Security researcher Egor Homakov has discovered a Twitter vulnerability which allows apps to send DMs without requiring explicit user permission. TNW has verified the findings and can confirm the bug.
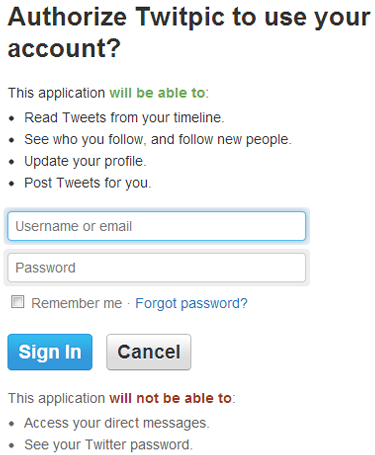
This means Twitter apps that don’t ask for permission to send DMs can do so anyway. For example, Twitpic doesn’t ask for access to your DMs when you connect it to your account:
Nevertheless, by using the command “d twitter_username message” the app can send a DM to anyone you can normally send DMs to. The app never has to check with the user if he or she is okay with sending a DM.
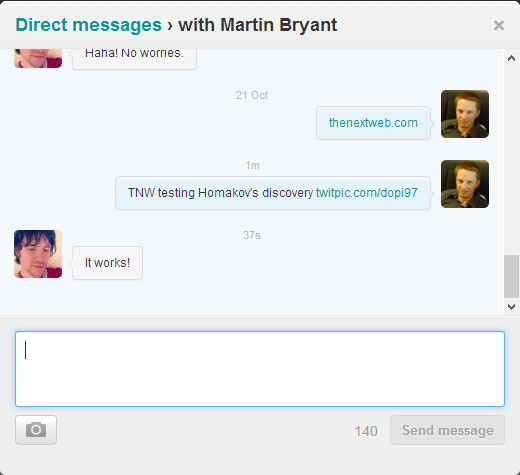
Here is a test message we tried to send:
Here is the immediate result:
It’s worth noting that some apps block this functionality. Buffer, for example, gives the following error: “Sorry, direct messages can’t currently be sent through Buffer.” Other apps we tested, however, sent DMs without a hitch.
Homakov gives three reasons as to why this is a bug:
- Apps are supposed to have read & write permissions to access DMs. With this shortcut, you can bypass that protection.
- DMs are easier to use for spam. Users are less likely to notice them being sent.
- DMs don’t show if messages were sent via the official Twitter client or a third-party OAuth client. As a result, the flaw could be used for phishing.
Per the last point, I knew my test was successful because I had a DM notification: Martin was waiting for the message and responded immediately.
If Twitpic, or any other Twitter app for that matter, had sent a message on my behalf to my Twitter friends, I would not know until one of them responded or I decided to check my DMs on a whim. In other words, there’s a lot of potential for abuse here.
Another vulnerability researcher, DaKnOb, says he found the flaw a year ago and reported it to Twitter. The company allegedly said it wasn’t something that needed fixing:
@homakov I know. I told them. They said it is a Twitter feature and should be left as is
— DaKnOb (@DaKnObCS) December 14, 2013
This flaw may require users to connect a malicious Twitter app to their account, but after that, they are quite vulnerable. The fact it has been known for so long without being addressed is quite worrying.
We have contacted Twitter about this issue. We will update this article if we hear back.
Top Image Credit: Leon Neal/AFP/Getty Images
Get the TNW newsletter
Get the most important tech news in your inbox each week.