As the world grows increasingly security conscious, Web users are placing their trust in strong encryption, two factor authentication and bulletproof passwords that can’t be brute forced in a single lifetime, or several lifetimes for that matter.
Thing is, all the cryptology in the world can’t save humans from, well, humans.
Amazon has proven especially terrible at coming to this realization.
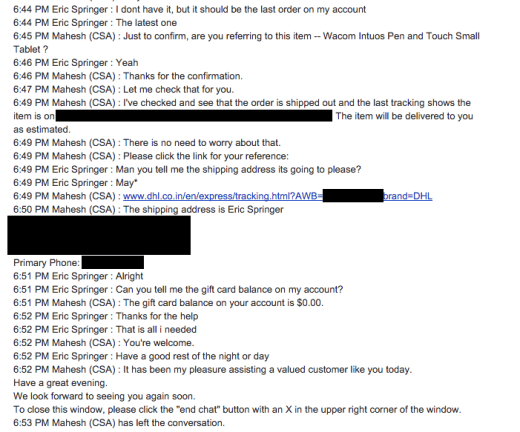
The above transcript of a chat sessions comes from an Amazon user, Eric Springer, who had his account social engineered not once, but three times.
In the first hack, Amazon unwittingly exposed sensitive details to someone presumably not named Eric Springer. This unnamed third party then used this customer data to gain more information from other services Springer used regularly, until he or she ultimately had enough information to convince Springer’s bank to send him a new credit card.
The hacker started the journey with nothing more than Springer’s email address and a fake mailing address from a Whois record on a privately registered domain in which Whois guard (an anonymization service) had lapsed.
From there, the hacker tricked the Amazon support representative into providing the actual mailing address, gift card balances, previous order details and even tracking information for a scheduled delivery.
After a bit of back and forth, Amazon apologized and told Springer that it would make an internal note that the account was likely to be targeted again.
But it happened again, and then once more, for good measure. The last of the three, thankfully, the representative didn’t give out the credit card data the hacker sought.

If you think this was the first time Amazon had failed to secure an account from social engineers, you’d be wrong.
Wired journalist Mat Honan lost his account to hackers in 2012. Worse, in Honan’s case, the hackers used the information Amazon compromised to secure his Twitter account, secure and delete his Gmail address and then further hack their way into his AppleID to remotely wipe his iPhone, iPad and Macbook.
These two aren’t alone. A perusal through any hacking forum or IRC channel details similar exploits from children as young as 13.
What’s particularly worrisome isn’t necessarily a compromised Amazon account, it’s how daisy-chained all of our online information is. Meaning, once a hacker obtains one piece of user data, they can often use it to secure more.
Eventually, they own it all, and in Springer’s case, they’ll often use this data to take their online exploits offline.
Technology can save us all, but only if the user on either end of the keyboard understands the importance of what they’re securing. It’s clear in this case, Amazon doesn’t.
Amazon, as of this writing, hasn’t responded to a TNW request for comment. We’ll update if needed.
➤ Amazon’s customer service backdoor [Medium]
Get the TNW newsletter
Get the most important tech news in your inbox each week.