For people of a certain age, owning a Myspace account was an essential rite of passage. Countless teenage years were spent carefully customizing the CSS on profiles, ranking friends into top eight lists, and picking out the most perfectly angsty pop-punk track to autoplay.
Ten years later, Myspace is a relic of the past. It’s forgotten, but not quite gone, existing in a moribund state. Although nobody updates their profiles anymore, they’re still there, ignored and unloved.
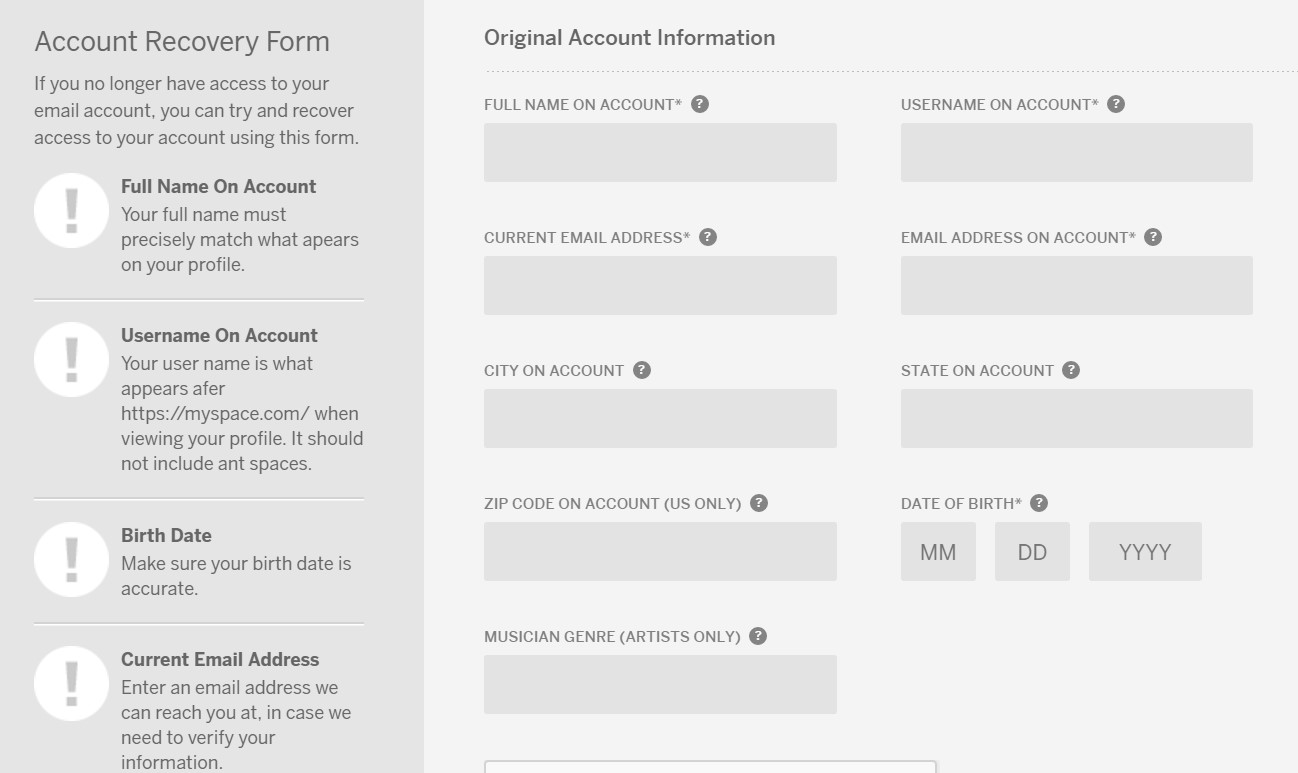
Myspace, perhaps conscious of the fact that many people have since lost access to the email accounts associated with their profiles, offers a tool that lets you recover them. You simply have to verify your identity by providing a few pieces of information.
Unfortunately, according to information shared exclusively with TNW by security researcher Leigh-Anne Galloway, this process is deeply flawed, and makes it trivially easy for a bad actor to gain unauthorized access to any account.
When you recover a long-lost Myspace account, you’re asked to provide information about the account. Myspace says that the more information you provide, the greater chance you’re able to get back in.
This is an automated process. Once you’ve successfully gained access to an account, you’re prompted to change the password before heading to your profile.
So, what do you need to get into the account? It turns out, not much. While Myspace prompts you for a current email address, as well as the email address registered with the account, it doesn’t validate this.
It validates just three pieces of information: name, username, and date of birth.
Names are found on the profile itself, and you can discern the username from the URL (so, for myspace.com/thenextweb, thenextweb is the username). The only tricky part is the date-of-birth, although you can figure that by sleuthing on other social networking sites.
Once you have obtained those three pieces of information, you can essentially break into any Myspace account.
It’s bad. Galloway, who works as a Cyber Security Resilience Lead at Positive Technologies, described this process as “so flawed it deserves a place in history.” I’m inclined to agree with her.
Following responsible disclosure best practices, Galloway informed Myspace of the vulnerability in April of this month. The company sent an automated reply, but has otherwise failed to act.
This inaction forced Galloway to take action into her hands, and she has publicly disclosed the vulnerability while it still exists. In a damning blog post, she said Myspace is “an example of the kind of sloppy security many sites suffer from,” citing “poor implementation of controls, lack of user input validation, and zero accountability.”
She also encouraged anyone with the ability to delete their account to do so, saying “whilst Myspace is no longer the number one social media site, they have a duty of care to users past and present.”
Myspace has a checkered record when it comes to security. Last year, the company confirmed the leakage of 360 million user accounts. Researchers believe this is one of the largest data breaches of all time.
We’ve reached out to Myspace for comment. If we hear back from them, we’ll update this post.
Update: Myspace got in touch. In a statement, the company said:
“In response to some recent concerns raised regarding Myspace user account reactivation, we have enhanced our process by adding an additional verification step to avoid improper access. We take data security very seriously at Myspace. We plan to continue to refine and improve this process over time.”
Get the TNW newsletter
Get the most important tech news in your inbox each week.




