Security researchers have discovered a bombshell: HTC was storing high-resolution images of your fingerprints directly on your Android phone with little protection.
In a white paper released by FireEye researchers last week, the group outlined how simple it was to recover the image files from an HTC phone, the One Max.
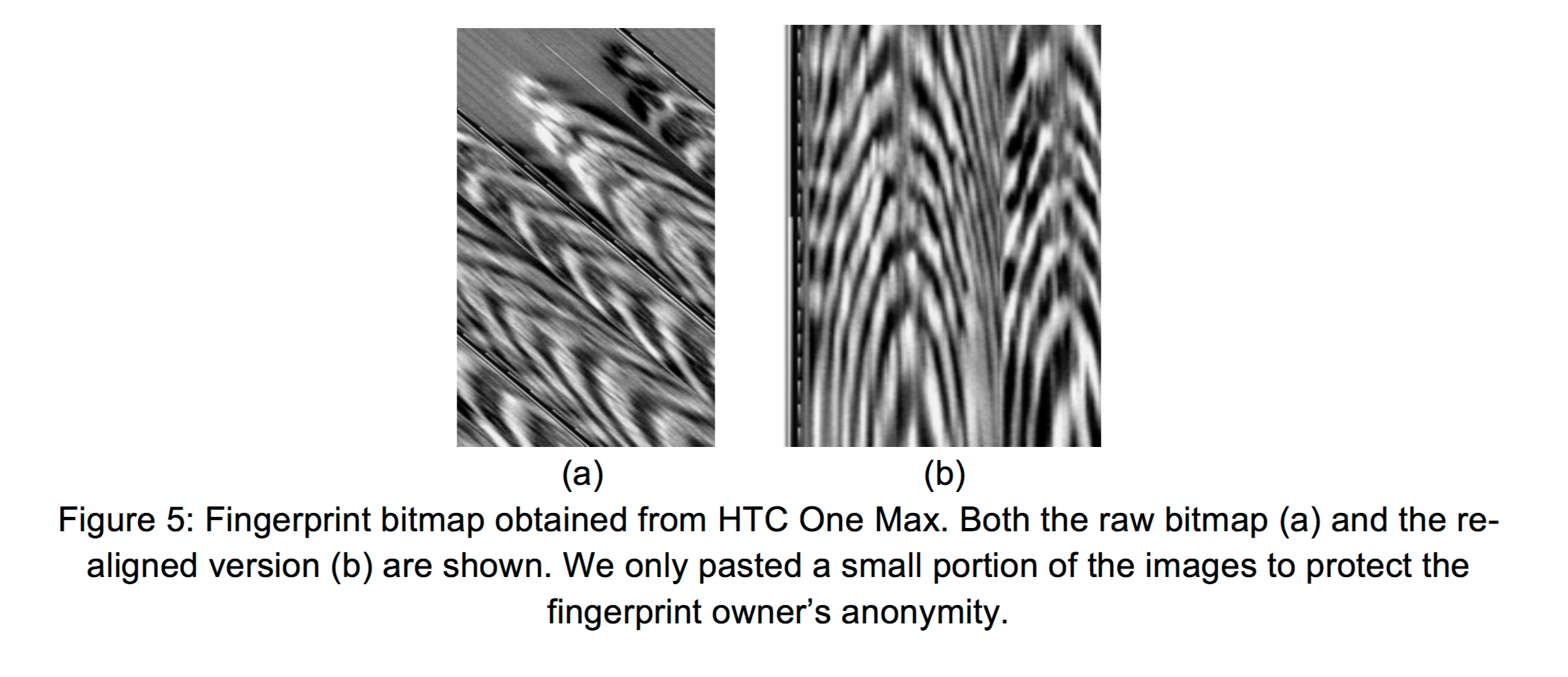
In the case of the One Max, HTC saved images of configured fingerprints directly to phone storage at /data/dbgraw.bmp with ‘world-readable’ permissions, meaning any app could steal the user’s fingerprints.
Even worse, every time the fingerprint sensor was swiped the image was updated, so a malicious process could steal multiple images without detection.
The bug was fixed by HTC after FireEye notified the company of how dangerous it was.
The group also identified another attack that affects other Android phones where malware can circumvent protections in the operating system to access the fingerprint hardware directly.
Apple uses a “secure enclave” to store fingerprint data, but never saves the actual image so it’s not possible to retrieve a scan of the fingerprint, though a group did successfully break into an iPhone using a silicon representation of a stolen fingerprint.
Today’s news shows that many phone vendors don’t go out of their way with the security of your biometrics and it’s hard to know exactly what they’re doing with your fingerprint data or if it’s being secured correctly.
Image credit: Shutterstock
Get the TNW newsletter
Get the most important tech news in your inbox each week.