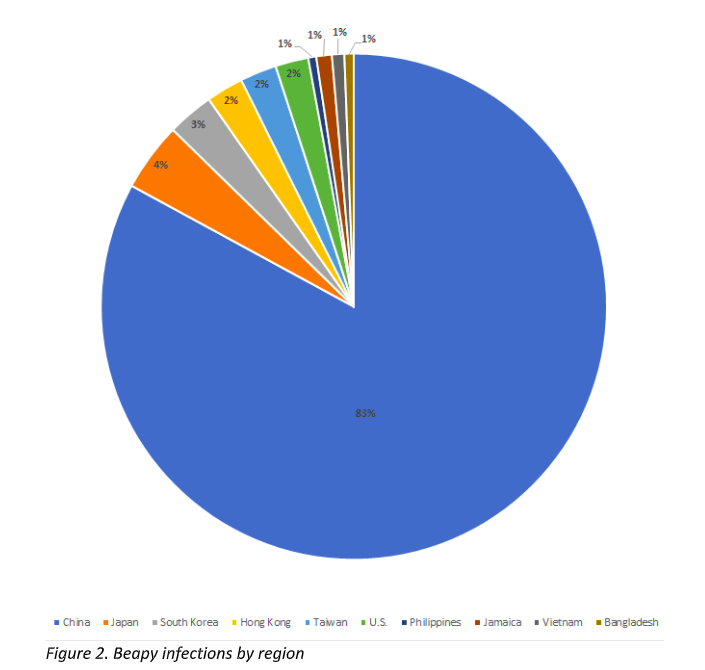
Until now, 98 percent of recorded Beapy infections were enterprise machines, and 83 percent were located in China.
“Beapy is a file-based coinminer, which is interesting as most of the crypto-jacking activity we saw at the height of its popularity was carried out using browser-based coinminers, which were popular due to lower barriers to entry and because they allowed even fully patched machines to be targeted,” said Symantec.
Beapy mines Monero cryptocurrency faster than CoinHive
Symantec threat intelligence analyst Alan Neville told Hard Fork they had observed infected machines downloading cryptocurrency miner XMRig from the attacker’s own infrastructure.
“We believe that the attackers are mining Monero, as we observed a miner called XMRig being downloaded – this is specific to Monero,” Neville confirmed. This software has been featured in previously reported malware threats.
Symantec noted file-based coinminers like XMRig mine cryptocurrency significantly faster than browser-based miners like the (now defunct) CoinHive.
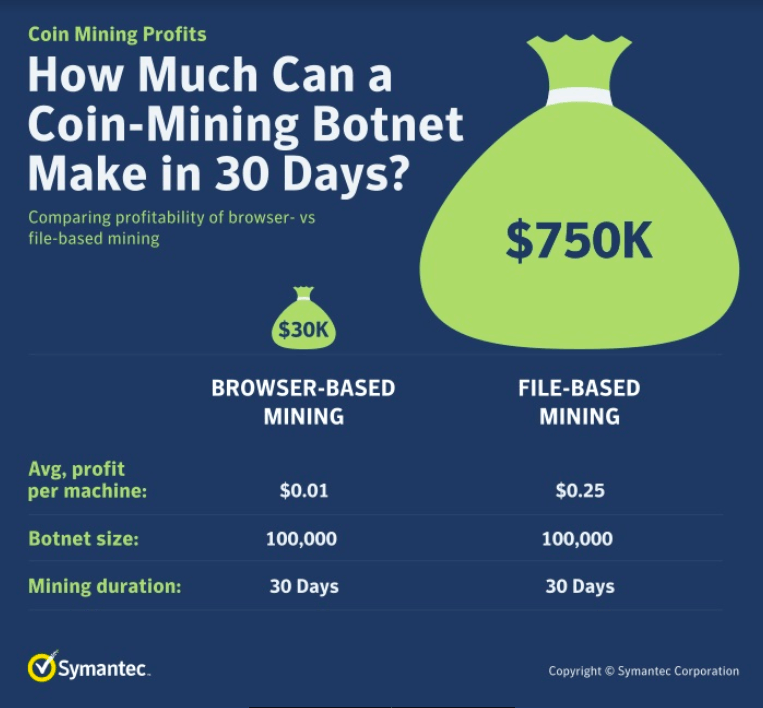
“The Monero cryptocurrency, which is the cryptocurrency most commonly mined during crypto-jacking attacks, dropped in value by 90 percent in 2018, so it may make sense that miners that can create more cryptocurrency faster are now more popular with cyber criminals,” said Symantec.
The firm noted that file-based miners (like the ones featured in Beapy) hold significant advantage over browser-based miners like CoinHive, primarily as they mine cryptocurrency (and return profits to attackers) much faster.
Browser-based mining is out, hacking Asia’s enterprises is in
Symantec warned enterprises they shouldn’t remain complacent to the Beapy threat, and urged them to consider the major impacts Beapy could have on businesses.
The firm highlighted potential Beapy concerns including slowdown in device performance, leading to employee frustration and reduction in activity.
Symantec also mentioned the malware could cause higher IT costs due to hardware degradation, and businesses operating in the cloud could face large bills, especially those services that pay fees based on CPU usage.
“Despite the drop in crypto-jacking activity in 2018, when there was a 52 percent drop in crypto-jacking, this is still an area of interest for cybercriminals,” said the researchers.
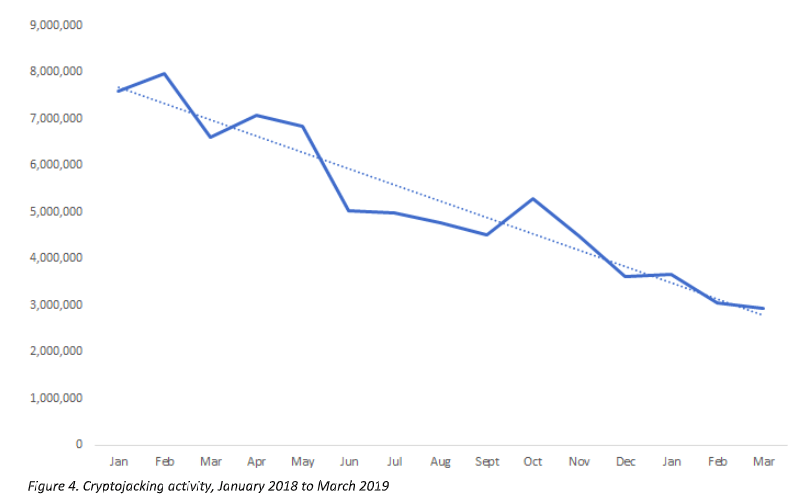
Indeed, Symantec recorded just under 3 million crypto-jacking attempts in March 2019. “While a big drop from the peak of February 2018, when there were 8 million crypto-jacking attempts, it is still a significant figure,” they added.
To mitigate risk, enterprises are urged to ensure their networks are protected by multiple, overlapping, and mutually supportive defensive systems, like endpoint, email, and web gateway protection technologies.
Symantec also advised enterprises educate their employees on the symptoms of crypto-jacking, as well as how to avoid dodgy email attachments like the ones employed by the Beapy malware.
Did you know? Hard Fork has its own stage at TNW2019, our tech conference in Amsterdam. Check it out.
Get the TNW newsletter
Get the most important tech news in your inbox each week.






