
The servers of popular Bitcoin wallet Electrum are under heavy attack, and users are advised to be extra careful when using the platform until it’s resolved.
A sophisticated botnet of more than 140,000 machines has launched Denial-of-Service (DoS) attacks on Electrum’s servers, with apparent intent to direct users to compromised versions of the software designed to steal their Bitcoin.
Bad actors have even deployed their own Electrum servers hosting “backdoored” versions of the Electrum client en masse. If a user successfully syncs their vulnerable Electrum wallet with a malicious server (hundreds detected so far), they’re instructed to “update” their client with a hacked version.
A security researcher familiar with the matter told Hard Fork if these fake versions of Electrum are installed, all funds contained in the old versions are immediately lost.
“The total amount stolen is in the millions of dollars so far, with a single person alone losing almost $140,000, based on our analysis,” they said. “The DoS attacks are a new level, which only began about a week ago. People have seen 25 Gigabits per second worth of traffic being flooded at community run servers.”
Electrum users are warned they could face service interruptions as administrators continue work to mitigate the damage caused by the intense incoming traffic.
“We hope to resolve this in the coming hours or days,” lead Electrum developer Thomas Voegtlin told Hard Fork.
This could be retaliation over new protections for Electrum users
Bitcoin phishing has actually plagued the Electrum community for months. Indeed, Trojan horse electrumstealer and its variants are thought to have already stolen millions of dollars worth of Bitcoin from unsuspecting Electrum users.
Whilst there’s no explicit link connecting this DoS attack and the phishing campaign, the latest attack seems focused entirely on users with out-of-date Electrum clients.
Our source explained that devs modified some key Electrum servers to reduce the odds of exposure to the phishing scam. It is this, they speculated, that has led the attackers to perform such a large-scale DoS attack against Electrum’s servers.
“With the benign servers down due to the attack, there’s a strong likelihood of people connecting to the malicious ones,” they said. “Original versions of the attack used modified Electrum servers, abusing a bug in the Electrum wallet, to send messages telling users that they need to upgrade their software to a malicious version. These were originally tackled by using Google’s SafeBrowsing service to make them inaccessible to possible victims.”
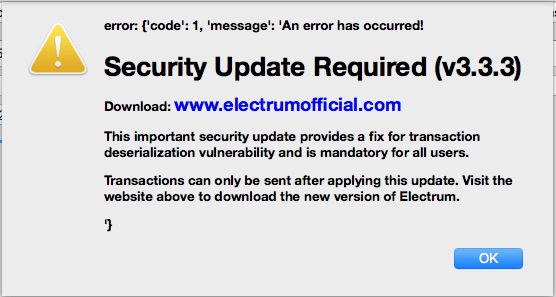
Currently, there are over 200 detected domains that appear to be hosting the Electrum malware – for example “electrumx.network.” Unfortunately, as Google takes its time to update its SafeBrowsing database, blacklisting malicious servers has become ineffective.
Lead dev Voegtlin explained a patch had previously been issued to force out-of-date, vulnerable Electrum wallets offline as soon as a connection to a “legit” server was found (Electrum needs 8-10 connections to fully operate).
“We are not sure what motivates the attacker; it might be some kind of retaliation, after we took steps last month in order to prevent phishing attacks,” he commented. “This counter-attack has been effective against phishing, because it does not require a lot of legit servers; if you randomly connect to 10 servers, the chance that at least one of them is performing the counter-attack is very high.”
“We have not heard of any recent success at the phishing attack, since we deployed the counter-attack,” said Voegtlin.
Long-forgotten Electrum users most at risk
Currently, Electrum has no auto-update mechanism, so it will continue to run old and vulnerable versions until users manually upgrade the client themselves.
With this in mind, Voegtlin emphasised users most at risk are those who downloaded Electrum long ago and have not updated the software since.
“Indeed, updated versions are not at risk, but the service might be temporarily unavailable. If that is the case, we recommend to users that they stick to the same server (disable auto-connect), until they eventually manage to open a session,” he continued.
“Of course the attacker might be trying to take down legit servers in order to keep carrying out their phishing attack, but […] they do not simply need the user to connect to their server,” Voegtlin confirmed. “What they need is a vulnerable client to connect exclusively to their servers, and that is a lot less likely.”
So, to be safe, users are encouraged to strictly download Electrum software from the electrum [dot] org domain and its official GitHub repository.
Installing and updating Electrum clients from only these locations is said to be the main method of protection against these attacks.
A related patch is currently being prepared by its devs. Electrum also urged users to run their own servers, as more (legitimate) public Electrum servers effectively work to dilute attack.
Did you know? Hard Fork has its own stage at TNW2019, our tech conference in Amsterdam. Check it out.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




