O2 may also be unwittingly assisting spammers, allowing them to match email addresses with phone numbers. See below for more updates.
If you reside in the UK and you are one of the millions of subscribers to mobile operator O2, you may be alarmed to learn that the carrier is sending your mobile number to every website you visit on your mobile phone.
The issue was brought to our attention to Lewis Peckover, who created a simple webpage to check the information that a mobile browser would send to a website when it requested data.
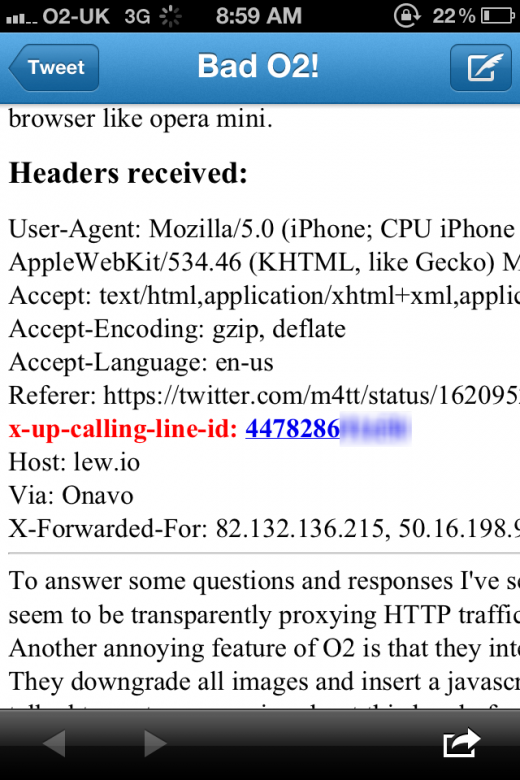
Whilst most of the data was to be expected, including the Host, User Agent, Referrer and Encoding, there was also another field in the results — x-up-calling-line-id.
What is x-up-calling-line-id? Your mobile phone number.
We tested it on an O2-connected mobile device and received the following results (number blurred for privacy):
O2 appears to be aware of the issue and is replying to irate customers via its Twitter account:
@sevitz we’re checking with internal teams, and will come back with more as soon as we can
— O2 in the UK (@O2) January 25, 2012
In our tests we have confirmed that Orange, T-Mobile, Three and Vodafone do not send mobile numbers in header information. If you are on GiffGaff (an O2-owned company) or Tesco Mobile (which uses O2’s networks), you will be sending your mobile number to websites also.
You also need to be connected to its network, not a Wi-Fi connection.
Last night, O2 replied to Lewis Peckover on Twitter, detailing why it sent the data to websites:
@lewispeckover Hi Lewis. The mobile number in the HTML is linked to how the site determines that your browsing from a mobile device #O2Guru
— O2 in the UK (@O2) January 24, 2012
However, Think Broadband offers this explantion:
Our suspicion is that the feature is used by internal O2 websites to identify the user trying to make changes to the account, but that one or more of O2’s proxy servers have been misconfigured.
Whereas commenters on Hacker News believe O2 has mistakenly opened its data to third-party websites:
x-up-calling-line-id (and similar headers from other gateway vendors) are typically not meant to be sent in the clear beyond internal sites. Perhaps a certain set/class of URL ACLs were (mis)configured during a maintenance window that caused this to happen.
Similar to how websites leave cookies, carriers have always had the ability to send certain identifying information to external sites. Usually, such identifying information is munged in some way that doesn’t make it possible to determine the mobile number of the subscriber.
The funny thing is that people are often surprisingly willing to provide their phone number on more and more sites, which then makes it trivial for such services to link the anonymized identifier with the actual mobile number.
We have reached out to O2 to enquire as to why the network would send customer mobile numbers in website header information, we will update the article should we receive a response.
Update: Pocket-lint shares a way to stop sharing your number with websites:
If you want to remove your phone number, and switch to the O2 proxy bypass APN until the firm fixes this leak, you need to enter the following in to your APN settings:
APN: mobile.o2.co.uk
Username: bypass
Password: password
Update 2: Consumer campaigning society Which? contacted the Information Commissioner’s Office (ICO) about the issue, it was sent this statement:
‘Keeping people’s personal information secure is a fundamental principle that sits at the heart of the Data Protection Act and the Privacy and Electronic Communications Regulations. When people visit a website via their mobile phone they would not expect their number to be made available to that website.
‘We will now speak to O2 to remind them of their data breach notification obligations, and to better understand what has happened, before we decide how to proceed.’
Get the TNW newsletter
Get the most important tech news in your inbox each week.