A flaw in the design of Twitter.com’s security allowed for user passwords to be sent in plain text when entered on the detail page of a Tweet. That flaw has been addressed by the Twitter security team this evening and is now fixed, though it is unknown how long it went on before today.
While the main Twitter site uses SSL security to prevent plain text from being sent in the open, the tweet detail pages feature a drop-down sign-in menu that was not properly utilizing the HTTPS (secure) protocol. This means that anyone who has entered their Twitter login and password from such a page before tonight has sent that password to Twitter’s servers in plain, easily intercept-able text.
The issue was discovered by avid twitter user and CEO of cloud security company Dome9, Zohar Alon, who contacted us. We informed Twitter of the problem immediately, as did Alon. In order to replicate the issue, you would have to log out of Twitter, click on a link that took you directly to the detail page of a tweet and log in there using the drop down sheet.
While this isn’t the most common way that people log in to Twitter, it is by no means unheard of. I often log in to Twitter using this drop-down sheet after I visit a tweet that I would like to retweet or reply to. This means that I’ve sent my password in plain text hundreds of times.
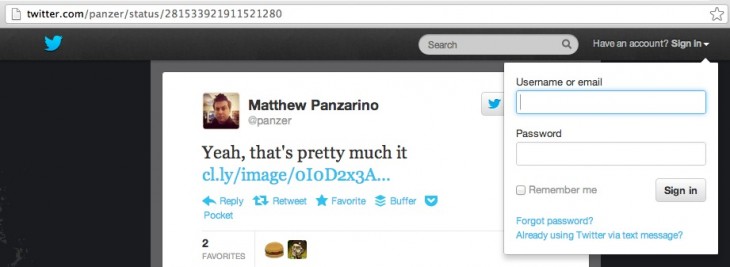
The pages in question are these, which display when you view a single tweet directly on the site. Note the sign in box that appears when you click the option to the right:
While Chrome’s URL bar doesn’t display the whole text of the link, these pages are HTTP, not HTTPS. Unfortunately, the drop-down menu itself was not secured under the HTTPS protocol. This meant that when you clicked that Sign in button, your information got sent in regular old text.
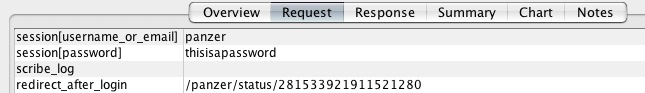
To illustrate, I entered the text ‘thisisapassword’ and used an application that monitors web traffic to see what information was being sent over the network. Here’s what I got back:
If you needed to be told, that is not good news. Your password to any site, even one that has a minimum of security measures, should never be able to be picked up by a network monitoring tool. The potential for abuse is far too large and this is definitely not the level of security that a site with such potential as a gateway to your information should employ.
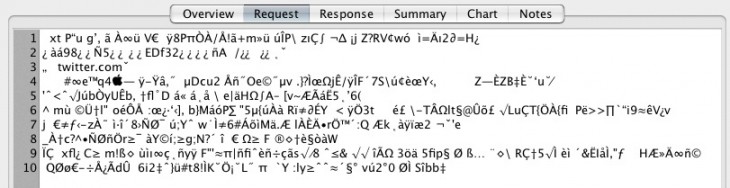
Here’s what the traffic looks like when signing in on the main Twitter.com homepage, which is properly secured:
Gibberish, perfect. To be absolutely clear, the security on the main Twitter.com homepage is set up appropriately. It was specifically the login sheet on the tweet detail pages that was affected by this improper use of HTTP rather than HTTPS traffic.
As the issue was easily replicable and was not — as far as we know — public knowledge, we approached Twitter to give it time to rectify the problem before publishing. A Twitter spokesperson informed us this evening that the company’s security team had “looked at the potential vulnerability and addressed it.” Hopefully that’s the end of it, but the fact that a simple security precaution wasn’t in place on a site with some 200M users is still troubling.
Image Credit: GABRIEL BOUYS/AFP/Getty Images
Get the TNW newsletter
Get the most important tech news in your inbox each week.