WhatsApp and Telegram have both billed themselves as secure alternatives to phone, text or email correspondence. For the most part, that’s true, the two are end-to-end (e2e) encrypted by default and because of this, your conversations are much harder to monitor by outsiders.
But, sometimes it’s not the application that leads to security vulnerabilities, it’s something else entirely. In this case, that “something else” is Signaling System 7 (SS7), a global network of carriers that acts as a central hub to connect the world — we’ve talked about it before.
SS7 vulnerabilities aren’t a secret. We’ve known about them for years, as have governments around the world, telecoms and yes, hackers. The problem is, the vulnerability isn’t a simple one to fix, but more on that later.
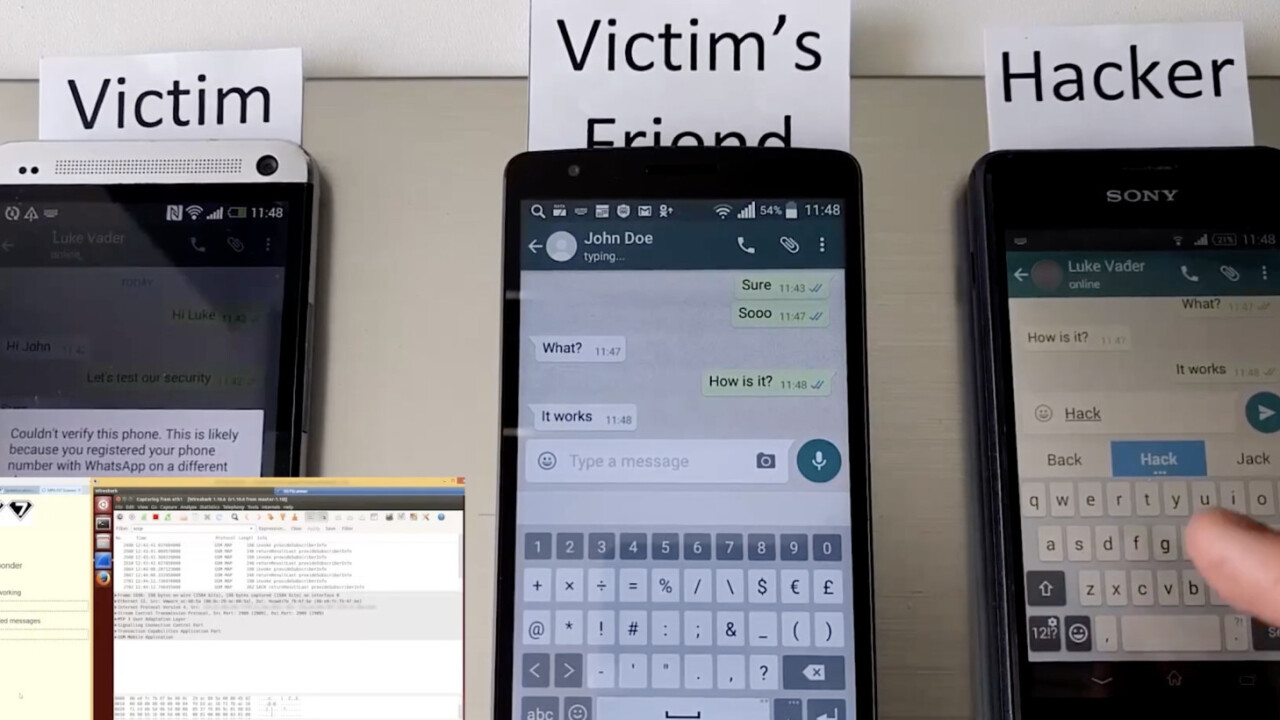
For now, check out the hack in action.
What’s happening here?
Typically, encrypted messaging apps are impervious to hackers because the key to decrypt the message relies on each end of the conversation (you and your friend). Intercepting the message in the middle — known as a man-in-the-middle attack — is still possible, but the attacker would gain nothing but a message they couldn’t read, or decrypt.
These two hacks aren’t attacking the encryption in the app(s), however, they’re attacking the SS7 vulnerability. This is done by tricking the telecom network into believing the attacker’s phone has the same number as the target’s. I won’t detail how that’s done, but let’s just say it’s not difficult. From there, the attacker would create a new WhatsApp or Telegram account and receive the secret code that authenticates their phone as the legitimate account holder.
Once complete, the attacker now controls the account, including the ability to send and receive messages. This is particularly troublesome as — now that their phone is authenticated — they are the original account holder, meaning they’ll now be able to send messages as you, and read messages intended for you without ever having to try to break strong encryption protocols.
Why can’t we just fix SS7?
SS7 is a global network of telecom companies, which means none of them actually own, or govern it. Instead, any change is met with miles of red tape and a lack of decent options aside from global compliance to actually get things done. It’s a mess, and it’ll remain that way until someone, or a group, is appointed to govern and maintain it.
Until then, the vulnerability will remain.
There’s an alternate theory as well that says intelligence agencies are the wall standing between the vulnerability and telecoms’ ability to fix it.
We’ll never be able to say for sure, but the ability to clone phones and communicate over encrypted channels is certainly an appealing option for the CIA, NSA and others who’ve stuck their hands in the anti-privacy cookie jar once or twice before.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




