The hacking group Syrian Electronic Army (SEA) managed to take out The New York Times on Tuesday by attacking its registrar, Melbourne IT, the newspaper has confirmed. Concurrent attacks from the SEA also targeted Twitter and Huffington Post’s UK site, both of which are also Melbourne IT customers.
Related: This how the Syrian Electronic Army hacked the New York Times and Twitter
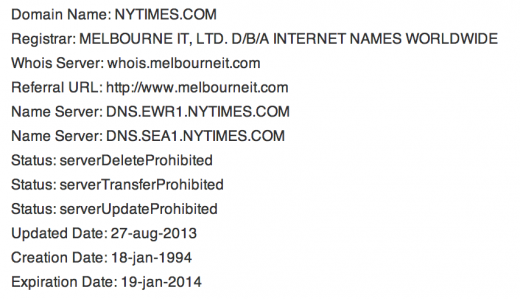
Melbourne IT, which rates itself as a “top 5 global domain name registrar and the #1 digital brand management company worldwide”, took over management of Twitter’s domains in 2009 (PDF). Earlier this year, the company admitted that it had suffered a minor breach from an “unauthorized third party”, but maintained that no damage had been done. A Melbourne IT spokesperson has confirmed that reseller credentials were used to access its systems. Once alerted to the break-in, the company “changed the affected DNS records back to their previous values,” “locked the affected records from any further changes at the .com domain name registry,” and “changed the reseller credentials so no further changes can be made.”
The company is currently investigating its logs for the identity of the intruder.
Update: Melbourne IT has confirmed that the SEA gained log-in details to its system via a phishing attack:
We have now identified that a targeted phishing attack was used to gain access to the credentials of users of a Melbourne IT reseller account. We have obtained a copy of the phishing email and have notified the recipients of the phishing email to update their passwords. We have also temporarily suspended access to affected user accounts until passwords have been changed.
Since Melbourne IT operates as a top-level domain service, it could take as long as a day for SEA’s changes to be cleared from the system. Low-level DNS and ISP services could, however, speed up the process by manual reversing the alterations.
Cory Von Wallenstein, the CTO of Dyn, which provides DNS services for Twitter but was not compromised in today’s incident, explained the attack as follows:
For the affected sites, the attackers gained access to the domain registration accounts that were operated by Melbourne IT, and changed the authoritative DNS servers to ns1.syrianelectronicarmy.com and ns2.syrianelectronicarmy.com. What makes this attack so dangerous is what’s called the TTL… or time to live. Changes of this nature are globally cached on recursive DNS servers for typically 86,400 seconds, or a full day. Unless operators are able to purge caches, it can take an entire day (sometimes longer) for the effects to be reversed.
Twitter has posted the following update about what happened:
At 20:49 UTC, our DNS provider experienced an issue in which it appears DNS records for various organizations were modified, including one of Twitter’s domains used for image serving, twimg.com. Viewing of images and photos was sporadically impacted. By 22:29 UTC, the original domain record for twimg.com was restored. No Twitter user information was affected by this incident.
Photo credit: Ramin Talaie/Getty Images
Get the TNW newsletter
Get the most important tech news in your inbox each week.