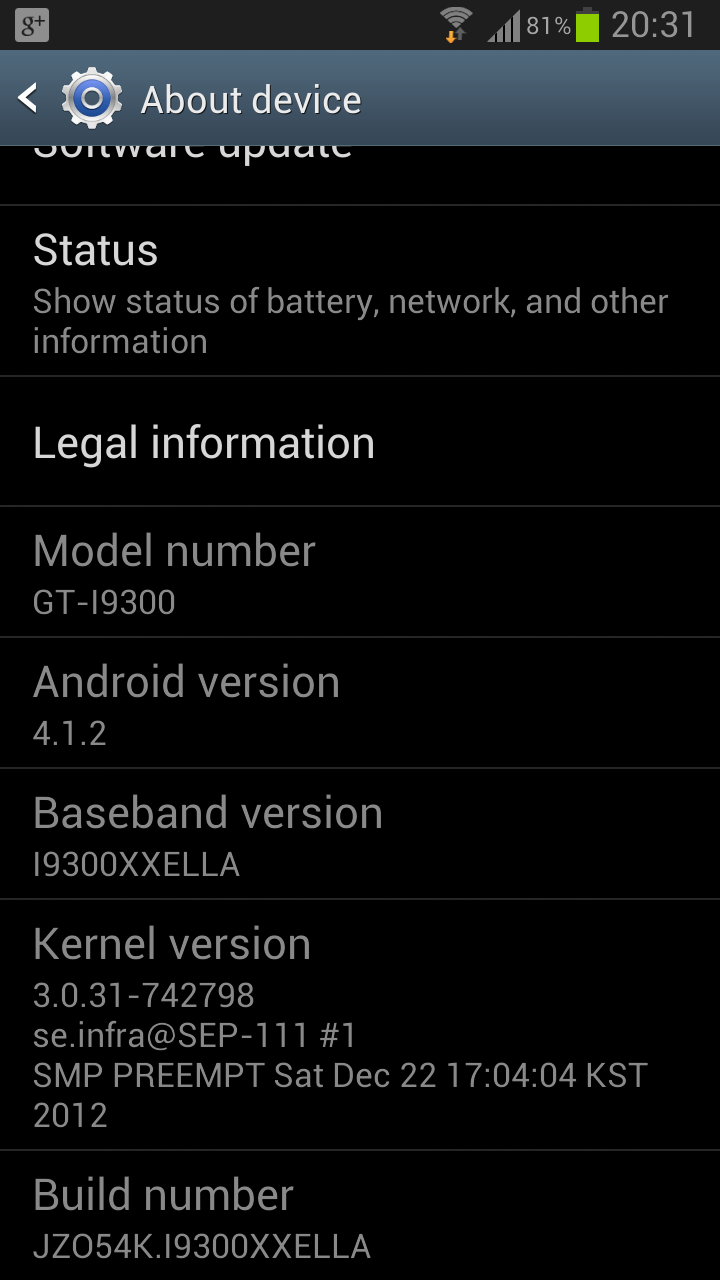
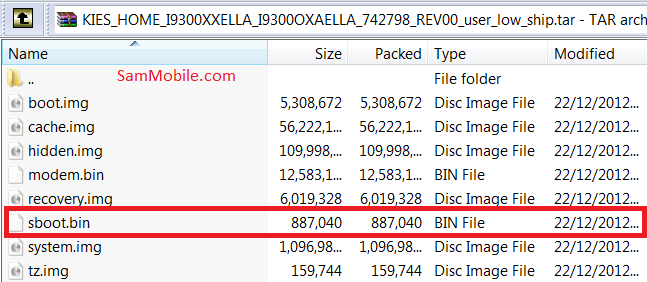
Samsung has finally begun rolling out a patch to fix the Exynos vulnerability that leaves a range of its smartphones open to being hacked. SamMobile noticed that the update has made its way to owners of the Galaxy S3 in the UK, but it is not yet available in other markets.
The security issue, leaves physical memory on any device powered by a specific Samsung Exynos processor open to hacking, was first discovered on December 16. Samsung acknowledged the issue when it responded three days later saying it was working “as quickly as possible” to patch the vulnerability. Now, just over two weeks later, the rollout has quietly begun.
SamMobile speculates that the software update also fixes the ‘sudden death’ issue that was randomly bricking some Galaxy S3 devices. While Samsung did acknowledge it was working to fix this second issue, it is not confirmed since the company officially communicated the update and details of the changelog are not yet available. Reports claim there are other minor fixes addressed in the update.
Galaxy S2 owners can get the patch by updating their device to the latest firmware via Kies or over-the-air. The Samsung-dedicated blog posted a number of screenshots that show the update has arrived in the UK.
We’ve reached to Samsung to ascertain more information about the update, and find out when it will be available to device owners in the rest of the world.
Third party security firms were quick to release patches of their own — including one from TrustGo — but, given that many users are unlikely to be unaware of the issue in the first instance, let alone where to find a reliable patch, Samsung’s own fix — which is pushed to devices — is the most critical update.
The flaw isn’t limited to the Galaxy S3. The vulnerability was first highlighted on XDA Developers, where the exploit was tested on the flagship Samsung phone, which then rooted the device. The flaw also exists on the Samsung Galaxy S II, the Samsung Galaxy Note II, the Meizu MX, and potentially other devices that feature an Exynos processor (4210 and 4412) and use Samsung kernel sources.
Other affected devices are said to include: Samsung Galaxy S2 GT-I9100, Samsung Galaxy S3 GT-I9300, Samsung Galaxy S3 LTE GT-I9305, Samsung Galaxy Note GT-N7000, Samsung Galaxy Note 2 GT-N7100, Verizon Galaxy Note 2 SCH-I605 (with locked bootloaders), Samsung Galaxy Note 10.1 GT-N8000, and the Samsung Galaxy Note 10.1 GT-N8010.
Image Credit: retrocactus/Flickr
Get the TNW newsletter
Get the most important tech news in your inbox each week.