For the vast majority of people in 2017, creating a website is simply a matter of combining a number of off-the-shelf components until they end up with something that does what they want it to.
Anyone wanting to create an online shop could just hack together WordPress and Shopify. There are a plethora of affordable plugins and tools that allow you to turn a barebones blog into a fully-featured social network – like Peepso – or a YouTube-style video sharing site.
Now is a great time to have lofty aspirations, but lack any sort of technical prowess whatsoever.
But there’s a big problem with this approach. Whenever you use someone’s code, you’re essentially making a big leap of faith that they know what they’re doing. There’s always a possibility that any plugin or tool you use comes with a serious security vulnerability. That was certainly the case with the popular (and self-explanatory) HTML Comment Box plugin, which is used by around 2 million blogs and websites.
Stored XSS: An Explainer
Karim Rahal, a brilliant 14-year-old security researcher and ethical hacker from Lebanon, discovered the stored XSS (cross-site scripting) vulnerability in the plugin. Before we delve into how he did it, it’s probably a good idea to explain what Stored XSS is.
Many websites let you upload your own text-based content. This could be anything – from an entry in a guestbook, to an insightful comment on a blog post.
Now, what if the text you added was actually a piece of malicious code that got stored and rendered to anyone who visited the website from that point on? That’s called stored XSS.
Most competent web developers know how to filter it. The problem is, there are a myriad of ways in which you can obfuscate XSS attacks so that they slip past any filters, and it’s extremely hard to account for all of them.
That’s essentially how Karim was able to compromise the HTML Comment Box plugin. He embedded a small JavaScript proof-of-concept within an IMG tag, and then concealed that with what’s known as an “Extraneous open brackets” payload. This is a technique he learned from his friend, fellow teenaged security researcher Ibram Marzouk, who discovered a similar vulnerability in PasteCoin a few months earlier.
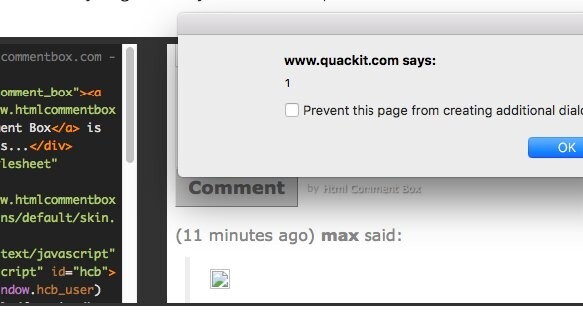
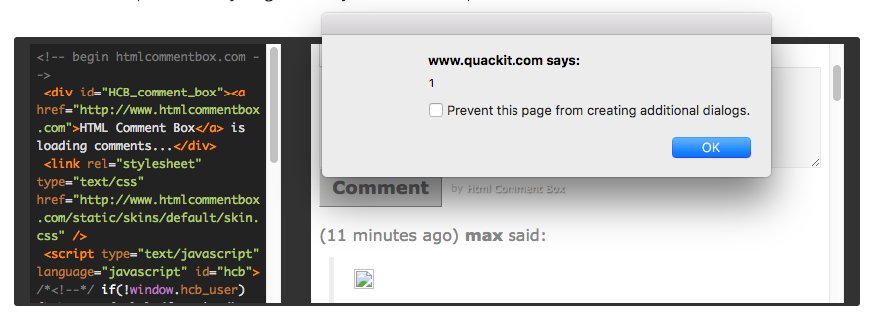
“>><<img src=x onerror=alert(1);//>>
This was the code he used. It doesn’t look like much. Indeed, it doesn’t do much. When executed, it merely forces the browser to create an alert pop-up that says ‘1’. But it was able to bypass all the XSS protections the developers had created.
In the wrong hands, it could be used to spread malware, either through drive-by download attacks, or by redirecting people to malicious websites.
Communicating the vulnerability
Getting in touch with the developers was harder than Karim expected. But thanks to an ongoing relationship he has with Swedish security giant Detectify Labs, they were able to help.
Karim explained: “About two months ago I was invited to Detectify’s Crowdsource program, which is a program where hackers contribute to their scanner with known vulnerabilities and in return they get paid. Through the Detectify Crowdsource program I reported the HTML Comment Box vulnerability stating that I wasn’t able to find the developer’s contact info. After some research from their side, they were able to find the developer’s email address.”

All things said, the developers of HTML Comment Box were pretty sanguine about their cherished plugin getting pwned by someone still in high school. Karim let them know about the vulnerability on November 30, 2016. By December 1, the vendors had created and issued a fix.
Upon reflection, Karim has some pretty strong advice for anyone using any form of CMS system: “If you fully want to be secure then you shouldn’t be using external plugins.” If that’s unavoidable, you should also ensure that auto-update is enabled.
At the very least, this episode is a reminder of the dangers inherent in relying on other people’s code.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




